Image Encryption Algorithm Based on Plane-Level Image Filtering and Discrete Logarithmic Transform
Abstract
:1. Introduction
- (1)
- The secret key design of some algorithms is not reasonable, resulting in the need to change the secret key every time a different image is encrypted. Such a design is not practical when there are a large number of images to be encrypted.
- (2)
- Inappropriate use of the plain image hash value. This makes it necessary to repeatedly generate chaotic sequences when encrypting different images.
- (3)
- Some algorithms only make simple use of modular addition or XOR operations, making them vulnerable to differential attacks.
- (4)
- Bit-level or pixel-by-pixel encryption operations make some algorithms inefficient at encrypting images.
- (1)
- A standardized and reasonable secret key design is adopted, and there is no need to change the secret key when encrypting different images.
- (2)
- The hash value is used to truncate chaotic sequences and to determine the generator of the finite multiplicative group . This allows the chaotic sequences to be generated in advance and reused once the secret key is determined.
- (3)
- A discrete logarithmic transformation based on is employed, thereby rendering common differential attack strategies ineffective.
- (4)
- The plane-level permutation, plane-level image filtering, and three-dimensional (3D) chaotic image superposition make the encryption efficiency extremely high while ensuring security.
- (5)
- The random pixel swapping performed at the end makes it impossible for attackers to isolate the diffusion operation through special plain images.
2. Preliminaries
2.1. Chaotic Systems
2.2. SHA-256 Hash Value
2.3. Discrete Logarithm
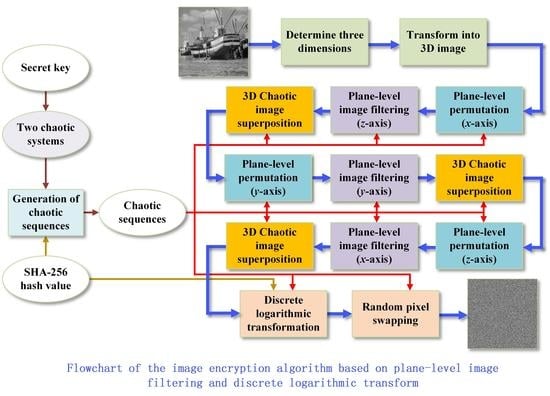
3. Proposed Encryption Algorithm
3.1. Determination of Three Dimensions
- Step 1: Determine the total number of the pixels in P. If is not a power of 2 or less than 8, fill P with the pixels whose values are zeros, until is a power of 2 and not less than 8. Otherwise, go to the next step.
- Step 2: According to , calculatewhere represents the round down operation on an operand.
- Step 3: Determine the size of the first dimension, let .
- Step 4: For the size of the second dimension, let .
- Step 5: According to , , and , calculate the sizeof the third dimension.
- Step 6: Reshape P into with the size of .
3.2. Generation of Chaotic Sequences
3.3. Plane-Level Permutation
3.4. Plane-Level Image Filtering
3.5. 3D Chaotic Image Superposition
3.6. Discrete Logarithmic Transformation
- Step 1: Initialize the 3D intermediate cipher image of size , which is used to save the transformation result.
- Step 2: Set the index of the first dimension to 1.
- Step 3: Set the index of the second dimension to 1.
- Step 4: Let .
- Step 5: For to , repeat Step 4.
- Step 6: For to , repeat Step 3 to Step 5.
3.7. Random Pixel Swapping
- Step 1: The 3D intermediate cipher image of size is reshaped into the 2D final cipher image C of size .
- Step 2: The 1D chaotic sequence of length is reshaped into the 2D chaotic matrix of size .
- Step 3: Convert into the random coordinate matrices and as follows.where holds the row numbers of the coordinates, and holds the column numbers of the coordinates.
- Step 4: Set the row index to 1.
- Step 5: Set the column index to 1.
- Step 6: Swap with .
- Step 7: For to N, repeat Step 6.
- Step 8: For to M, repeat Step 5 to Step 7.
