A Systematic Methodology for Developing Bowtie in Risk Assessment: Application to Borescope Inspection
Abstract
:1. Introduction
2. Review of Bowtie Development and Structures
2.1. Existing Approaches Constructing a Bowtie Diagram
2.2. Categorisations Applied in Bowtie Analysis
2.3. General Categorisations and Classifications in Risk Management
2.3.1. Risk Categorisations
2.3.2. Threat and Root Cause Categorisations
2.3.3. Human Factors Categorisations
2.4. Limitation in the Methods for Bowtie Construction
3. Method
3.1. Purpose
3.2. Approach
- ‘Please describe the inspection process you are performing and the challenges of each step.’
- ‘What factors influence the inspection process and why are they safety critical?’
- ‘What are the risks inherent in each process step?’
- ‘What means of prevention or mitigation are or could be in place to prevent missing a defect during inspection?’
4. Results
4.1. Consistent Interpretation of Relationship between Hazard and Top Event
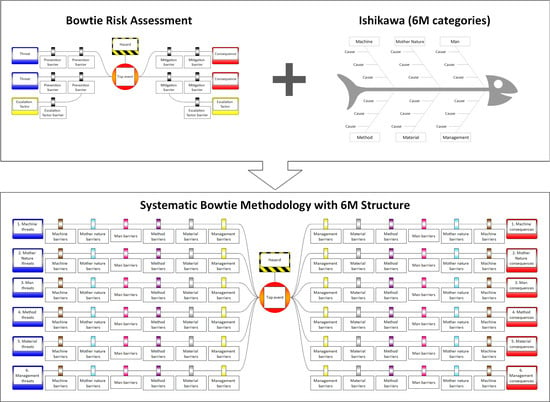
4.2. Proposal to Use 6M Structure
4.3. Integration of 6M with Bowtie (Contextualisation)
4.4. Threats and Consequence Structure Using 6M
4.4.1. Threat Structure in MRO
4.4.2. Consequences for Different Stakeholders
Immediate Consequences for the MRO Service Provider
Subsequent Consequences for the Airline
4.4.3. Combined Threat and Consequence Structure Using 6M
4.5. Barrier Structures Using 6M
4.5.1. Generic 6M Barrier Structure
4.5.2. Colour Coding of Barriers
4.5.3. Escalation Factor Paths with a 6M Structure
4.5.4. Barrier Modules
4.6. Full Bowtie with a 6M Structure
4.7. Application to a Case Study
5. Discussion
5.1. Summary of Outcomes
5.2. Implications for Practitioners
5.3. Limitations of the Work
5.4. Implications for Future Research
6. Conclusions
Supplementary Materials
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A








References
- Shahriar, A.; Sadiq, R.; Tesfamariam, S. Risk Analysis for Oil & Gas Pipelines: A Sustainability Assessment Approach using Fuzzy based Bow-Tie Analysis; Elsevier: Amsterdam, The Netherlands, 2012; Volume 25, pp. 505–523. [Google Scholar] [CrossRef]
- De Ruijter, A.; Guldenmund, F. The bowtie method: A review. Saf. Sci. 2016, 88, 211–218. [Google Scholar] [CrossRef]
- Federal Aviation Administration (FAA). Bow-Tie Analysis. Available online: http://www.hf.faa.gov/workbenchtools/default.aspx?rPage=Tooldetails&subCatId=43&toolID=21 (accessed on 1 October 2018).
- Civil Aviation Authority (CAA). Bowtie Risk Assessment Models. Available online: https://www.caa.co.uk/Safety-Initiatives-and-Resources/Working-with-industry/Bowtie/ (accessed on 25 September 2018).
