MULBER: Effective Android Malware Clustering Using Evolutionary Feature Selection and Mahalanobis Distance Metric
Abstract
:1. Introduction
- Both X and Y can be mapped to the same behavioral set so that if X is vulnerable, then Y would become consequent, and vice versa.
- Vulnerability validation could be applied to just one app out of the two.
- Vulnerability in X could be targeted at apps that communicate with Y.
- X and Y could be combined into a new behavior model, for example, Y’s vulnerability leads to vulnerability in X, (i.e., Y ⟶ X).
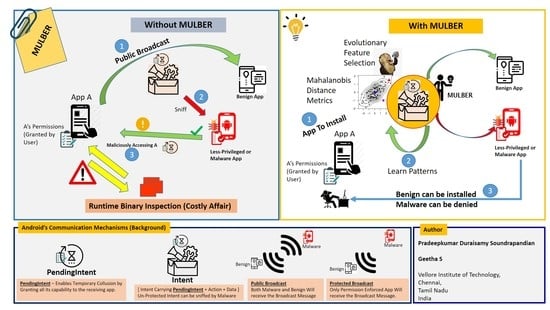
- We introduce a method combining binary analysis and the Mahalanobis distance metric based on a clustering method that is capable of identifying Android malware with high accuracy and few false alarms.
- MULBER can analyze an application’s communication patterns based on Intent and PendingIntent exchanges. However, MULBER cannot analyze the obfuscated or dynamically loaded malware, loading from the resources folder, or exporting sensitive information to malware servers.
- Feature Extraction Tool—We implement a feature extraction tool that can automatically collect the communication patterns from an application as evidence and present them as a .csv (comma separated values) file, and extract the important features using an evolutionary feature selection method.
- Mahalanobis Distance-Based Classifier—We use the Mahalanobis distance metric instead of the Euclidean metric to classify an app as benign or malware.
2. Related Works
3. Methodology
- Binary analysis. In the first step, MULBER statically inspects the given Android APK and extracts the different feature sets from the application’s manifest and dex code.
- The extracted feature sets are then pre-processed, for example, handling null values and the standardization of the extracted data.
- Key feature selection. Using an a priori algorithm, MULBER extracts the key features that can form a contour.
- Modifying dataset. MULBER creates a new dataset using the selected features, thereby removing the other features.
- Learning-based detection. The feature vector space enables us to identify malware clusters based on the Mahalanobis distance metric.
- Explanation. In the last step, the features contributing to the detection of communication leaks in a malicious application are identified and presented to the user, explaining the possibility of future malicious communication patterns.
3.1. Binary Analysis
3.1.1. Features from Manifest.xml
- Requested permissions: The permission system is one of the most significant security features of Android. A user must actively authorize the permissions for an application to access security-related resources at installation time. Malicious software frequently requests more permissions than legitimate apps [4].
- Filtered intents: Inter-process and intra-process communications in Android are mainly performed through asynchronous messages called Intents. The Intents carry information and actions to be performed by the receiving component. We collect all Intents listed in the manifest as another feature set and these Intents show the communication patterns such as inbound and outbound links.
3.1.2. Features from DEX Code
- Intent Communication: Android apps collaborate and share information with each other by exchanging a messaging object called an Intent [39]. An Intent is an unprotected object that carries data and the operation to be performed by the receiving application. Intents are used to start an activity, start a service, and to deliver a broadcast. The Android system classifies Intents into two types: (1) explicit Intents, and (2) implicit Intents.Explicit Intents specify the receiving application details such as the target app’s package name or a fully-qualified component class name. In other words, explicit Intents are used to start a component in a known application because the class name of the activity or service is fixed at the Intent creation time itself. On the other hand, implicit Intents declare a general action to perform. The Android framework takes the liberty to identify the target component for this action, i.e., a component from another app can also handle it. For example, in the following code snippet, the source application is dynamically collaborating with the camera app through the implicit Intent. In Line 1, the implicit Intent is created, in Line 4, the file location is added to the Intent, and in Line 5, the implicit Intent is shared publicly. In Figure 2 we can see the possible application communication based on both the implicit and explicit communication mechanisms. By inspecting the communication patterns and the payload exchanged with other applications, we can capture the vulnerability of an app.
