Multi-Source Reliable Multicast Routing with QoS Constraints of NFV in Edge Computing
Abstract
:1. Introduction
- We first introduce the reliable routing mode and formulate the problem of reliable NFV layout with various deployment costs, while taking account of the end-to-end latency. The aim is to find the scheme that consumes the least resources (minimal cost), including both the construction cost and recovery cost. Meanwhile, to minimize the cost, we assume that a VM can host more than one type of network function.
- We prove that the problem is an NP-hard (non-deterministic polynomial-time hard) problem.
- With the help of multilevel overlay directed (MOD) network and Steiner tree, a heuristic algorithm named Multi-Source Reliable Multicast Tree Construction (RMTC) is proposed. This algorithm handles the various deployment costs by MOD, chooses appropriate SFC placements shared by users, and guarantees the service’s QoS and reliability.
- Two real topologies are used to evaluate the performance of the proposed algorithm. Simulation results indicate that, compared to other heuristic algorithms, our scheme effectively reduces the cost of reliable services and stratifies the QoS requirements.
2. Related Work
3. Problem Statement
3.1. System Model
3.2. Reliable Transmission Model
- Nodes D and E receive the packet successfully and there is no packet loss, hence the recovery cost is zero.
- Nodes D or E do not receive the packet, and node B receives the packet successfully. There is packet loss in the links after node B, and, therefore, node B can retransmit the packet to nodes D or E, hence the recovery cost is 2.
- Nodes D and E do not receive the packet, and node B receives the packet successfully. There is packet loss in the links after node B, and, therefore, node B can retransmit the packet to nodes D and E, hence the recovery cost is 3.
- Nodes D or E do not receive the packet, and node B also does not receive the packet. There is packet loss in the links from source to node B, and, therefore, only the source node can retransmit the packet to nodes D or E, hence the recovery cost is 4.
- Nodes D and E do not receive the packet, and node B also does not receive the packet. There is packet loss in the links from the source node to node B, and, therefore, only the source node can retransmit the packet to nodes D and E, hence the recovery cost is 5.
3.3. Mixed Integer Linear Programming
3.4. The Challenge
4. Reliable Multicast Tree Construction
4.1. Overview
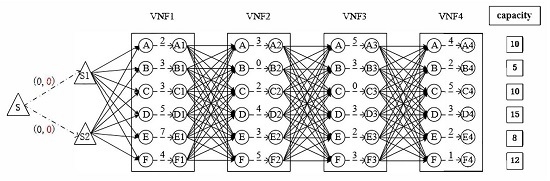
4.2. Multilevel Overlay Directed Network
- Step 1: Replicate all nodes of the network times, where is the length of the SFC. Arrange these nodes in a matrix form, in which columns denote VNF functions and rows denote nodes.
- Step 2: For each column, replicate all the nodes again and treat the column and its replicate as a model, meaning that there are models. Connect each node to its replicate with dotted arrows from left to right in a model, and connect all the nodes to all their right neighbors with solid arrows between models.
- Step 3: Set the link weights in a model to equal the corresponding VNF computation resource costs on VM, and set the edge weights between modes to equal the corresponding shortest path costs between the two nodes in G.
4.3. SFC Embedding
4.4. Multicast Tree Construction
4.5. Reliability Guarantee
| Algorithm 1: MOD network transformation |
 |
| Algorithm 2: Steiner Tree Construction |
| Input: ,, the last VNF’s location node u. Output: A Steiner tree with the least bandwidth consumption. 1 Calculate the shortest path between every two nodes in G by Floyd; 2 Pick out node u and in G to construct a complete graph , and the link’s weight is the shortest path length between nodes in G.; 3 Find a minimal spanning tree by Prim algorithm; 4 Get by replacing every link in with the shortest path in G; 5 return |
| Algorithm 3: Reliable Multicast Tree Construction |
 |
4.6. QoS Guarantee
4.7. Computation Complexity Analysis
5. Performance Evaluation
5.1. Simulation Environment
- Two Stages Service Function Tree Embedding Algorithm (TSE) [41]: It also finds a multicast tree with minimum cost when some VNFs have run on some VM nodes. However, the reliability of this tree solution is not guaranteed. Therefore, we do some modification to support reliability by treating the source as recovery node and considering the recovery cost as a part of the total cost.