- European Aviation Safety Agency (EASA). The European Plan for Aviation Safety (EBAS) 2018–2022; European Aviation Safety Agency: Cologne, Germany, 2018. [Google Scholar]
- Civil Aviation Authority (CAA) of New Zealand. Making Safe Aviation Even Safer. In Civil Aviation Authority Sector Risk profile of Medium and Large Aircraft Air Transport; CAA: Wellington, New Zealand, 2017. [Google Scholar]
- Aust, J.; Pons, D. Bowtie Methodology for Risk Analysis of Visual Borescope Inspection during Aircraft Engine Maintenance. Aerospace 2019, 6, 110. [Google Scholar] [CrossRef] [Green Version]
- Delmotte, F. A Sociotechnical Framework for the Integration of Human and Organizational Factors in Project Management and Risk Analysis. Master’s Thesis, Virginia Tech, Blacksburg, VA, USA, 2003. [Google Scholar]
- Brown, K. Review of the South Island Rail Coal Route—MET351-X-REP-001. Available online: www.ltsa.govt.nz/rail/coal-route (accessed on 27 September 2018).
- Van Scyoc, K.; Hughes, G. Rail ruminations for process safety improvement. J. Loss Prev. Process Ind. 2009, 22, 689–694. [Google Scholar] [CrossRef]
- Papazoglou, I.A.; Bellamy, L.J.; Hale, A.R.; Aneziris, O.N.; Ale, B.J.M.; Post, J.G.; Oh, J.I.H. I-Risk: Development of an integrated technical and management risk methodology for chemical installations. J. Loss Prev. Process Ind. 2003, 16, 575–591. [Google Scholar] [CrossRef]
- De Dianous, V.; Fievez, C. ARAMIS project: A more explicit demonstration of risk control through the use of bow–tie diagrams and the evaluation of safety barrier performance. J. Hazard. Mater. 2006, 130, 220–233. [Google Scholar] [CrossRef] [Green Version]
- Burgess-Limerick, R.; Horberry, T.; Steiner, L. Bow-tie analysis of a fatal underground coal mine collision. Ergon. Aust. 2014, 10, 1–5. [Google Scholar]
- Abdo, H.; Kaouk, M.; Flaus, J.M.; Masse, F. A safety/security risk analysis approach of Industrial Control Systems: A cyber bowtie combining new version of attack tree with bowtie analysis. Comput. Secur. 2018, 72, 175–195. [Google Scholar] [CrossRef] [Green Version]
- Bernsmed, K.; Frøystad, C.; Meland, P.H.; Nesheim, D.A.; Rødseth, Ø.J. Visualizing cyber security risks with bow-tie diagrams. In International Workshop on Graphical Models for Security; Springer: Berlin/Heidelberg, Germany, 2017; pp. 38–56. [Google Scholar]
- Faulkner, A.; Nicholson, M. Data-Centric Safety: Challenges, Approaches, and Incident Investigation; Elsevier: Amsterdam, The Netherlands, 2020. [Google Scholar]
- Culwick, M.D.; Merry, A.F.; Clarke, D.M.; Taraporewalla, K.J.; Gibbs, N.M. Bow-Tie Diagrams for Risk Management in Anaesthesia. Anaesth. Intensive Care 2016, 44, 712–718. [Google Scholar] [CrossRef] [Green Version]
- Abdi, Z.; Ravaghi, H.; Abbasi, M.; Delgoshaei, B.; Esfandiari, S. Application of Bow-tie methodology to improve patient safety. Int. J. Health Care Qual. Assur. 2016, 29, 425–440. [Google Scholar] [CrossRef]
- Janssen, E. Patient Safety BowTies. Available online: http://www.patientsafetybowties.com/knowledge-base/5-why-bowties-in-healthcare (accessed on 13 February 2020).
- Badreddine, A.; Amor, N.B. A Bayesian approach to construct bow tie diagrams for risk evaluation. Process Saf. Environ. Prot. 2013, 91, 159–171. [Google Scholar] [CrossRef]
- Maragakis, I.; Clark, S.; Piers, M.; Prior, D.; Tripaldi, C.; Masson, M.; Audard, C. Guidance on Hazard Identification. In Safety Management System and Safety Culture Working Group (SMSWG); European Commercial Aviation Safety Team (ECAST): Cologne, Germany, 2009; pp. 6–8. [Google Scholar]
- Acquisition Safety & Environmental Management System (ASEMS). Bow-Tie Diagram. Available online: https://www.asems.mod.uk/content/bow-tie-diagram (accessed on 4 April 2020).