- PendingIntent Communication: On the other hand, dynamic collaboration is also possible by exchanging PendingIntents (also known as Wrapping Intents (WI) [14]) between applications. The PendingIntent (PI) [40] dynamically grants authority that a PI creating app owns to the PI receiving app. This is a kind of temporary permission sharing between applications that lasts as long as the shared PendingIntent is valid. In the below code, the Wrapping Intent carries the created PendingIntent object between applications. In Line 1, we create an implicit Intent, and in Line 3, a PendingIntent object is created using the baseintent object created in Line 2, and in Line 4, the PendingIntent is parceled inside the implicit Intent. Finally, in Line 5, the PendingIntent is exported publicly.
3.2. Android Permissions
3.3. Security Features
- Whether the investigated application used dangerous permissions.
- Whether the investigated application had a vulnerable PI creation, for example, creation of a PI with an empty baseintent.
- Whether the investigated application exposed the vulnerable PI using an implicit broadcast.
| Algorithm 1 Dataset Generation from Android APK |
 |
3.4. Evolutionary Feature Selection
3.5. Mahalanobis Distance Metric
- Points—Points represents the variables that are mapped to an application and its characteristics, say, … .
- Mean—Represents the average of the given set of points , where i = 0…n
- Variance—The variance is a measurement of how dispersed the distribution of the provided collection of points is. It shows how the variable’s distribution looks close to the mean value. A small variance implies a distribution of the supplied variable that is close to the mean value, whereas a large variance suggests a distribution of the random variable that is distant from the mean value. Given X and Y are separate random variables:
- Covariance—Covariance is the directional relationship between the two variables; positive covariance means they move in the same direction, negative covariance means they move in an inverse direction, and zero covariance means there is no variation. The covariance metric compares the combined changes of the two variables, i.e., compares the variance rather than the dependency or strength between the given two variables.
- Covariance Matrix—The covariance matrix (also known as the variance–covariance matrix) represents the variance between the pair of elements along the diagonal and the covariance along the off-side of the diagonal. The covariance matrix gives the structured relationship between various variables in the given dataset.
| Algorithm 2 Training and prediction using Mahalanobis distance |
 |
4. Evaluation
4.1. Research Objectives
- RO-1: To investigate automatic feature selection related to PendingIntent vulnerabilities, implicit broadcast, and usage of dangerous permissions.
- RO-2: To investigate the impact of the proposed algorithm on the performance of Android malware clustering.
- RO-3: To evaluate the detection capability of the proposed model with the RAICC dataset [13] containing Android applications with PendingIntent vulnerabilities.
4.2. Dataset Generation
Classification of APKs Using PI Vulnerabilities
Report
- Highlights from Table 2:
- ∼9% of PI vulnerabilities were found in benign-tagged apps taken from the CICMalDroid-2020 dataset [52].
- ∼1.4% of implicit Intent vulnerabilities were found in benign apps taken from the CICMalDroid-2020 dataset.
- ∼0.15% of apps had vulnerable PI transfers (though it looks trivial, it can create precarious behavior in apps).
- In total, MULBER identified, ∼26% of dataset apps that had PendingIntent- and Intent-based vulnerabilities.
4.3. Evolutionary Feature Selection [RO-1]
4.4. Clustering Using Mahalanobis [RO-2]
4.5. Evaluation Using RAICC Dataset [RO3]
5. Limitations
- Imbalanced Dataset—This property was not considered in this paper, as training a model using a balanced dataset improves the accuracy; this paper focused mainly on the mechanism for handling the mutivariate features of applications using the Mahalanobis distance metric rather than Euclidean-metric-based clustering.
- This paper considered the PendingIntent and Intent exchanges between applications; however, as a future work, we plan to extend this to application behavior and other control-flow graph properties.
6. Future Work
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Mobile Operating System Market Share Worldwide (2021–2022). Available online: https://gs.statcounter.com/os-market-share/mobile/worldwide/ (accessed on 3 October 2022).
- Mobile Malware Evolution 2021. Available online: https://securelist.com/mobile-malware-evolution-2021/105876/ (accessed on 1 September 2022).
- Intents and Intent Filters. Available online: https://developer.android.com/guide/components/intents-filters (accessed on 5 October 2022).
