Low-Computational Extended Orthogonal Matched Filter Structure for Multiuser Detection
Abstract
:1. Introduction
2. Principle of the EOMF
2.1. Formulation of an EOMF
2.2. Computational Complexity of an EOMF
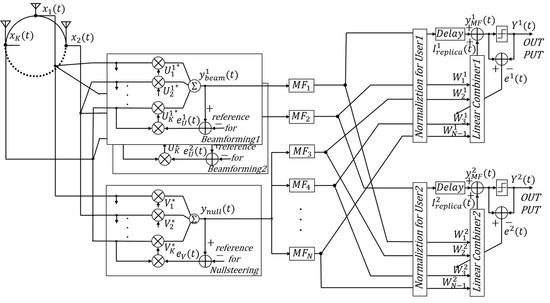
3. Proposed EOMF Structure
3.1. Approach to an EOMF with Multiuser Detection
3.2. Structure of an EOMF with Multiuser Detection
3.3. Computational Complexity of the Proposed EOMF Structure
4. Performance Evaluation and Discussion
4.1. Purpose of Computer Simulation
4.2. Results and Discussion
4.2.1. MUDT
4.2.2. CQET
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Ding, J.; Nemati, M.; Ranaweera, C.; Choi, J. IoT connectivity technologies and applications: A survey. IEEE Access 2020, 8, 67646–67673. [Google Scholar] [CrossRef]
- Alsamhi, S.H.; Ma, O.; Ansari, M.S.; Almalki, F.A. Survey on collaborative smart drones and internet of things for improving smartness of smart cities. IEEE Access 2019, 7, 128125–128152. [Google Scholar] [CrossRef]
- Wu, J.; Jiang, W.; Mei, Y.; Zhou, Y.; Wang, T. A Survey on the progress of testing techniques and methods for wireless sensor networks. IEEE Access 2019, 7, 4302–4316. [Google Scholar] [CrossRef]
- Alameri, I.A. MANETS and internet of things: The development of a data routing algorithm. Eng. Technol. Appl. Sci. Res. 2018, 8, 2604–2608. [Google Scholar]
- Reina, D.G.; Toral, S.L.; Barrero, F.; Bessis, N.; Asimakopoulou, E. The role of Ad Hoc Networks in the internet of things: A case scenario for smart environments. In Internet of Things and Inter-Cooperative Computational Technologies for Collective Intelligence; Studies in Computational Intelligence; Bessis, N., Xhafa, F., Varvarigou, D., Hill, R., Li, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; Volume 460, pp. 89–113. [Google Scholar]
- Alnumay, W.; Ghosh, U.; Chatterjee, P.A. Trust-based predictive model for mobile Ad Hoc Network in internet of things. Sensors 2019, 19, 1467. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Gupta, L.; Jain, R.; Vaszkun, G. Survey of important issues in UAV communication networks. IEEE Commun. Surv. Tutor. 2016, 18, 1123–1152. [Google Scholar] [CrossRef] [Green Version]
- Hadded, M.; Muhlethaler, P.; Laouiti, A.; Zagrouba, R.; Saidane, L.A. TDMA-based MAC protocols for vehicular Ad Hoc Networks: A survey, qualitative analysis, and open research issues. IEEE Commun. Surv. Tutor. 2015, 17, 2461–2492. [Google Scholar] [CrossRef] [Green Version]
- Kim, C.; Cho, Y. Performance of a wireless MC-CDMA system with an antenna array in a fading channel: Reverse link. IEEE Trans. Commun. 2000, 48, 1257–1261. [Google Scholar]
- Sanada, Y.; Padilla, M.; Araki, K. Performance of adaptive array antenna with multicarrier DS/CDMA in a mobile fading environment. IEICE Trans. Commun. 1998, E81-B(7), 1392–1399. [Google Scholar]
- Ahn, C.J.; Sasase, I. Code orthogonalizing filter based adaptive array antenna using common correlation matrix of time domain signals for multicarrier DS/CDMA systems. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2002, E85-A(7), 1604–1611. [Google Scholar]
- Sakakibara, S.; Ohno, K.; Itami, M. Performance evaluation of DS-CDMA IVC scheme and CSMA/OFDM IVC scheme. In Proceedings of the 13th International Conference on ITS Telecommunications (ITST), Tampere, Finland, 5–7 November 2013. [Google Scholar]
- Hachisuka, M. Interference Cancellation Using Layered Structure of Orthogonal Matched Filter for Inter-Vehicle Communication and Ranging. Master’s Thesis, Yokohama National University, Yokohama, Japan, 2014. [Google Scholar]
- Kobayashi, T.; Suzuki, M.; Sugimoto, C.; Kohno, R. Space temporal interference cancellation using TDL array antenna and waveform based OMF for IR-UWB systems. ICT Express 2015, 1, 71–75. [Google Scholar] [CrossRef] [Green Version]
- Kobayashi, T.; Sugimoto, C.; Kohno, R. Interference cancellation for intra and inter UWB systems using modified hermite polynomials based orthogonal matched filter. IEICE Trans. Commun. 2016, E99-B(3), 569–577. [Google Scholar] [CrossRef]