- Ishikawa, K. Introduction to Quality Control; Productivity Press: New York, NY, USA, 1990. [Google Scholar]
- Lewis, S. Lessons Learned from Real World Application of the Bow-tie Method. In Proceedings of the 6th Global Congress on Process Safety, Antonio, TX, USA, 22–24 March 2010; Available online: https://www.aiche.org/academy/videos/conference-presentations/lessons-learned-real-world-application-bow-tie-method (accessed on 27 October 2018).
- Civil Aviation Authority (CAA). CAA ‘Significant Seven’ Task Force Reports. In CAA PAPER 2011/03; CAA: London, UK, 2011. Available online: https://publicapps.caa.co.uk/docs/33/2011_03.pdf (accessed on 25 October 2018).
- Joint Industry Program. The BowTie Examples Library. In Joint Industries Project; CGE Risk Management Solutions: Leidschendam, The Netherlands, 2016. [Google Scholar]
- International Civil Aviation Organization (ICAO). Safety Management Manual (SMM), 3rd ed.; ICAO: Montreal, QC, Canada, 2012. [Google Scholar]
- Sklet, S. Safety barriers: Definition, classification, and performance. J. Loss Prev. Process Ind. 2006, 19, 494–506. [Google Scholar] [CrossRef]
- Badreddine, A.; Romdhane, T.B.; HajKacem, M.A.B.; Amor, N.B. A new multi-objectives approach to implement preventive and protective barriers in bow tie diagram. J. Loss Prev. Process Ind. 2014, 32, 238–253. [Google Scholar] [CrossRef]
- Jacinto, C.; Silva, C. A semi-quantitative assessment of occupational risks using bow-tie representation. Saf. Sci. 2010, 48, 973–979. [Google Scholar] [CrossRef]
- Visser, J.P. Developments in HSE management in oil and gas exploration and production. Saf. Manag. Chall. Chang. 1998, 1, 43–66. [Google Scholar]
- Manton, M.; Moat, A.; Ali, W.; Johnson, M.; Cowley, C. Representing Human Factors in Bowties as per the new CCPS/EI Book. In Proceedings of the CCPS Middle East Conference on Process Safety, Sanabis, Bahrain, 10 October 2017. [Google Scholar]
- Delvosalle, C.; Fiévez, C.; Pipart, A. ARAMIS Project: Reference Accident Scenarios Definition in SEVESO Establishment. J. Risk Res. 2006, 9, 583–600. [Google Scholar] [CrossRef]
- Hamzah, S. Use bow tie tool for easy hazard identification. In Proceedings of the 14th Asia Pacific Confederation of Chemical Engineering Congress, Singapore, 21–24 February 2012. [Google Scholar]
- Flight Safety Foundation. Basic Aviation Risk Standard. In Offshore Helicopter Operations; Flight Safety Foundation: Alexandria, VA, USA, 2015. [Google Scholar]
- Kang, J.; Zhang, J.; Gao, J. Analysis of the safety barrier function: Accidents caused by the failure of safety barriers and quantitative evaluation of their performance. J. Loss Prev. Process Ind. 2016, 43, 361–371. [Google Scholar] [CrossRef]
- Neogy, P.; Hanson, A.; Davis, P.; Fenstermacher, T. Hazard and barrier analysis guidance document. Department of Energy, Office of Operating Experience Analysis and Feedback, Report No. EH-33; Springer: Berlin/Heidelberg, Germany, 1996. [Google Scholar]
- Chevreau, F.R.; Wybo, J.L.; Cauchois, D. Organizing learning processes on risks by using the bow-tie representation. J. Hazard. Mater. 2006, 130, 276–283. [Google Scholar] [CrossRef]
- Wilson, P.F. Root Cause Analysis: A Tool for Total Quality Management; Quality Press: Milwaukee, WI, USA, 1993. [Google Scholar]
- Hall, D.; Hulett, D.; Graves, R. Universal Risk Project—Final Report; PMI Risk SIG: Newtown Township, PA, USA, 2002. [Google Scholar]