- Enck, W.; Ongtang, M.; McDaniel, P. On lightweight mobile phone application certification. In Proceedings of the 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009; pp. 235–245. [Google Scholar]
- Felt, A.P.; Chin, E.; Hanna, S.; Song, D.; Wagner, D. Android permissions demystified. In Proceedings of the 18th ACM Conference on Computer and Communications Security (CCS ’11), Association for Computing Machinery, New York, NY, USA, 17–21 October 2011; pp. 627–638. [Google Scholar] [CrossRef] [Green Version]
- Grace, M.; Zhou, Y.; Zhang, Q.; Zou, S.; Jiang, X. RiskRanker: Scalable and accurate zero-day android malware detection. In Proceedings of the 10th International Conference on Mobile Systems, Applications, and Services (MobiSys ’12), Association for Computing Machinery, New York, NY, USA, 10–13 November 2012; pp. 281–294. [Google Scholar] [CrossRef]
- CVE-2021-25352. Samsung Mobile. Available online: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-25352 (accessed on 1 September 2022).
- CVE-2021-25364. Samsung Mobile. Available online: https://cve.mitre.org/cgi-bin/cvename.cgi?name=2021-25364 (accessed on 1 September 2022).
- CVE-2020-7039. Samsung Mobile. Available online: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-7039 (accessed on 1 September 2022).
- CVE-2022-22286. Samsung Mobile. Available online: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-22286 (accessed on 1 September 2022).
- Mahalanobis, P.C. On the generalised distance in statistics (PDF). Proc. Natl. Inst. Sci. India 1936, 2, 49–55. [Google Scholar]
- Euclidean Distance. Available online: https://en.wikipedia.org/wiki/Euclidean_distance (accessed on 5 October 2022).
- Samhi, J.; Bartel, A.; Bissyandé, T.F.; Klein, J. Raicc: Revealing atypical inter-component communication in android apps. In Proceedings of the 2021 IEEE/ACM 43rd International Conference on Software Engineering (ICSE), Madrid, Spain, 25–28 May 2021; pp. 1398–1409. [Google Scholar]
- Groß, S.; Tiwari, A.; Hammer, C. Pianalyzer: A precise approach for pendingintent vulnerability analysis. In European Symposium on Research in Computer Security; Springer: Cham, Switzerland, 2018; pp. 41–59. [Google Scholar]
- Li, L.; Bartel, A.; Bissyandé, T.F.; Klein, J.; Le Traon, Y.; Arzt, S.; Rasthofer, S.; Bodden, E.; Octeau, D.; McDaniel, P. Iccta: Detecting inter-component privacy leaks in android apps. In Proceedings of the 2015 IEEE/ACM 37th IEEE International Conference on Software Engineering, Florence, Italy, 16–24 May 2015; Volume 1, pp. 280–291. [Google Scholar]
- Wei, F.; Roy, S.; Ou, X. Amandroid: A precise and general inter-component data flow analysis framework for security vetting of android apps. Acm Trans. Priv. Secur. 2014, 21, 1–32. [Google Scholar] [CrossRef]
- Duraisamy, S.P.; Geetha, S.; Cheng, X.; Kadry, S. On Shielding Android’s Pending Intent from Malware Apps Using a Novel Ownership-Based Authentication. J. Circuits Syst. Comput. 2022, 31, 13. [Google Scholar]
- Zhang, C.; Li, S.; Diao, W.; Guo, S. PITracker: Detecting Android PendingIntent Vulnerabilities through Intent Flow Analysis. In Proceedings of the 15th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec ’22), Association for Computing Machinery, New York, NY, USA, 20–25 May 2022. [Google Scholar] [CrossRef]
- Duraisamy Soundrapandian, P.K.; Bao, T.; Baek, J.; Shoshitaishvili, Y.; Doupé, A.; Wang, R.; Ahn, G.J. Mutent: Dynamic android intent protection with ownership-based key distribution and security contracts. In Proceedings of the 54th Hawaii International Conference on System Sciences, Kauai, HI, USA, 5–8 January 2021; pp. 7217–7226. [Google Scholar]
- Stone, M. Securing the System: A Deep Dive into Reversing Android Pre-Installed Apps. Available online: https://i.blackhat.com/USA-19/Thursday/us-19-Stone-Securing-The-System-A-Deep-Dive-Into-Reversing-Android-Preinstalled-Apps.pdf (accessed on 1 September 2022).
