A New Secure and Anonymous Metering Scheme for Smart Grid Communications
Abstract
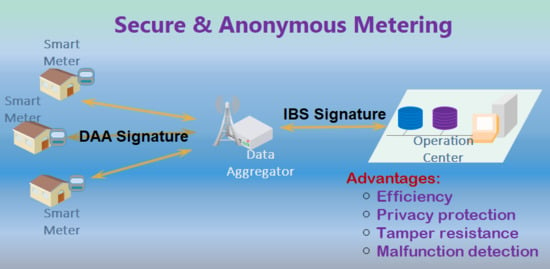
:1. Introduction
2. Methodology
2.1. Bilinear Maps
- Bilinearity: , .
- Non-degeneracy: , for all iff .
- Computability: , is efficiently computable.
- There exists an efficient and publicly computable isomorphism such that .
2.2. Mathematical Problem
2.3. System Model
2.4. Construction of Our Proposed Scheme
2.4.1. System Initialization
- Find a prime , and select an asymmetric bilinear group pair of order q to satisfy a pairing function as follows:along with the generators , , where is a computable isomorphism from to .
- Choose and select a system master key ; compute a system public key where
- Select secure hash functions , , .
- Pre-compute the following pairings:
- Output the system public key and master key
2.4.2. Membership Registration
A. Smart Meter Registration
- The OC randomly chooses a nonce and sends to SM.
- The TPM in the smart meter selects a secret key , and computes the associated public keyFinally, the TPM sends the proof message, and , to the OC.
- Upon receiving the and , the OC checks F against the RL to verify the correctness of . RL is a rogue list, which is set to be empty at the system setup, and will contain the invalid secret key of malfunctioning or rogue smart meters. Then, the OC computes a credential cre by calculating:A is a signature on the public key F (therefore on f). Then, the OC sends to SM.
- SM verifies the correctness of the credential cre such thatThus, SM gets a membership credential cre on its secret key f.
B. Data Aggregator Registration
2.4.3. Communications between the SM and DA
A. The Signing Protocol
B. The Verification Algorithm
2.4.4. Malfunctioning Meter Detection
A. The Linking Algorithm
B. The Tracing Protocol
- SM selects and computes by
- SM executes the proof of knowledge thatand sends the result to the tracer.
- The tracer accepts that the smart meter is not a malfunctioning one if it accepts in step 2. Otherwise, the tracer rejects the meter, and ensures that the present SM is the malfunctioning smart meter.
2.4.5. Communications between the DA and OC
A. Signing
B. Verification
3. Results
3.1. Security Results
- Correctness: According to the verification procedures in our proposed security protocol, the anonymous signature generated by a valid smart meter and the signature generated by an honest data aggregator can surely pass the verification.
- Data Integrity and Authenticity: The properties of integrity and authenticity require that the entity in the communications should be a valid registered membership, and that no attackers could tamper with or forge the data generated by the entity. In our scheme, all of the smart meters are equipped with a tamper-resistant TPM chip, which prevents meter data from being altered by the attacker. Meanwhile, secure DAA and IBS protocols are used in our scheme to ensure the authenticity. Without valid credentials, a smart meter cannot successfully sign the meter data or forge a valid signature. In addition, without a valid identity-based secret key, a fake data aggregator cannot produce a valid signature that can pass the verification by the operation center. Thus, our scheme satisfies data integrity and authenticity concerns.
- Anonymity: Anonymity is the privacy requirement of our scheme. It requires that each valid signature is unable to expose any of the information of the signer, and no one can distinguish whether two normal signatures are generated by the same signer. In fact, as described in Section 2.4.3, during the data upload, SM hides its credential and uses a pseudonym K instead of the real identity F; as a result, no adversary can recognize the identity of the data owner. Meanwhile, for any two different pairs and in signatures , if the adversary can determine whether they are generated by the same SM (i.e., determine whether , where , ), then it will break the decisional Diffie–Hellman(DDH) problem [51]. Thus, our scheme satisfies the requirement of anonymity.
- Malfunctioning Meter Traceability: As presented in Section 2.4.4, our scheme has the property of malfunctioning meter detection. If any two signatures are dishonestly generated by the SM, i.e., the SM signs a message twice in a time period—even though two such signatures can pass the verification—they can be linked and traced by the utilities.