3.8. Discussion
- (1)
- The hash value of the plain image is used to truncate the chaotic sequences and determine the generator of the finite multiplicative group, which makes the equivalent key stream depend not only on the secret key but also on the plain image, thus helping to resist plaintext attacks.
- (2)
- Three rounds of plane-level permutation, plane-level image filtering, and 3D chaotic image superposition can realize good confusion and diffusion properties.
- (3)
- IEA-IF-DLT alternately uses modular addition and XOR operations to superimpose chaotic images, and the mathematical relationship between plain and cipher pixels becomes more complex, which helps to resist common plaintext attacks.
- (4)
- The discrete logarithmic operation is a complex nonlinear operation, which is different from the modular addition and XOR operations commonly used. Therefore, the discrete logarithmic transformation of the intermediate cipher image can enhance the ability of IEA-IF-DLT to resist plaintext attacks.
- (5)
- For the attackers’ strategy of exploiting the special plain images of single pixel values to conduct differential attacks, the random pixel swapping added at the end of IEA-IF-DLT can effectively protect the previous encryption steps from being simplified or isolated.
4. Simulation Tests and Analyses
4.1. Visual Effect Test
4.2. Key Space Analysis
4.3. Key Sensitivity Analysis
4.4. Differential Attack Analysis
4.5. Histogram Analysis
4.6. Correlation Analysis
4.7. Information Entropy Analysis
4.8. Robustness Analysis
4.9. Efficiency Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ghadirli, H.M.; Nodehi, A.; Enayatifar, R. An overview of encryption algorithms in color images. Signal Process. 2019, 164, 163–185. [Google Scholar] [CrossRef]
- Zhang, Y.; He, Q.; Xiang, Y.; Zhang, L.Y.; Liu, B.; Chen, J.; Xie, Y. Low-Cost and Confidentiality-Preserving Data Acquisition for Internet of Multimedia Things. IEEE Internet Things J. 2018, 5, 3442–3451. [Google Scholar] [CrossRef]
- Li, C.; Zhang, Y.; Xie, E.Y. When an attacker meets a cipher-image in 2018: A Year in Review. J. Inf. Secur. Appl. 2019, 48, 102361. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Y.; He, Q.; Chen, G.; Zhang, X.; Xiang, Y. A Low-Overhead, Confidentiality-Assured, and Authenticated Data Acquisition Framework for IoT. IEEE Trans. Ind. Inform. 2020, 16, 7566–7578. [Google Scholar] [CrossRef]
- Özkaynak, F. Brief review on application of nonlinear dynamics in image encryption. Nonlinear Dyn. 2018, 92, 305–313. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, P.; Huang, H.; Zhu, Y.; Xiao, D.; Xiang, Y. Privacy-Assured FogCS: Chaotic Compressive Sensing for Secure Industrial Big Image Data Processing in Fog Computing. IEEE Trans. Ind. Inform. 2020, 17, 3401–3411. [Google Scholar] [CrossRef]