- Recovery-aware Steiner Tree Algorithm (RST) [29]: It guarantees the reliability but does not have provisions for embedding SFC. Therefore, we find the shortest path P from the virtual source to embed the SFC, then find a Steiner tree and combine them to let the flow arrive at all destination nodes. Path P should contain the recovery node to provide reliable routing. If Path P does not contain a recovery node, we connect P with the closest recovery node.
5.2. Simulation Results
5.2.1. Impact of Loss Rate
5.2.2. Impact of the Number of Destinations
5.2.3. Impact of the Number of Recovery Nodes
5.2.4. Impact of Weight
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| EC | Edge Computing |
| NFV | Network Function Virtualization |
| VNF | Virtual Network Function |
| QoS | Quality of Service |
| RMTC | Multi-Source Reliable Multicast Tree Construction |
| SFC | Service Function Chain |
| MOD | Multilevel Overlay Directed |
| NFs | Network Functions |
| VM | Virtual Machine |
| MRMRQC | Multi-Source Reliable Multicast Routing with QoS Constraints |
| MMRQC | Multi-Source Multi-Cast Routing with QoS Constraints |
| ST | Steiner Tree |
| SDN | Software Defined Network |
References
- Yin, Y.; Chen, L.; Xu, Y.; Wan, J.; Zhang, H.; Mai, Z. QoS prediction for service recommendation with deep feature learning in edge computing environment. Mob. Netw. Appl. 2019, 1–11. [Google Scholar] [CrossRef]
- Yin, Y.; Xu, Y.; Xu, W.; Min, G.; Pei, Y. Collaborative Service Selection via Ensemble Learning in Mixed Mobile Network Environments. Entropy 2017, 19, 358. [Google Scholar] [CrossRef]
- Li, W.; Chen, Z.; Gao, X.; Liu, W.; Wang, J. Multi-Model Framework for Indoor Localization under Mobile Edge Computing Environment. IEEE Internet Things J. 2019, 6, 4844–4853. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Yin, X.; Li, F.; Kim, H.J. An Enhanced PEGASIS Algorithm with Mobile Sink Support for Wireless Sensor Networks. Wirel. Commun. Mob. Comput. 2018, 2018, 1–9. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Pan, J.S.; Dao, T.K. An Improved Flower Pollination Algorithm for Optimizing Layouts of Nodes in Wireless Sensor Network. IEEE Access 2019, 7, 75985–75998. [Google Scholar] [CrossRef]
- He, S.; Tang, Y.; Li, Z.; Li, F.; Xie, K.; Kim, H.J.; Kim, G.J. Interference-Aware Routing for Difficult Wireless Sensor Network Environment with SWIPT. Sensors 2019, 19, 3978. [Google Scholar] [CrossRef] [PubMed]
- Network Functions Virtualization-Introductory White Pape. Available online: http://portal.etsi.org/NFV/NFV_White_Paper.pdf (accessed on 10 May 2018).