3.2. Performance Results
- : The execution time of a bilinear pairing operation .
- : The execution time of a scalar multiplication in , .
- : The execution time of a modular exponentiation operation.
- : The execution time of the map-to-point function in .
- : The execution time of symmetric encryption or decryption.
- : The execution time of the hash function.
4. Discussion
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Khan, M.W.; Wang, J.; Ma, M.; Xiong, L.; Li, P.; Wu, F. Optimal energy management and control aspects of distributed microgrid using multi-agent systems. Sustain. Cities Soc. 2019, 44, 855–870. [Google Scholar] [CrossRef]
- Khan, M.W.; Wang, J.; Xiong, L.; Ma, M. Modelling and optimal management of distributed microgrid using multi-agent systems. Sustain. Cities Soc. 2018, 41, 154–169. [Google Scholar] [CrossRef]
- Gungor, V.C.; Lu, B.; Hancke, G.P. Opportunities and challenges of wireless sensor networks in smart grid. IEEE Trans. Ind. Electron. 2010, 57, 3557–3564. [Google Scholar] [CrossRef] [Green Version]
- Amin, S.M.; Wollenberg, B.F. Toward a smart grid: Power delivery for the 21st century. IEEE Power Energy Mag. 2005, 3, 34–41. [Google Scholar] [CrossRef]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C.; Cecati, C.; Hancke, G.P. Smart grid technologies: Communication technologies and standards. IEEE Trans. Ind. Inform. 2011, 7, 529–539. [Google Scholar] [CrossRef] [Green Version]
- Cecati, C.; Citro, C.; Piccolo, A.; Siano, P. Smart operation of wind turbines and diesel generators according to economic criteria. IEEE Trans. Ind. Electron. 2011, 58, 4514–4525. [Google Scholar] [CrossRef]
- Belvedere, B.; Bianchi, M.; Borghetti, A.; Nucci, C.A.; Paolone, M.; Peretto, A. A microcontroller-based power management system for standalone microgrids with hybrid power supply. IEEE Trans. Sustain. Energy 2012, 3, 422–431. [Google Scholar] [CrossRef]
- Mashayekh, S.; Stadler, M.; Cardoso, G.; Heleno, M. A mixed integer linear programming approach for optimal DER portfolio, sizing, and placement in multi-energy microgrids. Appl. Energy 2017, 187, 154–168. [Google Scholar] [CrossRef] [Green Version]
- Klaimi, J.; Rahim-Amoud, R.; Merghem-Boulahia, L.; Jrad, A. A novel loss-based energy management approach for smart grids using multi-agent systems and intelligent storage systems. Sustain. Cities Soc. 2018, 39, 344–357. [Google Scholar] [CrossRef]
- Liu, G.; Jiang, T.; Ollis, T.B.; Zhang, X.; Tomsovic, K. Distributed energy management for community microgrids considering network operational constraints and building thermal dynamics. Appl. Energy 2019, 239, 83–95. [Google Scholar] [CrossRef]
- De Rubeis, T.; Nardi, I.; Paoletti, D.; Di Leonardo, A.; Ambrosini, D.; Poli, R.; Sfarra, S. Multi-year consumption analysis and innovative energy perspectives: The case study of Leonardo da Vinci International Airport of Rome. Energy Convers. Manag. 2016, 128, 261–272. [Google Scholar] [CrossRef]
- Isa, N.M.; Tan, C.W.; Yatim, A. A comprehensive review of cogeneration system in a microgrid: A perspective from architecture and operating system. Renew. Sustain. Energy Rev. 2018, 81, 2236–2263. [Google Scholar] [CrossRef]
- Li, X.; Liang, X.; Lu, R.; Shen, X.; Lin, X.; Zhu, H. Securing smart grid: Cyber attacks, countermeasures, and challenges. IEEE Commun. Mag. 2012, 50, 38–45. [Google Scholar] [CrossRef]
- Lisovich, M.A.; Mulligan, D.K.; Wicker, S.B. Inferring personal information from demand-response systems. IEEE Secur. Priv. 2010, 8, 11–20. [Google Scholar] [CrossRef]
- Barbosa, P.; Brito, A.; Almeida, H. Defending against load monitoring in smart metering data through noise addition. In Proceedings of the 30th Annual ACM Symposium on Applied Computing, Salamanca, Spain, 13–17 April 2015; pp. 2218–2224. [Google Scholar]
- Fan, Z.; Kulkarni, P.; Gormus, S.; Efthymiou, C.; Kalogridis, G.; Sooriyabandara, M.; Zhu, Z.; Lambotharan, S.; Chin, W.H. Smart grid communications: Overview of research challenges, solutions, and standardization activities. IEEE Commun. Surv. Tutor. 2012, 15, 21–38. [Google Scholar] [CrossRef] [Green Version]
- Komninos, N.; Philippou, E.; Pitsillides, A. Survey in smart grid and smart home security: Issues, challenges and countermeasures. IEEE Commun. Surv. Tutor. 2014, 16, 1933–1954. [Google Scholar] [CrossRef]
- Pillitteri, V.Y.; Brewer, T.L. Guidelines for Smart Grid Cybersecurity; NIST Interagency/Internal Report (NISTIR)-7628 Rev 1; NIST: Gaithersburg, MD, USA, 2014.