- Kobayashi, T.; Sugimoto, C.; Kohno, R. Theoretical analysis of interference canceler using modified hermite polynomials based orthogonal matched filter for IR-UWB systems in AWGN and interference channel. In Proceedings of the 20th International Symposium on Wireless Personal Multimedia Communications (WPMC), Bali, Indonesia, 17–20 December 2017. [Google Scholar]
- Suzuki, K.; Kohno, R. Time-space interference cancellation system using OMF. In Proceedings of the 38th Symposium on Information Theory and Its Applications (SITA2015), Okayama, Japan, 24–27 November 2015. [Google Scholar]
- Harada, S.; Takabayashi, K.; Kobayashi, T.; Sakakibara, K.; Kohno, R. Theoretical analysis of interference cancellation system utilizing an orthogonal matched filter and adaptive array antenna for MANET. J. Sens. Actuator Netw. 2019, 8, 48. [Google Scholar] [CrossRef] [Green Version]
- Chandekar, A.A.; Pawar, M. Delay and power optimized adaptive filter using distributed arithmetic. In Proceedings of the International conference of Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 20–22 April 2017. [Google Scholar]
- Tan, L.; Wu, M. Data reduction in wireless sensor networks: A hierarchical LMS prediction approach. IEEE Sens. J. 2016, 16, 1708–1715. [Google Scholar] [CrossRef]
- Shu, T.; Chen, J.; Bhargava, V.K.; de Silva, C.W. An energy-efficient dual prediction scheme using LMS filter and LSTM in wireless sensor networks for environment monitoring. IEEE Internet Things J. 2019, 6, 6736–6747. [Google Scholar] [CrossRef]








| Computation | Computational Complexity |
|---|---|
| (a) | |
| (b) | |
| (c) | |
| (d) | |
| (e) |
| Computation | Computational Complexity |
|---|---|
| (f) | |
| (g) | 1 |
| (h) |
| Parameter | Detail |
|---|---|
| Channel Model | Additive white Gaussian noise channel |
| Modulation | BPSK and DSSS |
| Spreading sequence | Gold sequence |
| Spreading factor | 31 |
| Carrier frequency | 760 (MHz) |
| Transmit power | 1 (desired users 1 and 2), DIR −30 (dB) equally divided (interference users) |
| Energy per bit to noise power spectral density ratio, | 60 (dB) |
| Number of interference users | 30 |
| Number of antenna elements | 8 |
| Direction of arrival | 0 (degrees) (desired user 1), 180 (degrees) (desired user 2), equidistant to 180 (degrees) (interference users) |
| Information data length | 30,000 (bits) |
| Step size of NLMS algorithm | 0.01 |
| Array antenna weight vector | Winner solution |
| Synchronization, normalization | Ideal |
| Parameter | Detail |
|---|---|
| Channel Model | AWGN |
| Modulation | BPSK and DSSS |
| Spreading sequence | Gold sequence |
| Spreading factor | 31 |
| Carrier frequency | 760 (MHz) |
| Transmit power | 1 (desired user 1), Randomly distributed according to DIR (other users) |
| 15 (dB) | |
| Number of total users | 8, 30 |
| Number of antenna elements | 8 |
| Number of desired users | 1 (Conventional EOMF), 2, Half the total number of users |
| Direction of arrival | 0 (degrees) (desired user 1), scenario 1, 2 (other users) |
| Information data length | 10,000 (bits) |
| Step size of NLMS algorithm | 0.01 |
| Number of weight updates | 10,000 (array antenna, linear combiner) |
| Synchronization, normalization | Ideal |
| Number of Desired Users | BER (10−3) |
|---|---|
| 1 (Conventional EOMF) | 1.16 |
| 2 (Proposed structure) | 2.59 |
| 4 (Proposed structure) | 3.41 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Takabayashi, K.; Harada, S.; Kobayashi, T.; Sakakibara, K.; Kohno, R. Low-Computational Extended Orthogonal Matched Filter Structure for Multiuser Detection. Telecom 2020, 1, 32-47. https://doi.org/10.3390/telecom1010004
Takabayashi K, Harada S, Kobayashi T, Sakakibara K, Kohno R. Low-Computational Extended Orthogonal Matched Filter Structure for Multiuser Detection. Telecom. 2020; 1(1):32-47. https://doi.org/10.3390/telecom1010004
Chicago/Turabian StyleTakabayashi, Kento, Shuhei Harada, Takumi Kobayashi, Katsumi Sakakibara, and Ryuji Kohno. 2020. "Low-Computational Extended Orthogonal Matched Filter Structure for Multiuser Detection" Telecom 1, no. 1: 32-47. https://doi.org/10.3390/telecom1010004