- Oravec, J.; Ovsenik, L.; Papaj, J. An Image Encryption Algorithm Using Logistic Map with Plaintext-Related Parameter Values. Entropy 2021, 23, 1373. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, P.; Fang, L.; He, X.; Chen, B. Secure Transmission of Compressed Sampling Data Using Edge Clouds. IEEE Trans. Ind. Inform. 2020, 16, 6641–6651. [Google Scholar] [CrossRef]
- Ahmad, M.; Doja, M.N.; Beg, M.M.S. Security analysis and enhancements of an image cryptosystem based on hyperchaotic system. J. King Saud Univ.-Comput. Inf. Sci. 2021, 33, 77–85. [Google Scholar] [CrossRef]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Belazi, A.; Iliyasu, A.M. Efficient Chaos-Based Substitution-Box and Its Application to Image Encryption. Electronics 2021, 10, 1392. [Google Scholar] [CrossRef]
- El-Latif, A.A.A.; Abd-El-Atty, B.; Mazurczyk, W.; Fung, C.; Venegas-Andraca, S.E. Secure Data Encryption Based on Quantum Walks for 5G Internet of Things Scenario. IEEE Trans. Netw. Serv. Manag. 2020, 17, 118–131. [Google Scholar] [CrossRef]
- Wang, X.; Xue, W.; An, J. Image encryption algorithm based on tent-dynamics coupled map lattices and diffusion of household. Chaos Solitons Fractals 2020, 141, 110309. [Google Scholar] [CrossRef]
- Pourasad, Y.; Ranjbarzadeh, R.; Mardani, A. A new algorithm for digital image encryption based on chaos theory. Entropy 2021, 23, 341. [Google Scholar] [CrossRef] [PubMed]
- Feng, W.; He, Y.; Li, H.; Li, C. A Plain-Image-Related Chaotic Image Encryption Algorithm Based on DNA Sequence Operation and Discrete Logarithm. IEEE Access 2019, 7, 181589–181609. [Google Scholar] [CrossRef]
- Li, H.; Li, T.; Feng, W.; Zhang, J.; Zhang, J.; Gan, L.; Li, C. A novel image encryption scheme based on non-adjacent parallelable permutation and dynamic DNA-level two-way diffusion. J. Inf. Secur. Appl. 2021, 61, 102844. [Google Scholar] [CrossRef]
- Zhang, Q.; Guo, L.; Wei, X. A novel image fusion encryption algorithm based on DNA sequence operation and hyper-chaotic system. Opt.-Int. J. Light Electron Opt. 2013, 124, 3596–3600. [Google Scholar] [CrossRef]
- Abd EL-Latif, A.A.; Abd-El-Atty, B.; Abou-Nassar, E.M.; Venegas-Andraca, S.E. Controlled alternate quantum walks based privacy preserving healthcare images in Internet of Things. Opt. Laser Technol. 2020, 124, 105942. [Google Scholar] [CrossRef]
- Abd-El-Atty, B.; Iliyasu, A.M.; Alanezi, A.; Abd El-latif, A.A. Optical image encryption based on quantum walks. Opt. Lasers Eng. 2021, 138, 106403. [Google Scholar] [CrossRef]
- Ye, G.; Pan, C.; Dong, Y.; Shi, Y.; Huang, X. Image encryption and hiding algorithm based on compressive sensing and random numbers insertion. Signal Process. 2020, 172, 107563. [Google Scholar] [CrossRef]
- Chai, X.; Wu, H.; Gan, Z.; Han, D.; Zhang, Y.; Chen, Y. An efficient approach for encrypting double color images into a visually meaningful cipher image using 2D compressive sensing. Inf. Sci. 2021, 556, 305–340. [Google Scholar] [CrossRef]