- De Oliveira, F.B. On Privacy-Preserving Protocols for Smart Metering Systems; Springer: Berlin, Germany, 2015. [Google Scholar]
- Fouda, M.M.; Fadlullah, Z.M.; Kato, N.; Lu, R.; Shen, X.S. A lightweight message authentication scheme for smart grid communications. IEEE Trans. Smart Grid 2011, 2, 675–685. [Google Scholar] [CrossRef] [Green Version]
- Chim, T.W.; Yiu, S.M.; Li, V.O.; Hui, L.C.; Zhong, J. PRGA: Privacy-preserving recording & gateway-assisted authentication of power usage information for smart grid. IEEE Trans. Dependable Secur. Comput. 2014, 12, 85–97. [Google Scholar]
- Li, H.; Lin, X.; Yang, H.; Liang, X.; Lu, R.; Shen, X. EPPDR: An efficient privacy-preserving demand response scheme with adaptive key evolution in smart grid. IEEE Trans. Parallel Distrib. Syst. 2013, 25, 2053–2064. [Google Scholar] [CrossRef] [Green Version]
- Jo, H.J.; Kim, I.S.; Lee, D.H. Efficient and privacy-preserving metering protocols for smart grid systems. IEEE Trans. Smart Grid 2015, 7, 1732–1742. [Google Scholar] [CrossRef]
- Liu, Y.; Guo, W.; Fan, C.I.; Chang, L.; Cheng, C. A practical privacy-preserving data aggregation (3PDA) scheme for smart grid. IEEE Trans. Ind. Informatics 2018, 15, 1767–1774. [Google Scholar] [CrossRef]
- Xue, K.; Yang, Q.; Li, S.; Wei, D.S.; Peng, M.; Memon, I.; Hong, P. PPSO: A privacy-preserving service outsourcing scheme for real-time pricing demand response in smart grid. IEEE Internet Things J. 2018, 6, 2486–2496. [Google Scholar] [CrossRef]
- Zhang, S.; Zheng, T.; Wang, B. A privacy protection scheme for smart meter that can verify terminal’s trustworthiness. Int. J. Electr. Power Energy Syst. 2019, 108, 117–124. [Google Scholar] [CrossRef]
- Mustafa, M.A.; Cleemput, S.; Aly, A.; Abidin, A. A secure and privacy-preserving protocol for smart metering operational data collection. IEEE Trans. Smart Grid 2019, 10, 6481–6490. [Google Scholar] [CrossRef] [Green Version]
- Barbosa, P.; Brito, A.; Almeida, H.; Clauß, S. Lightweight privacy for smart metering data by adding noise. In Proceedings of the 29th Annual ACM Symposium on Applied Computing, Gyeongju, Korea, 24–28 March 2014; pp. 531–538. [Google Scholar]
- McLaughlin, S.; McDaniel, P.; Aiello, W. Protecting consumer privacy from electric load monitoring. In Proceedings of the 18th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 17–21 October 2011; pp. 87–98. [Google Scholar]
- Zhao, J.; Jung, T.; Wang, Y.; Li, X. Achieving differential privacy of data disclosure in the smart grid. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 504–512. [Google Scholar]
- Zhu, L.; Zhang, Z.; Qin, Z.; Weng, J.; Ren, K. Privacy protection using a rechargeable battery for energy consumption in smart grids. IEEE Netw. 2016, 31, 59–63. [Google Scholar] [CrossRef]
- Zargar, S.H.M.; Yaghmaee, M.H. Privacy preserving via group signature in smart grid. In Proceedings of the Electric Industry Automation Congress (EIAC), Mashhad, Iran, 13–14 February 2013. [Google Scholar]
- Kishimoto, H.; Yanai, N.; Okamura, S. An Anonymous Authentication Protocol for the Smart Grid. In Smart Micro-Grid Systems Security and Privacy; Springer: Berlin, Germany, 2018; pp. 29–52. [Google Scholar]
- Zhao, J.; Liu, J.; Qin, Z.; Ren, K. Privacy protection scheme based on remote anonymous attestation for trusted smart meters. IEEE Trans. Smart Grid 2016, 9, 3313–3320. [Google Scholar] [CrossRef]
- Diao, F.; Zhang, F.; Cheng, X. A privacy-preserving smart metering scheme using linkable anonymous credential. IEEE Trans. Smart Grid 2014, 6, 461–467. [Google Scholar] [CrossRef]
- Gong, Y.; Cai, Y.; Guo, Y.; Fang, Y. A privacy-preserving scheme for incentive-based demand response in the smart grid. IEEE Trans. Smart Grid 2015, 7, 1304–1313. [Google Scholar] [CrossRef]