- Xie, K.; Li, X.; Wang, X.; Xie, G.; Wen, J.; Cao, J.; Zhang, D. Fast tensor factorization for accurate Internet anomaly detection. IEEE/ACM Trans. Netw. 2017, 25, 3794–3807. [Google Scholar] [CrossRef]
- Xie, K.; Wang, L.; Wang, X.; Xie, G.; Wen, J.; Zhang, G.; Cao, J.; Zhang, D.; Xie, K.; Wang, X.; et al. Accurate Recovery of Internet Traffic Data: A Sequential Tensor Completion Approach. IEEE/ACM Trans. Netw. (TON) 2018, 26, 793–806. [Google Scholar] [CrossRef]
- Gu, S.; Li, Z.; Wu, C.; Huang, C. An efficient auction mechanism for service chains in the NFV market. In Proceedings of the 2016 IEEE Conference on Computer Communications (INFOCOM), San Francisco, CA, USA, 10–15 April 2016; pp. 1–9. [Google Scholar]
- Li, L.E.; Liaghat, V.; Zhao, H.; Hajiaghay, M. PACE: Policy-Aware Application Cloud Embedding. In Proceedings of the 2013 IEEE Conference on Computer Communications (INFOCOM), Turin, Italy, 14–19 April 2013; pp. 638–646. [Google Scholar]
- Anwer, B.; Benson, T.; Feamster, N.; Levin, D. Programming slick network functions. In Proceedings of the 1st ACM SIGCOMM Symposium on Software Defined Networking Research, Santa Clara, CA, USA, 17–18 June 2015; pp. 1–13. [Google Scholar]
- Palkar, S.; Lan, C.; Han, S.; Jang, K.; Panda, A.; Ratnasamy, S.; Rizzo, L.; Shenker, S. E2:A framework for NFV applications. In Proceedings of the Symposium on Operating Systems Principles, Monterey, CA, USA, 4–7 October 2015; pp. 121–136. [Google Scholar]
- Cohen, R.; Lewin-Eytan, L.; Naor, J.S.; Raz, D. On the effect of forwarding table size on SDN network utilization. In Proceedings of the 2014 IEEE Conference on Computer Communications (INFOCOM), Toronto, ON, Canada, 27 April–2 May 2014; pp. 1734–1742. [Google Scholar]
- Cohen, R.; Lewin-Eytan, L.; Naor, J.S.; Raz, D. Near optimal placement of virtual network functions. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 1346–1354. [Google Scholar]
- Li, Y.; Phan, L.T.X.; Loo, B.T. Network functions virtualization with soft real-time guarantees. In Proceedings of the 2016 IEEE Conference on Computer Communications (INFOCOM), San Francisco, CA, USA, 10–15 April 2016; pp. 1–9. [Google Scholar]
- Lukovszki, T.; Schmid, S. Online Admission Control and Embedding of Service Chains. In Proceedings of the International Colloquium on Structural Information and Communication Complexity, Montserrat, Spain, 14–16 July 2015; pp. 104–118. [Google Scholar]
- Kuo, T.W.; Liou, B.H.; Lin, C.J.; Tsai, M.J. Deploying chains of virtual network functions: On the relation between link and server usage. In Proceedings of the 2016 IEEE Conference on Computer Communications (INFOCOM), San Francisco, CA, USA, 10–15 April 2016; pp. 1–9. [Google Scholar]
- Zhang, J.; Jin, X.; Sun, J.; Wang, J.; Sangaih, A.K. Spatial and semantic convolutional features for robust visual object tracking. Multimed. Tools. Appl. 2018. [Google Scholar] [CrossRef]
- Zhang, J.; Jin, X.; Sum, J.; Wang, J.; Li, K. Dual model learning combined with multiple feature selection for accurate visual tracking. IEEE Access 2019, 7, 43956–43969. [Google Scholar] [CrossRef]
- Chen, Y.; Wang, J.; Chen, X.; Zhu, M.; Kai, Y.; Wang, Z.; Xia, R. Single-Image Super-Resolution Algorithm Based on Structural Self-Similarity and Deformation Block Features. IEEE Access 2019, 7, 58791–58801. [Google Scholar] [CrossRef]
- He, S.; Li, Z.; Tang, Y.; Liao, Z.; Jin, W. Parameters Compressing in Deep Learning. Comput. Mater. Continua 2019, 1–16. [Google Scholar]
- Xie, K.; Peng, C.; Wang, X.; Xie, G.; Wen, J.; Cao, J.; Zhang, D.; Qin, Z. Accurate Recovery of Internet Traffic Data Under Variable Rate Measurements. IEEE/ACM Trans. Netw. 2018, 26, 1137–1150. [Google Scholar] [CrossRef]