- Wang, X.; Liu, C.; Jiang, D. A novel triple-image encryption and hiding algorithm based on chaos, compressive sensing and 3D DCT. Inf. Sci. 2021, 574, 505–527. [Google Scholar] [CrossRef]
- Hua, Z.; Zhu, Z.; Yi, S.; Zhang, Z.; Huang, H. Cross-plane colour image encryption using a two-dimensional logistic tent modular map. Inf. Sci. 2021, 546, 1063–1083. [Google Scholar] [CrossRef]
- Wang, X.; Chen, X. An image encryption algorithm based on dynamic row scrambling and Zigzag transformation. Chaos Solitons Fractals 2021, 147, 110962. [Google Scholar] [CrossRef]
- Bezerra, J.I.M.; de Almeida Camargo, V.V.; Molter, A. A new efficient permutation-diffusion encryption algorithm based on a chaotic map. Chaos Solitons Fractals 2021, 151, 111235. [Google Scholar] [CrossRef]
- Diaconu, A.V. Circular inter-intra pixels bit-level permutation and chaos-based image encryption. Inf. Sci. 2016, 355–356, 314–327. [Google Scholar] [CrossRef]
- Zefreh, E.Z. An image encryption scheme based on a hybrid model of DNA computing, chaotic systems and hash functions. Multimed. Tools Appl. 2020, 79, 24993–25022. [Google Scholar] [CrossRef]
- Feng, W.; He, Y. Cryptanalysis and improvement of the hyper-chaotic image encryption scheme based on DNA encoding and scrambling. IEEE Photonics J. 2018, 10, 7909215. [Google Scholar] [CrossRef]
- Feng, W.; He, Y.; Li, H.; Li, C. Cryptanalysis and improvement of the image encryption scheme based on 2D logistic-adjusted-sine map. IEEE Access 2019, 7, 12584–12597. [Google Scholar] [CrossRef]
- Feng, W.; He, Y.; Li, H.; Li, C. Cryptanalysis of the integrated chaotic systems based image encryption algorithm. Optik 2019, 186, 449–457. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, J. Cryptanalyzing a Novel Hyper-Chaotic Image Encryption Scheme Based on Pixel-Level Filtering and DNA-Level Diffusion. IEEE Access 2020, 8, 209471–209482. [Google Scholar] [CrossRef]
- Feng, W.; Qin, Z.; Zhang, J.; Ahmad, M. Cryptanalysis and Improvement of the Image Encryption Scheme Based on Feistel Network and Dynamic DNA Encoding. IEEE Access 2021, 9, 145459–145470. [Google Scholar] [CrossRef]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef] [Green Version]
- Preishuber, M.; Hütter, T.; Katzenbeisser, S.; Uhl, A. Depreciating motivation and empirical security analysis of chaos-based image and video encryption. IEEE Trans. Inf. Forensics Secur. 2018, 13, 2137–2150. [Google Scholar] [CrossRef]
- Gao, T.; Chen, Z.; Yuan, Z.; Yu, D. Adaptive synchronization of a new hyperchaotic system with uncertain parameters. Chaos Solitons Fractals 2007, 33, 922–928. [Google Scholar] [CrossRef]
- Li, C.; Feng, B.; Li, S.; Kurths, J.; Chen, G. Dynamic analysis of digital chaotic maps via state-mapping networks. IEEE Trans. Circuits Syst. I Regul. Pap. 2019, 66, 2322–2335. [Google Scholar] [CrossRef] [Green Version]