- Lee, Y.K.; Bang, J.Y.; Safi, G.; Shahbazian, A.; Zhao, Y.; Medvidovic, N. A sealant for inter-app security holes in android. In Proceedings of the 2017 IEEE/ACM 39th International Conference on Software Engineering, Buenos Aires, Argentina, 20–28 May 2017; pp. 312–323. [Google Scholar]
- Hammad, M.; Garcia, J.; Malek, S. Self-protection of android systems from inter-component communication attacks. In Proceedings of the 2018 33rd IEEE/ACM International Conference on Automated Software Engineering, Montpellier, France, 3–7 September 2018; pp. 726–737. [Google Scholar]
- Hammad, M.; Garcia, J.; Malek, S. Static analysis of implicit control flow: Resolving java reflection and android intents. In Proceedings of the 2018 33rd IEEE/ACM International Conference on Automated Software Engineering, Montpellier, France, 3–7 September 2015. [Google Scholar]
- Alhanahnah, M.; Yan, Q.; Bagheri, H.; Zhou, H.; Tsutano, Y.; Srisa-An, W.; Luo, X. DINA: Detecting Hidden Android Inter-App Communication in Dynamic Loaded Code. IEEE Trans. Inf. Forensics Secur. 2020, 15, 2782–2797. [Google Scholar] [CrossRef]
- Demissie, B.F.; Ceccato, M.; Shar, L.K. Security analysis of permission re-delegation vulnerabilities in android apps. Empir. Softw. Eng. 2020, 25, 5084–5136. [Google Scholar] [CrossRef]
- Felt, A.P.; Wang, H.J.; Moshchuk, A.; Hanna, S.; Chin, E. Permission re-delegation: Attacks and defenses. Usenix Symp. 2011, 22, 88. [Google Scholar]
- Arzt, S.; Rasthofer, S.; Fritz, C.; Bodden, E.; Bartel, A.; Klein, J.; Traon, Y.L.; Octeau, D.; McDaniel, P. Flowdroid: Precise context, flow, field, object-sensitive and lifecycle-aware taint analysis for android apps. Acm Sigplan Not. 2014, 49, 259–269. [Google Scholar] [CrossRef]
- Chin, E.; Felt, A.P.; Greenwood, K.; Wagner, D. Analyzing inter-application communication in android. In Proceedings of the 9th International Conference on Mobile Systems, Applications, and Services, Bethesda, MD, USA, 28 June–1 July 2011; pp. 239–252. [Google Scholar]
- Lu, L.; Li, Z.; Wu, Z.; Lee, W.; Jiang, G. Chex: Statically vetting android apps for component hijacking vulnerabilities. In Proceedings of the 2012 ACM Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 229–240. [Google Scholar]
- Demissie, B.F.; Ceccato, M.; Shar, L.K. Anflo: Detecting anomalous sensitive information flows in android apps. In Proceedings of the 2018 IEEE/ACM 5th International Conference on Mobile Software Engineering and Systems (MOBILESoft), Gothenburg, Sweden, 27 May–3 June 2018. [Google Scholar]
- Sadeghi, A.; Jabbarvand, R.; Ghorbani, N.; Bagheri, H.; Malek, S. A temporal permission analysis and enforcement framework for android. In Proceedings of the 40th International Conference on Software Engineering, Gothenburg, Sweden, 27 May–3 June 2018; pp. 846–857. [Google Scholar]
- Arp, D.; Spreitzenbarth, M.; Hubner, M.; Gascon, H.; Rieck, K.; Siemens, C.E.R.T. Drebin: Effective and explainable detection of android malware in your pocket. Ndss 2014, 14, 23–26. [Google Scholar]
- Institute for System Security—Technische Universität Braunschweig. The Drebin Dataset. Available online: https://www.sec.cs.tu-bs.de/~danarp/drebin/index.html (accessed on 1 September 2022).
- Enck, W.; Gilbert, P.; Han, S.; Tendulkar, V.; Chun, B.G.; Cox, L.P.; Jung, J.; McDaniel, P.; Sheth, A.N. Taintdroid: An information-flow tracking system for realtime privacy monitoring on smartphones. Acm Trans. Comput. Syst. 2010, 32, 393–407. [Google Scholar] [CrossRef]
- Dawoud, A.; Bugiel, S. Droidcap: Os Support for Capability-Based Permissions in Android. Ndss Symp. 2019. Available online: https://svenbugiel.github.io/publication/dawoud-19-ndss/dawoud-19-ndss.pdf (accessed on 5 October 2022).