- Rose, K.H. A Guide to the Project Management Body of Knowledge (PMBOK® Guide), 5th ed.; Project Management Institute: Hampton, VA, USA, 2013; Volume 44. [Google Scholar]
- Hillson, D. Use a risk breakdown structure (RBS) to understand your risks. In Proceedings of the project Management Institute Annual Seminars & Symposium, San Antonio, TX, USA, 3–10 October 2002. [Google Scholar]
- Tanim, M.M.Z. Risk Management in International Business Handbook; 2019. [Google Scholar]
- Lester, A. Project Management, Planning and Control: Managing Engineering, Construction and Manufacturing Projects to PMI, APM and BSI Standards; Elsevier Science & Technology: Saint Louis, UK, 2013. [Google Scholar]
- Chung, W.; Zhu, M. Risk Assessment Based on News Articles: An Experiment on IT Companies. In Proceedings of the International Conference on Information Systems (ICIS 2012), Orlando, FL, USA, 16–19 December 2012. [Google Scholar]
- Deshpande, P. Study of Construction Risk Assessment Methodology for Risk Ranking. In Proceedings of the International Conference on Education, E Learning and Life Long Learning, Kuala Lumpur, Maleysia, 16–17 November 2015. [Google Scholar]
- Sandle, T. Approaching Risk Assessment: Tools and Methods; Newsletter; Global Biopharmaceutical Resources Inc.: Clarksburg, MD, USA, 2012; Volume 1, pp. 1–23. [Google Scholar]
- Kurian, G.T. The AMA Dictionary of Business and Management; AMACOM: Nashville, TN, USA, 2013. [Google Scholar]
- Pons, D. Strategic Risk Management: Application to Manufacturing. Open Ind. Manuf. Eng. J. 2010, 3, 13–29. [Google Scholar] [CrossRef] [Green Version]
- International Organization for Standardization (ISO). Information Technology. In Security Techniques—Information Security Management Systems Requirements; Joint Technical Committee ISO/IEC JTC1. Subcommittee SC 27; International Organization for Standardization (ISO): Geneva, Switzerland, 2013. [Google Scholar]
- Jouini, M.; Ben, L.; Ben Arfa Rabai, L.; Aissa, A. Classification of security threats in information systems. Procedia Comput. Sci. 2014, 32, 489–496. [Google Scholar] [CrossRef] [Green Version]
- Paradies, M. TapRoot—Root Cause Tree Dictionary; System Improvements, Inc.: Knoxville, TS, USA, 2015; Volume 9. [Google Scholar]
- International Air Transport Association (IATA). Safety Report; International Air Transport Association (IATA): Geneva, Switzerland; Montreal, QC, Canada, 2006. [Google Scholar]
- Liliana, L. A new model of Ishikawa diagram for quality assessment. In IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2016; Volume 161, p. 012099. [Google Scholar]
- Radziwill, N. Creating Ishikawa (Fishbone) Diagrams With R. Softw. Qual. Prof. 2017, 20, 47–48. [Google Scholar]
- Hristoski, I.; Kostoska, O.; Kotevski, Z.; Dimovski, T. Causality of Factors Reducing Competitiveness of e-Commerce Firms. Balk. Near East. J. Soc. Sci. 2017, 3, 109–127. [Google Scholar]
- Eckes, G. Six Sigma for Everyone; John Wiley & Sons: Hoboken, NJ, USA, 2003. [Google Scholar]
- Burch, R.F.; Strawderman, L.; Bullington, S.F. Global corporation rollout of ruggedised handheld devices: A Lean Six Sigma case study. Total Qual. Manag. Bus. Excell. 2016, 27, 1–16. [Google Scholar] [CrossRef]
- Bradley, E. Reliability Engineering: A Life Cycle Approach; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- See, J.E. Visual Inspection: A Review of the Literature; Sandia National Laboratories: Albuquerque, NM, USA, 2012.