- Li, C.; Tan, K.; Feng, B.; Lü, J. The graph structure of the generalized discrete Arnold’s Cat map. IEEE Trans. Comput. 2022, 71, 364–377. [Google Scholar] [CrossRef]
- Sahasrabuddhe, A.; Laiphrakpam, D.S. Multiple images encryption based on 3D scrambling and hyper-chaotic system. Inf. Sci. 2021, 550, 252–267. [Google Scholar] [CrossRef]
- Gan, Z.; Chai, X.; Zhi, X.; Ding, W.; Lu, Y.; Wu, X. Image cipher using image filtering with 3D DNA-based confusion and diffusion strategy. Neural Comput. Appl. 2021, 33, 16251–16277. [Google Scholar] [CrossRef]
- Feng, W.; He, Y.; Li, H.; Li, C. Image encryption algorithm based on discrete logarithm and memristive chaotic system. Eur. Phys. J. Spec. Top. 2019, 228, 1951–1967. [Google Scholar] [CrossRef]
- Hua, Z.; Jin, F.; Xu, B.; Huang, H. 2D Logistic-Sine-coupling map for image encryption. Signal Process. 2018, 149, 148–161. [Google Scholar] [CrossRef]
- Feng, W.; Zhang, J.; Qin, Z. A Secure and Efficient Image Transmission Scheme Based on Two Chaotic Maps. Complexity 2021, 2021, 1898998. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y. Design of image cipher using block-based scrambling and image filtering. Inf. Sci. 2017, 396, 97–113. [Google Scholar] [CrossRef]
- Hua, Z.; Xu, B.; Jin, F.; Huang, H. Image Encryption Using Josephus Problem and Filtering Diffusion. IEEE Access 2019, 7, 8660–8674. [Google Scholar] [CrossRef]
- Ma, Y.; Li, C.; Ou, B. Cryptanalysis of an Image Block Encryption Algorithm Based on Chaotic Maps. J. Inf. Secur. Appl. 2020, 54, 102566. [Google Scholar] [CrossRef]
- Liu, S.; Li, C.; Hu, Q. Cryptanalyzing two image encryption algorithms based on a first-order time-delay system. IEEE Multimed. 2022, 29, 74–84. [Google Scholar] [CrossRef]
- Chen, L.; Li, C.; Li, C. Security Measurement of a Medical Image Communication Scheme based on Chaos and DNA. J. Vis. Commun. Image Represent. 2022, 83, 103424. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Pun, C.M.; Chen, C.P. 2D Sine Logistic modulation map for image encryption. Inf. Sci. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Huang, H. Cosine-transform-based chaotic system for image encryption. Inf. Sci. 2019, 480, 403–419. [Google Scholar] [CrossRef]
- Zhu, H.; Zhao, Y.; Song, Y. 2D Logistic-Modulated-Sine-Coupling-Logistic Chaotic Map for Image Encryption. IEEE Access 2019, 7, 14081–14098. [Google Scholar] [CrossRef]
- Cao, C.; Sun, K.; Liu, W. A novel bit-level image encryption algorithm based on 2D-LICM hyperchaotic map. Signal Process. 2018, 143, 122–133. [Google Scholar] [CrossRef]
- Wang, X.; Liu, L.; Zhang, Y. A novel chaotic block image encryption algorithm based on dynamic random growth technique. Opt. Lasers Eng. 2015, 66, 10–18. [Google Scholar] [CrossRef]