- Xu, Y.; Witchel, E. Maxoid: Transparently confining mobile applications with custom views of state. In Proceedings of the Tenth European Conference on Computer Systems, New York, NY, USA, 21–24 April 2015; pp. 1–16. [Google Scholar]
- Jia, L.; Aljuraidan, J.; Fragkaki, E.; Bauer, L.; Stroucken, M.; Fukushima, K. Run-time enforcement of information-flow properties on android. In European Symposium on Research in Computer Security; Springer: Berlin/Heidelberg, Germany, 2013; pp. 775–792. [Google Scholar]
- Rubio-Medrano, C.E.; Hill, M.; Claramunt, L.M.; Baek, J.; Ahn, G.J. DyPolDroid: Protecting Users and Organizations from Permission-Abuse Attacks in Android. In International Conference on Secure Knowledge Management in Artificial Intelligence Era; Krishnan, R., Rao, H.R., Sahay, S.K., Samtani, S., Zhao, Z., Eds.; SKM 2021; Springer: Cham, Switzerland, 2021; pp. 23–36. [Google Scholar] [CrossRef]
- Conversational Actions. Intents. Available online: https://developers.google.com/assistant/conversational/intents (accessed on 5 October 2022).
- Google Developers Guide. Pendingintent. Available online: https://developer.android.com/reference/android/app/PendingIntent (accessed on 1 September 2022).
- Application Signing. Application Signing. Available online: https://source.android.com/security/apksigning#v1 (accessed on 1 September 2022).
- Ben Gruver. Baksmali. (Disassembler for the Dex Format Used by Dalvik). Available online: https://github.com/JesusFreke/smali/tree/master/baksmali (accessed on 1 September 2022).
- Ben Gruver. Smali. (Assembler for the Dex Format Used by Dalvik). Available online: https://github.com/JesusFreke/smali (accessed on 1 September 2022).
- Ben Gruver. Dexlib2. Available online: https://github.com/JesusFreke/smali/tree/master/dexlib2 (accessed on 1 September 2022).
- Tang, Y.; Pan, Z.; Pedrycz, W.; Ren, F.; Song, X. Viewpoint-Based Kernel Fuzzy Clustering With Weight Information Granules. IEEE Trans. Emerg. Top. Comput. Intell. 2022. [Google Scholar] [CrossRef]
- Gupta, N.; Ari, S.; Panigrahi, N. Change Detection in Landsat Images Using Unsupervised Learning and RBF-Based Clustering. IEEE Trans. Emerg. Top. Comput. Intell. 2021, 5, 284–297. [Google Scholar] [CrossRef]
- Roseline, S.A.; Geetha, S.; Kadry, S.; Nam, Y. Intelligent vision-based malware detection and classification using deep random forest paradigm. IEEE Access. 2020, 8, 206303–206324. [Google Scholar] [CrossRef]
- Hemalatha, J.; Roseline, S.A.; Geetha, S.; Kadry, S.; Damaševičius, R. An Efficient DenseNet-Based Deep Learning Model for Malware Detection. Entropy 2021, 23, 344. [Google Scholar] [CrossRef] [PubMed]
- Liberti, L.; Lavor, C.; Maculan, N.; Mucherino, A. Euclidean Distance Geometry and Applications. SIAM Rev. 2014, 56, 3–69. [Google Scholar] [CrossRef] [Green Version]
- Ghorbani, H. Mahalanobis Distance and Its Application for Detecting Multivariate Outliers. Facta Univ. Ser. Math. Inform. 2019, 34, 583–595. [Google Scholar] [CrossRef]
- Mahalanobis Distance. Available online: https://en.wikipedia.org/wiki/Mahalanobis_distance (accessed on 5 October 2022).
- Canadian Institute for Cybersecurity. Available online: https://www.unb.ca/cic/datasets/maldroid-2020.html (accessed on 1 September 2022).
- Hopkins Statistic. Available online: https://en.wikipedia.org/wiki/Hopkins_statistic/ (accessed on 1 September 2022).