- Wiegmann, D.A.; Shappell, S.A. A Human Error Approach to Aviation Accident Analysis: The Human Factors Analysis and Classification System; Routledge: London, UK, 2017. [Google Scholar]
- U.S. Department of Transportation. FAA-H-8083-32A, Federal Aviation Administration (FAA) Session. In Aviation Maintenance Technician Handbook—Powerplant; FAA: Washington, DC, USA, 2018; Volume 2. [Google Scholar]
- Wiener, E.; Nagel, D. Human Factors in Aviation; Academic Press Limited: London, UK, 1988. [Google Scholar]
- Gong, L.; Zhang, S.; Tang, P.; Lu, Y. An integrated graphic–taxonomic–associative approach to analyze human factors in aviation accidents. Chin. J. Aeronaut. 2014, 27, 226–240. [Google Scholar] [CrossRef] [Green Version]
- Said, M.; Mokhtar, A. Significant human risk factors in aviation maintenance. Sains Hum. 2014, 2, 31–34. [Google Scholar]
- Chang, Y.H.; Wang, Y.C. Significant human risk factors in aircraft maintenance technicians. Saf. Sci. 2010, 48, 54–62. [Google Scholar] [CrossRef]
- Johnson, W.; Maddox, M. A PEAR shaped model for better human factors. Cat Mag. 2007, 2, 20–21. [Google Scholar]
- CGE Risk. BowtieXP; CGE Risk: Leidschendam, The Netherlands, 2019. [Google Scholar]
- Wilken, M.; Hüske-Kraus, D.; Klausen, A.; Koch, C.; Schlauch, W.; Röhrig, R. Alarm Fatigue: Causes and Effects. In Proceedings of the GMDS, Oldenburg, Germany, 17–21 September 2017; pp. 107–111. [Google Scholar]
- Wong, K.C. Using an Ishikawa diagram as a tool to assist memory and retrieval of relevant medical cases from the medical literature. J. Med. Case Rep. 2011, 5, 120. [Google Scholar] [CrossRef] [Green Version]
- Hessing, T. 6M’s in Six Sigma (Six Ms or 5Ms and one P or 5M1P). Available online: https://sixsigmastudyguide.com/six-ms-6ms-or-5ms-and-one-p-5m1p/ (accessed on 15 February 2020).
- Boca, G.D. 6M in Management Education. Procedia Soc. Behav. Sci. 2015, 182, 4–9. [Google Scholar] [CrossRef] [Green Version]
- Vaanila, T. Process Development Using the Lean Six Sigma Methodology: Case: Oy AGA Ab, Linde Healthcare. Bachelor’s Thesis, HAMK Häme University of Applied Sciences, Hämeenlinna, Finland, 2015. [Google Scholar]
- Gwiazda, A. Quality tools in a process of technical project management. J. Achiev. Mater. Manuf. Eng. 2006, 18, 439–442. [Google Scholar]
- Levine, M.E. Alternatives to regulation: Competition in air transportation and the Aviation Act of 1975. J. Air Law Commer. 1975, 41, 703. [Google Scholar]
- Eceral, T.Ö.; Köroğlu, B.A. Incentive mechanisms in industrial development: An evaluation through defense and aviation industry of Ankara. ProcediaSoc. Behav. Sci. 2015, 195, 1563–1572. [Google Scholar] [CrossRef] [Green Version]
- Fraser, J.; Simkins, B. Enterprise Risk Management: Today’s Leading Research and Best Practices for Tomorrow’s Executives; John Wiley & Sons: Hoboken, NJ, USA, 2010; Volume 3. [Google Scholar]
- Rankin, W. MEDA Investigation Process. In Boeing Commercial Aero; Boeing: Chicago, IL, USA, 2007. [Google Scholar]
- Federal Aviation Administration (FAA). Addendum: Chapter 14—Human Factors (PDF). In Published Separately from Aviation Maintenance Technician Handbook FAA-H-8083-30; FAA: Washington, DC, USA, 2018. [Google Scholar]
- Christianson, M.K.; Sutcliffe, K.M.; Miller, M.A.; Iwashyna, T.J. Becoming a high reliability organization. Crit Care 2011, 15, 314. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Sutcliffe, K.M. High reliability organizations (HROs). Best Pract. Res. Clin. Anaesthesiol. 2011, 25, 133–144. [Google Scholar] [CrossRef]
- The Institute of Operational Risk (IOR). Risk Categorisation. Available online: https://www.ior-institute.org/sound-practice-guidance/risk-categorisation (accessed on 2 May 2020).