- Wu, X.; Wang, D.; Kurths, J.; Kan, H. A novel lossless color image encryption scheme using 2D DWT and 6D hyperchaotic system. Inf. Sci. 2016, 349–350, 137–153. [Google Scholar] [CrossRef]
- Chai, X.; Chen, Y.; Broyde, L. A novel chaos-based image encryption algorithm using DNA sequence operations. Opt. Lasers Eng. 2017, 88, 197–213. [Google Scholar] [CrossRef]













| Row Index (Generator g) | |||||||
|---|---|---|---|---|---|---|---|
| 1 (3) | 2 (5) | 3 (6) | 4 (7) | 5 (10) | 6 (12) | 7 (14) | 8 (19) |
| 9 (20) | 10 (24) | 11 (27) | 12 (28) | 13 (33) | 14 (37) | 15 (38) | 16 (39) |
| 17 (40) | 18 (41) | 19 (43) | 20 (45) | 21 (47) | 22 (48) | 23 (51) | 24 (53) |
| 25 (54) | 26 (55) | 27 (56) | 28 (63) | 29 (65) | 30 (66) | 31 (69) | 32 (71) |
| 33 (74) | 34 (75) | 35 (76) | 36 (77) | 37 (78) | 38 (80) | 39 (82) | 40 (83) |
| 41 (85) | 42 (86) | 43 (87) | 44 (90) | 45 (91) | 46 (93) | 47 (94) | 48 (96) |
| 49 (97) | 50 (101) | 51 (102) | 52 (103) | 53 (105) | 54 (106) | 55 (107) | 56 (108) |
| 57 (109) | 58 (110) | 59 (112) | 60 (115) | 61 (119) | 62 (125) | 63 (126) | 64 (127) |
| Generator g (Discrete Logarithm) | |||||||
|---|---|---|---|---|---|---|---|
| 3 (2) | 5 (14) | 6 (162) | 7 (250) | 10(174) | 12(66) | 14 (154) | 19(170) |
| 20 (78) | 24 (226) | 27 (86) | 28 (58) | 33 (26) | 37 (166) | 38 (74) | 39 (134) |
| 40 (238) | 41 (54) | 43 (94) | 45 (18) | 47 (42) | 48 (130) | 51 (146 | 53 (210 |
| 54 (246) | 55 (102) | 56 (218) | 63 (206) | 65 (194) | 66 (186) | 69 (106) | 71 (22) |
| 74 (70) | 75 (30) | 76 (234) | 77 (82) | 78 (38) | 80 (142) | 82 (214) | 83 (222) |
| 85 (158) | 86 (254) | 87 (62) | 90 (178) | 91 (126) | 93 (118) | 94 (202) | 96 (34) |
| 97 (46) | 101 (198) | 102 (50) | 103 (242) | 105 (138) | 106 (114) | 107 (190) | 108 (150) |
| 109 (230) | 110 (6) | 112 (122) | 115 (182) | 119 (10) | 125 (90) | 126 (110) | 127 (98) |
| Image Size | Filename | IEA-IF-DLT | Ref. [40] | Ref. [47] | Ref. [48] | Ref. [49] | Ref. [50] |
|---|---|---|---|---|---|---|---|
| 5.1.09 | 99.6025 | 99.6136 | 99.6658 | 99.6292 | 99.6084 | 99.6140 | |
| 5.1.10 | 99.6094 | 99.6258 | 99.6475 | 99.6292 | 99.6155 | 99.5880 | |
| 5.1.11 | 99.6189 | 99.5787 | 99.6674 | 99.7055 | 99.6094 | 99.6033 | |
| 5.1.12 | 99.6178 | 99.6265 | 99.5941 | 99.7055 | 99.5758 | 99.5651 | |
| 5.1.13 | 99.5956 | 99.6246 | 99.6445 | 99.6765 | 99.6170 | 99.5789 | |
| 5.1.14 | 99.6075 | 99.6134 | 99.5975 | 99.6765 | 99.6353 | 99.6765 | |
| 5.2.08 | 99.6136 | 99.6251 | 99.6281 | 99.6250 | 99.6151 | 99.6037 | |
| 5.2.09 | 99.5850 | 99.5703 | 99.6197 | 99.6292 | 99.6094 | 99.6029 | |
| 5.2.10 | 99.6181 | 99.6031 | 99.6288 | 99.6212 | 99.6166 | 99.6124 | |
| 7.1.01 | 99.6006 | 99.6124 | 99.6273 | 99.6208 | 99.5872 | 99.6082 | |
| 7.1.02 | 99.6170 | 99.6116 | 99.5892 | 99.6025 | 99.6109 | 99.6174 | |
| boat.512 | 99.6178 | 99.6052 | 99.6006 | 99.6181 | 99.5998 | 99.6101 | |