- Xie, K.; Li, X.; Wang, X.; Cao, J.; Xie, G.; Wen, J.; Zhang, D.; Qin, Z. On-Line Anomaly Detection with High Accuracy. IEEE/ACM Trans. Netw. 2018, 26, 1222–1235. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, Z.; Li, B.; Lee, S.; Sherratt, R.S. An enhanced fall detection system for elderly person monitoring using consumer home networks. IEEE/ACM Trans. Consum. Electron. 2014, 60, 23–29. [Google Scholar] [CrossRef]
- Rajkumar, M.; Zhang, X.; Qiao, C. Benefits of multicasting in all-optical networks. In All-Optical Networking: Architecture, Control, and Management Issues; SPIE: Boston, MA, USA, 1998; Volume 3531, p. C805. [Google Scholar]
- Xu, Z.; Liang, W.; Huang, M.; Jia, M.; Guo, S.; Galis, A. Approximation and Online Algorithms for NFV-Enabled Multicasting in SDNs. In Proceedings of the IEEE 36th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 625–634. [Google Scholar]
- Molnar, M. Exact Algorithm to Solve the Minimum Cost Multi-Constrained Multicast Routing Problem. J. Comput. Commun. 2016, 4, 57–79. [Google Scholar] [CrossRef] [Green Version]
- Shen, S.H.; Huang, L.H.; Yang, D.N.; Chen, W.T. Reliable multicast routing for software-defined networks. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Hong Kong, China, 26 April–1 May 2015; pp. 181–189. [Google Scholar]
- Huang, L.H.; Hsu, H.C.; Shen, S.H.; Yang, D.N.; Chen, W.T. Multicast traffic engineering for software-defined networks. In Proceedings of the 2016 IEEE Conference on Computer Communications (INFOCOM), San Francisco, CA, USA, 10–15 April 2016; pp. 1–9. [Google Scholar]
- Kuo, J.J.; Shen, S.H.; Yang, M.H.; Yang, D.N.; Tsai, M.J.; Chen, W.T. Service overlay forest embedding for software-defined cloud networks. In Proceedings of the IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 720–730. [Google Scholar]
- Xie, K.; Zhou, X.; Semong, T.; He, S. Multi-Source Multicast Routing with QoS Constraints in Network Function Virtualization. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Babarczia, P.; Pasica, A.; Tapolcaia, J.; Nemethb, F.; Ladoczkia, B. Instantaneous recovery of unicast connections in transport networks: Routing versus coding. Comput. Netw. 2015, 82, 68–80. [Google Scholar] [CrossRef]
- Ayoubi, S.; Assi, C.; Chen, Y.; Khalifa, T.; Shaban, K.B. Restoration methods for cloud multicast virtual networks. J. Netw. Comput. Appl. 2017, 78, 180–190. [Google Scholar] [CrossRef]
- Xie, K.; Wang, X.; Liu, X.; Wen, J.; Cao, J. Interference-Aware Cooperative Communication in Multi-radio Multi-channel Wireless Networks. IEEE Trans. Comput. 2016, 65, 1528–1542. [Google Scholar] [CrossRef]
- Xie, K.; Wang, X.; Wen, J.; Cao, J. Cooperative routing with relay assignment in multiradio multihop wireless networks. IEEE/ACM Trans. Netw. 2015, 24, 859–872. [Google Scholar] [CrossRef]
- Xie, K.; Ning, X.; Wang, X.; Xie, D.; Cao, J.; Xie, G.; Wen, J. Recover corrupted data in sensor networks: A matrix completion solution. IEEE Trans. Mob. Comput. 2017, 16, 1434–1448. [Google Scholar] [CrossRef]
- Xie, K.; Ning, X.; Wang, X.; He, S.; Ning, Z.; Liu, X.; Wen, J.; Qin, Z. An efficient privacy-preserving compressive data gathering scheme in WSNs. Inf. Sci. 2017, 390, 82–94. [Google Scholar] [CrossRef]
- Wang, J.; Ju, C.; Kim, H.j.; Sherratt, R.S.; Lee, S. A mobile assisted coverage hole patching scheme based on particle swarm optimization for WSNs. Clust. Comput. 2019, 22, 1787–1795. [Google Scholar] [CrossRef]
- Wang, J.; Gu, X.; Liu, W.; Sangaiah, A.K.; Kim, H.J. An empower hamilton loop based data collection algorithm with mobile agent for WSNs. Hum.-Centric Comput. Inf. Sci. 2019, 9, 18. [Google Scholar] [CrossRef]