| Static Features | Sample Values |
|---|---|
| Checksum | d17d80f58b36ebe71dec80fa5ae8542c |
| appPackageName | - |
| appName2 | - |
| appSize(KB) | 40,003 |
| TotalPermissions | 41 |
| minSDKVersion | 15 |
| targetSDKVersion | 26 |
| TotActivities | 1112 |
| TotServices | 40 |
| TotBroadcastReceivers | 51 |
| TotExposedActivities | 86 |
| TotExposedServices | 13 |
| TotExposedBroadcastReceivers | 57 |
| OutBroadcastTags | android.intent.action.SENDTO |
| android.intent.action.SEND | |
| InBroadcastTags | android.intent.action.BOOT_COMPLETED |
| android.net.wifi.WIFI_STATE_CHANGED | |
| androidnet.conn.CONNECTIVITY_CHANGE | |
| android.intent.action.PHONE_STATE | |
| android.intent.action.PACKAGE_REMOVED | |
| owner | - |
| issuer | - |
| serialnumber | 4e5b9304 |
| algorithm | SHAlwithRSA (weak) |
| bit | 1024-bit RSA key (weak) |
| version | 3 |
| Dynamic Features | Sample Values |
| noOfClz | 22,347 |
| noOfMethods | 89,943 |
| no0fIntents | 520 |
| noOfPendinglntents | 37 |
| FLAG_ONE_SHOT | 0 |
| FLAG_NO_CREATE | 0 |
| FLAG_CANCEL_CURRENT | 1 |
| FLAG_UPDATE_CURRENT | 30 |
| FLAG_IMMUTABLE | 0 |
| unsafePICreation | 2 |
| unsafeBroadcast | 2 |
| unsafePITransfer | 0 |
| NoOfProtectedBroadcast | 2 |
| UnsafeProtectedBroadcast | 0 |
| TotalBroadcast | 48 |
| Dataset | 1s | Nc | Cc | Uc | Im | %VulIn | %VulPI | %VulTR | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Drebin | 5546 | 1,338,542 | 7,174,900 | 168,444 | 16,072 | 367 | 92 | 3570 | 2056 | 12 | 963 | 3916 | 87 | 0.57 | 24.3653559 | 0.541314087 |
| SMS | 4796 | 160,287 | 794,577 | 61,700 | 14,044 | 2 | 1 | 6094 | 303 | 0 | 771 | 7755 | 0 | 1.249594814 | 55.21931074 | 0 |
| Adware | 1510 | 584,945 | 3,331,055 | 99,125 | 11,894 | 43 | 23 | 2573 | 4197 | 119 | 703 | 957 | 8 | 0.709205549 | 8.046073651 | 0.067260804 |
| Riskware | 4352 | 2,464,826 | 12,713,338 | 145,208 | 14,753 | 911 | 40 | 841 | 6101 | 13 | 1312 | 4380 | 5 | 0.903531486 | 29.68887684 | 0.033891412 |
| Banking | 2399 | 673,494 | 3,452,858 | 63,421 | 7157 | 824 | 13 | 578 | 1776 | 3 | 556 | 2489 | 26 | 0.876681225 | 34.77714126 | 0.363280704 |
| Benign | 4035 | 10,229,928 | 46,168,467 | 476,672 | 25,410 | 1662 | 502 | 3154 | 10,089 | 58 | 6570 | 2264 | 322 | 1.378306257 | 8.909878001 | 1.267217631 |
| Total | 22,638 | 15,452,022 | 73,635,195 | 1,014,570 | 89,330 | 3809 | 671 | 16,810 | 24,522 | 205 | 10,875 | 21,761 | 448 | 1.07188267 | 24.36023732 | 0.50151125 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Duraisamy Soundrapandian, P.; Subbiah, G. MULBER: Effective Android Malware Clustering Using Evolutionary Feature Selection and Mahalanobis Distance Metric. Symmetry 2022, 14, 2221. https://doi.org/10.3390/sym14102221
Duraisamy Soundrapandian P, Subbiah G. MULBER: Effective Android Malware Clustering Using Evolutionary Feature Selection and Mahalanobis Distance Metric. Symmetry. 2022; 14(10):2221. https://doi.org/10.3390/sym14102221
Chicago/Turabian StyleDuraisamy Soundrapandian, Pradeepkumar, and Geetha Subbiah. 2022. "MULBER: Effective Android Malware Clustering Using Evolutionary Feature Selection and Mahalanobis Distance Metric" Symmetry 14, no. 10: 2221. https://doi.org/10.3390/sym14102221