| elaine.512 | 99.6128 | 99.6131 | 99.6128 | 99.6076 | 99.6227 | 99.6087 | |
| gray21.512 | 99.6052 | 99.6173 | 99.6082 | 99.6029 | 99.5949 | 99.6159 | |
| numbers.512 | 99.6231 | 99.5912 | 99.6059 | 99.6081 | 99.6006 | 99.9075 | |
| ruler.512 | 99.6069 | 99.6168 | 99.6265 | 99.6033 | 99.6091 | 99.6212 | |
| 5.3.01 | 99.6082 | 99.6124 | 99.6098 | 99.6061 | 99.6035 | 99.6072 | |
| 5.3.02 | 99.6136 | 99.6231 | 99.6119 | 99.6190 | 99.6117 | 99.6116 | |
| 7.2.01 | 99.6128 | 99.6278 | 99.6156 | 99.6077 | 99.6013 | 99.6204 | |
| testpat.1k | 99.6037 | 99.6153 | 99.6124 | 99.6099 | 99.6048 | 99.6091 | |
| Average | 99.60951 | 99.6115 | 99.6207 | 99.6302 | 99.6075 | 99.6241 | |
| Std. Dev. | 0.009131 | 0.01565 | 0.02185 | 0.03311 | 0.01274 | 0.06993 |
| Image Size | Filename | IEA-IF-DLT | Ref. [40] | Ref. [47] | Ref. [48] | Ref. [49] | Ref. [50] |
|---|---|---|---|---|---|---|---|
| 5.1.09 | 33.4823 | 33.4698 | 33.5980 | 33.3651 | 33.5253 | 33.4032 | |
| 5.1.10 | 33.4801 | 33.4425 | 33.5366 | 33.5240 | 33.5115 | 33.3557 | |
| 5.1.11 | 33.5077 | 33.3855 | 33.4398 | 33.5106 | 33.5174 | 33.4696 | |
| 5.1.12 | 33.4835 | 33.3982 | 33.4228 | 33.4172 | 33.4202 | 33.4634 | |
| 5.1.13 | 33.5054 | 33.5099 | 33.4205 | 33.5065 | 33.5019 | 33.3046 | |
| 5.1.14 | 33.4667 | 33.3925 | 33.4696 | 33.4875 | 33.4939 | 33.4796 | |
| 5.2.08 | 33.4357 | 33.4410 | 33.4720 | 33.4973 | 33.4766 | 33.4493 | |
| 5.2.09 | 33.4687 | 33.4675 | 33.4921 | 33.4778 | 33.4528 | 33.5077 | |
| 5.2.10 | 33.4323 | 33.4502 | 33.4914 | 33.4327 | 33.3925 | 33.4457 | |
| 7.1.01 | 33.4514 | 33.5002 | 33.5212 | 33.4154 | 33.5017 | 33.4890 | |
| 7.1.02 | 33.4628 | 33.5121 | 33.4846 | 33.4698 | 33.4415 | 33.4190 | |
| boat.512 | 33.4590 | 33.5100 | 33.5097 | 33.4472 | 33.4519 | 33.5414 | |
| elaine.512 | 33.4593 | 33.4650 | 33.5477 | 33.4337 | 33.5083 | 33.4791 | |
| gray21.512 | 33.4435 | 33.4919 | 33.3930 | 33.4781 | 33.4314 | 33.4331 | |
| numbers.512 | 33.4743 | 33.4759 | 33.3993 | 33.4772 | 33.3567 | 33.5396 | |
| ruler.512 | 33.4256 | 33.4539 | 33.5129 | 33.3883 | 33.3984 | 33.4363 | |
| 5.3.01 | 33.4611 | 33.3901 | 33.4532 | 33.4683 | 33.4741 | 33.4886 | |
| 5.3.02 | 33.4760 | 33.3851 | 33.4853 | 33.4428 | 33.4393 | 33.4384 | |
| 7.2.01 | 33.4289 | 33.5356 | 33.4965 | 33.4688 | 33.4548 | 33.4192 | |
| testpat.1k | 33.4755 | 33.4425 | 33.4455 | 33.4616 | 33.4447 | 33.4452 | |
| Average | 33.46401 | 33.4560 | 33.4796 | 33.4585 | 33.4597 | 33.4504 | |
| Std. Dev. | 0.023121 | 0.04684 | 0.05158 | 0.04102 | 0.04602 | 0.05610 |
| Image Size | Image Type | Filename | CC | ||
|---|---|---|---|---|---|
| Horizontal | Vertical | Diagonal | |||
| Plain image | 5.1.09 | 0.9389 | 0.9023 | 0.9035 | |
| 5.1.10 | 0.8606 | 0.9051 | 0.8217 | ||
| 5.1.11 | 0.9368 | 0.9574 | 0.8921 | ||
| Cipher image | 5.1.09 | 0.0014 | −0.0007 | −0.0019 | |
| 5.1.10 | −0.0014 | −0.0008 | −0.0038 | ||