- Efthymiou, C.; Kalogridis, G. Smart grid privacy via anonymization of smart metering data. In Proceedings of the First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 238–243. [Google Scholar]
- Stegelmann, M.; Kesdogan, D. Gridpriv: A smart metering architecture offering k-anonymity. In Proceedings of the IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25–27 June 2012; pp. 419–426. [Google Scholar]
- Finster, S.; Baumgart, I. Pseudonymous smart metering without a trusted third party. In Proceedings of the 2013 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Melbourne, VIC, Australia, 16–18 July 2013; pp. 1723–1728. [Google Scholar]
- LeMay, M.; Gross, G.; Gunter, C.A.; Garg, S. Unified architecture for large-scale attested metering. In Proceedings of the 40th Annual Hawaii International Conference on System Sciences (HICSS’07), Waikoloa, HI, USA, 3–6 January 2007; p. 115. [Google Scholar]
- Brickell, E.; Li, J. A pairing-based DAA scheme further reducing TPM resources. In Proceedings of the International Conference on Trust and Trustworthy Computing, Berlin, Germany, 21–23 June 2010; pp. 181–195. [Google Scholar]
- Chen, L.; Li, J. Flexible and scalable digital signatures in TPM 2.0. In Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013; pp. 37–48. [Google Scholar]
- Barreto, P.S.; Libert, B.; McCullagh, N.; Quisquater, J.J. Efficient and provably-secure identity-based signatures and signcryption from bilinear maps. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Chennai, India, 4–8 December 2005; pp. 515–532. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar]
- Boneh, D.; Boyen, X.; Shacham, H. Short group signatures. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 2004; pp. 41–55. [Google Scholar]
- Boneh, D.; Boyen, X. Short signatures without random oracles. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 2–6 May 2004; pp. 56–73. [Google Scholar]
- Schnorr, C.P. Efficient identification and signatures for smart cards. In Proceedings of the Conference on the Theory and Application of Cryptology, Santa Barbara, CA, USA, 20–24 August 1989; pp. 239–252. [Google Scholar]
- Fiat, A.; Shamir, A. How to prove yourself: Practical solutions to identification and signature problems. In Proceedings of the Conference on the Theory and Application of Cryptographic Techniques, Linköping, Sweden, 20–22 May 1986; pp. 186–194. [Google Scholar]
- Pointcheval, D.; Stern, J. Security proofs for signature schemes. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Saragossa, Spain, 12–116 May 1996; pp. 387–398. [Google Scholar]
- Camenisch, J.; Shoup, V. Practical verifiable encryption and decryption of discrete logarithms. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 2003; pp. 126–144. [Google Scholar]
- Boneh, D. The decision diffie-hellman problem. In Proceedings of the International Algorithmic Number Theory Symposium, Portland, OR, USA, 21–25 June 1998; pp. 48–63. [Google Scholar]
- Miyaji, A.; Nakabayashi, M.; Takano, S. New explicit conditions of elliptic curve traces for FR-reduction. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2001, 84, 1234–1243. [Google Scholar]
- Scott, M. On the efficient implementation of pairing-based protocols. In Proceedings of the IMA International Conference on Cryptography and Coding, Cirencester, UK, 17–19 December 2011; pp. 296–308. [Google Scholar]
- Brickell, E.; Camenisch, J.; Chen, L. Direct anonymous attestation. In Proceedings of the 11th ACM Conference on Computer and Communications Security, Washington, DC, USA, 25–29 October 2004; pp. 132–145. [Google Scholar]
- Trusted Computing Group. TPM 1.2 Main Specification. Available online: https://trustedcomputinggroup.org/resource/tpm-main-specification (accessed on 3 December 2019).