- Ren, B.; Guo, D.; Tang, G.; Lin, X.; Qin, Y. Optimal Service Function Tree Embedding for NFV Enabled Multicast. In Proceedings of the IEEE 38th International Conference on Distributed Computing Systems (ICDCS), Vienna, Austria, 2–5 July 2018; pp. 132–142. [Google Scholar]
- He, S.; Xie, K.; Chen, W.; Zhang, D.; Wen, J. Energy-aware Routing for SWIPT in Multi-hop Energy-constrained Wireless Network. IEEE Access 2018, 6, 17996–18008. [Google Scholar] [CrossRef]
- He, S.; Xie, K.; Xie, K.; Xu, C.; Jin, W. Interference-aware Multi-source Transmission in Multi-radio and Multi-channel Wireless Network. IEEE Syst. J. 2019, 13, 2507–2518. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Sangaiah, A.K.; Kim, H.J. An intelligent data gathering schema with data fusion supported for mobile sink in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2019. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Y.; Liu, W.; Wenbing, W.; Se-Jung, L. An Asynchronous Clustering and Mobile Data Gathering Schema based on Timer Mechanism in Wireless Sensor Networks. Comput. Mater. Contin. 2019, 58, 711–725. [Google Scholar] [CrossRef]
- Internet2 Network Infrastructure Topology. Available online: https://www.internet2.edu/ (accessed on 12 May 2018).
- Cogent’s Network Map. Available online: http://cogentco.com/en/network/network-map (accessed on 13 May 2018).
- Knight, S.; Nguyen, H.X.; Falkner, N.; Bowden, R.; Roughan, M. The internet topology zoo. IEEE J. Sel. Areas Commun. 2011, 29, 1765–1775. [Google Scholar] [CrossRef]
- Xu, Y.; Yu, C.; Li, J.; Liu, Y. Video telephony for end-consumers: Measurement study of Google+, iChat, and Skype. IEEE/ACM Trans. Netw. 2014, 22, 826–839. [Google Scholar] [CrossRef]
- Nguyen, H.X.; Roughan, M. Rigorous statistical analysis of internet loss measurements. Acm Sigmetrics Perform. Eval. Rev. - Perform. Eval. Rev. 2010, 38, 361–362. [Google Scholar] [CrossRef]














| Notation | Definition |
|---|---|
| V | The node set |
| E | The link set |
| Available computation capacity of node v | |
| Cost or required resource to deploy VNF (Virtual Network Function) f on VM m | |
| Delay of link | |
| Bandwidth consumption of link | |
| F | VNF set |
| A service chain consisting of | |
| The constructed multicast routing topology | |
| The neighbor node set of node v | |
| A binary variable which is 1 when VM m runs VNF f | |
| The number of times that was traversed by the flow | |
| A binary variable whether the flow from s to d pass through | |
| The upper bound of delay | |
| The upper bound of delay jitter | |
| The loss probability of link | |
| Recovery agent flag of node v | |
| The recovery cost of destination d | |
| T | The found multicast tree |
| Case | Node | Link | Data Center |
|---|---|---|---|
| Internet2 | 64 | 69 | 1 |
| Cogent | 190 | 260 | 40 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, S.; Xie, K.; Zhou, X.; Semong, T.; Wang, J. Multi-Source Reliable Multicast Routing with QoS Constraints of NFV in Edge Computing. Electronics 2019, 8, 1106. https://doi.org/10.3390/electronics8101106
He S, Xie K, Zhou X, Semong T, Wang J. Multi-Source Reliable Multicast Routing with QoS Constraints of NFV in Edge Computing. Electronics. 2019; 8(10):1106. https://doi.org/10.3390/electronics8101106
Chicago/Turabian StyleHe, Shiming, Kun Xie, Xuhui Zhou, Thabo Semong, and Jin Wang. 2019. "Multi-Source Reliable Multicast Routing with QoS Constraints of NFV in Edge Computing" Electronics 8, no. 10: 1106. https://doi.org/10.3390/electronics8101106