| 5.1.11 | 0.0034 | 0.0026 | −0.0046 | ||
| Plain image | 5.2.08 | 0.8912 | 0.9366 | 0.8580 | |
| 5.2.09 | 0.8606 | 0.9008 | 0.8028 | ||
| 5.2.10 | 0.9279 | 0.9401 | 0.8972 | ||
| Cipher image | 5.2.08 | 0.0019 | −0.0025 | −0.0051 | |
| 5.2.09 | −0.0005 | 0.0018 | 0.0022 | ||
| 5.2.10 | 0.0010 | −0.0017 | −0.0039 | ||
| Plain image | 5.3.01 | 0.9812 | 0.9775 | 0.9669 | |
| 5.3.02 | 0.9032 | 0.9104 | 0.8590 | ||
| 7.2.01 | 0.9467 | 0.9646 | 0.9448 | ||
| Cipher image | 5.3.01 | 0.0012 | −0.0020 | −0.0004 | |
| 5.3.02 | 0.0018 | 0.0004 | −0.0004 | ||
| 7.2.01 | 0.0006 | 0.0012 | 0.0009 | ||
| Image Size | Image Filename | Information Entropy Value | |
|---|---|---|---|
| Plain Image | Cipher Image | ||
| 5.2.08 | 7.2010 | 7.9992 | |
| 5.2.09 | 6.9940 | 7.9992 | |
| 5.2.10 | 5.7056 | 7.9993 | |
| 7.1.01 | 6.0274 | 7.9994 | |
| 7.1.02 | 4.0045 | 7.9992 | |
| 7.1.03 | 5.4957 | 7.9992 | |
| 7.1.04 | 6.1074 | 7.9993 | |
| 7.1.05 | 6.5632 | 7.9994 | |
| 7.1.06 | 6.6953 | 7.9994 | |
| 7.1.07 | 5.9916 | 7.9993 | |
| 7.1.08 | 5.0534 | 7.9993 | |
| boat.512 | 7.1914 | 7.9993 | |
| elaine.512 | 7.5060 | 7.9992 | |
| gray21.512 | 4.3923 | 7.9994 | |
| numbers.512 | 7.7292 | 7.9994 | |
| ruler.512 | 0.5000 | 7.9992 | |
| 5.3.01 | 7.5237 | 7.9998 | |
| 5.3.02 | 6.8303 | 7.9998 | |
| 7.2.01 | 5.6415 | 7.9998 | |
| testpat.1k | 4.4077 | 7.9998 | |
| Encryption Algorithm | Information Entropy Value |
|---|---|
| Ref. [47] | 7.9992 |
| Ref. [51] | 7.9971 |
| Ref. [25] | 7.9980 |
| Ref. [52] | 7.9909 |
| Ref. [48] | 7.9992 |
| Ref. [40] | 7.9992 |
| Ref. [43] | 7.9992 |
| Ref. [26] | 7.9976 |
| IEA-IF-DLT | 7.99931 |
| Image Size | |||
|---|---|---|---|
| Ref. [47] | 0.0538 s | 0.2338 s | 1.1494 s |
| Ref. [40] | 0.0800 s | 0.4842 s | 2.2848 s |
| Ref. [49] | 0.9261 s | 3.8887 s | 19.3147 s |
| Ref. [50] | 0.3243 s | 1.6113 s | 7.7342 s |
| Ref. [48] | 0.0949 s | 0.4010 s | 1.9857 s |
| Ref. [25] | 0.2224 s | 0.9731 s | 3.8377 s |
| Ref. [42] | 0.6347 s | 2.4913 s | 9.9185 s |
| Ref. [53] | 0.9810 s | 3.8539 s | 15.4565 s |
| IEA-IF-DLT | 0.0324 s | 0.1638 s | 0.9118 s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Feng, W.; Zhao, X.; Zhang, J.; Qin, Z.; Zhang, J.; He, Y. Image Encryption Algorithm Based on Plane-Level Image Filtering and Discrete Logarithmic Transform. Mathematics 2022, 10, 2751. https://doi.org/10.3390/math10152751
Feng W, Zhao X, Zhang J, Qin Z, Zhang J, He Y. Image Encryption Algorithm Based on Plane-Level Image Filtering and Discrete Logarithmic Transform. Mathematics. 2022; 10(15):2751. https://doi.org/10.3390/math10152751
Chicago/Turabian StyleFeng, Wei, Xiangyu Zhao, Jing Zhang, Zhentao Qin, Junkun Zhang, and Yigang He. 2022. "Image Encryption Algorithm Based on Plane-Level Image Filtering and Discrete Logarithmic Transform" Mathematics 10, no. 15: 2751. https://doi.org/10.3390/math10152751