- Trusted Computing Group. TPM 2.0 Library Specification. Available online: https://www.idtechex.com/research/reports/rfid-forecasts-players-and-opportunities-2018-2028-000642.asp (accessed on 3 December 2019).






| Notations | Descriptions |
|---|---|
| DAA | Direct anonymous attestation |
| IBS | Identity-based signature |
| SM | Smart meter |
| DA | Data aggregator |
| OC | Operation center |
| TPM | Trusted platform module |
| SM | The i-th smart meter |
| DA | The j-th data aggregator |
| TPM | The TPM chip embedded in SM |
| ID | The identity of DA |
| ms | millisecond |
| n | The total number of SMs in a domain |
| m | The total number of DAs |
| Bilinear map | |
| ,, | Multiplicative cyclic groups |
| k | The security parameter |
| q | Prime order of and |
| A generator of | |
| A generator of | |
| A computable isomorphism from to | |
| gsk | The system master key |
| gpk | The system public key |
| f | The secret key of the SM |
| F | The public key of the SM |
| cre | The credential of the SM |
| A secure hash function that | |
| A secure hash function that | |
| A secure hash function that | |
| RL | The list of rogue/malfuctioning smart meters |
| TS | The current timestamp |
| msg | Metering data of SM |
| M | Aggregated meter data of DA |
| Identity-based private key of DA | |
| M | The entire meter consumption of the OC |
| J | A base point of elliptive curve |
| K | Pseudonym of the SM |
| T | The blind credential of the SM |
| Concatenation operation | |
| The set of all binary strings of length l | |
| RSA | The public-key encryption algorithm |
| AES-256 | The symmetric encryption–decryption algorithm |
| SHA-256 | The hash function |
| T | T | T | T | T | T |
|---|---|---|---|---|---|
| 1.238 | 0.325 | 0.286 | 0.029 | 0.00779 | 0.00198 |
| Scheme | Cost on SM | Time (ms) | Cost on DA | Time (ms) |
|---|---|---|---|---|
| [34] | × | ≈0.2938 t + 0.8639 | ≈0.862 | |
| Ours | ≈3.561 | ≈3.769 |
| Cost on DA | Time (ms) | Cost on OC | Time (ms) |
|---|---|---|---|
| ≈0.994 | ≈1.907 |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, S.; Zhang, F.; Lin, H.; Tian, Y. A New Secure and Anonymous Metering Scheme for Smart Grid Communications. Energies 2019, 12, 4751. https://doi.org/10.3390/en12244751
Xie S, Zhang F, Lin H, Tian Y. A New Secure and Anonymous Metering Scheme for Smart Grid Communications. Energies. 2019; 12(24):4751. https://doi.org/10.3390/en12244751
Chicago/Turabian StyleXie, Shaohao, Fangguo Zhang, Huizhi Lin, and Yangtong Tian. 2019. "A New Secure and Anonymous Metering Scheme for Smart Grid Communications" Energies 12, no. 24: 4751. https://doi.org/10.3390/en12244751