- Reason, J. Human Error; Cambridge university press: Cambridge, UK, 1990. [Google Scholar]
- Pons, D. Pike river mine disaster: Systems-engineering and organisational contributions. Safety 2016, 2, 21. [Google Scholar] [CrossRef] [Green Version]
- Ji, Z.; Pons, D.; Pearse, J. Why do workers take safety risks?—A conceptual model for the motivation underpinning perverse agency. Safety 2018, 4, 24. [Google Scholar] [CrossRef] [Green Version]



















| Category | Manufacturing | Maintenance | Health Care |
|---|---|---|---|
| 1st M | Method (workflow and production processes and procedures) | Method (maintenance processes and procedures) | Method (surgery or medical treatment procedures) |
| 2nd M | Man (operator human factors) | Man (inspector human factors) | Man (personnel human factors) |
| 3rd M | Mother Nature (Production environment and facilities) | Mother Nature (maintenance environment and facilities) | Mother Nature (hospital and GP facilities) |
| 4th M | Machine (manufacturing machinery) | Machine (repair machinery and inspection tools) | Machine (surgery equipment and tools) |
| 5th M | Material (manufactured product) | Material (maintained product) | Material (used product, e.g., medicine and aids) |
| 6th M | Measurement (quality control and maintenance) | Management (MRO organisation and regulators) | Man (patient) |
| 6M Category | Threat Description and Example |
|---|---|
| 1. Machine-related threats | Machine or tools not working properly, e.g., faulty borescope |
| 2. Mother Nature-related threats | Poor inspection environment, e.g., poor lighting |
| 3. Man-related threats | Human error or failure, e.g., misinterpretation of the defect |
| 4. Method-related threats | Lack of standard processes and procedures, e.g., incorrect, outdated or no standard working procedures |
| 5. Material-related threats | Poor condition of the part, e.g., deposit on blade hides defect |
| 6. Management threats | Poor operational management, e.g., time pressure leads to rushed inspection |
| 6M Category | Consequence Description and Example |
|---|---|
| 1. Machine-related consequences | Damage to machinery, e.g., damaged borescope |
| 2. Mother Nature-related consequences | Adverse effect on MRO environment, e.g., damage of test cell or facility |
| 3. Man-related consequences | Consequences for employees, e.g., additional training or certification needed |
| 4. Method-related consequences | Changes of methods required, e.g., revision of standard work protocols and subsequent re-training of staff |
| 5. Material-related consequences | Additional part preparation, e.g., water jet wash |
| 6. Management consequences | Reputational consequences, e.g., degradation of engine shop status |
| 6M Category | Consequence Description and Example |
|---|---|
| 1. Machine-related consequences | Damage to the engine or aircraft, e.g., uncontained engine failure |
| 2. Mother Nature-related consequences | Contamination of airport or nature after engine failure, e.g., debris from engine falls from aircraft |
| 3. Man-related consequences | Harm to passengers and cabin crew, e.g., fatality |
| 4. Method-related consequences | New procedures, e.g., additional checks before flight operation |
| 5. Material-related consequences | Material failure, e.g., propagation of a defect leads to part separation (FOD) |
| 6. Management consequences | Reputational or financial consequences for airline, e.g., compensation for causing harm |
| 6M Category | Barrier Description and Example |
|---|---|
| 1. Machine-related barriers | Machinery and inspection tool-related barriers, e.g., backup tools availability |
| 2. Mother Nature-related barriers | Work environmental barriers (external and internal environment, e.g., appropriate work place design |
| 3. Man-related barriers | Operator or inspector-related barriers, e.g., airmanship, self-awareness, and experience |
| 4. Method-related barriers | Prevention and mitigation processes and procedures, e.g., standard working procedures |
| 5. Material-related barriers | Material-related barriers |
| 6. Management barriers | Operational management-based barriers, e.g., provision of appropriate training |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aust, J.; Pons, D. A Systematic Methodology for Developing Bowtie in Risk Assessment: Application to Borescope Inspection. Aerospace 2020, 7, 86. https://doi.org/10.3390/aerospace7070086
Aust J, Pons D. A Systematic Methodology for Developing Bowtie in Risk Assessment: Application to Borescope Inspection. Aerospace. 2020; 7(7):86. https://doi.org/10.3390/aerospace7070086
Chicago/Turabian StyleAust, Jonas, and Dirk Pons. 2020. "A Systematic Methodology for Developing Bowtie in Risk Assessment: Application to Borescope Inspection" Aerospace 7, no. 7: 86. https://doi.org/10.3390/aerospace7070086