1. Introduction
In recent years, the demand for wireless sensor networks has increased for many industrial applications such as fault diagnosis and monitoring, surveillance monitoring, industrial control systems, commodity consumption monitoring and plant automation, etc. [
1]. In addition, in industrial applications, wireless sensor networks have many medical, military, civil and environmental applications as well body area network monitoring [
2], civil structure monitoring [
3], target tracking in battlefields [
4], earthquake and flood monitoring [
5], forest fire monitoring [
6], etc.
The technological progression in the field of highly integrated digital sensor electronics, small scale microprocessors, low power transceivers and radio frequency devices, collectively resulted in the design of efficient wireless sensors [
7]. These wireless sensor devices are responsible for sensing the change in required physical phenomena of their surrounding environment with the help of a small microprocessor, radio transceiver, a few transducers and a low capacity battery [
7]. The transducers or sensors perform the specific type of sensing in the surrounding environment and pass the sensing information to a microprocessor for further processing of sensed data [
7]. A wireless sensor’s radio transceiver is used to transmit and receive the sensed data to/from adjacent wireless sensors or to/from the sink node, depending upon the location of the wireless sensor in the field [
7]. Due to low battery capacity, wireless sensor nodes have to adjust their sleep–awake cycle (or working–sleeping cycle) according to scenario requirements in order to maximize the network life time and minimize the overall network delay [
8]. The possible existence of these miniaturized wireless sensor devices motivated researchers to emphasize the significance of wireless sensor node collaboration for data sensing, data collection and aggregation purposes which resulted in the discovery of an emerging field known as wireless sensor network (WSN). The purpose of deploying multiple wireless sensor nodes in a field is to have collaboration between these sensor nodes to achieve a shared goal with the help of sensing, data aggregation and data sharing between wireless sensor nodes [
9].
The frequent transmission failures, electricity theft and congestion problems in traditional electric grids lead to the consideration that traditional electric grids are insecure and inefficient in terms of energy management. In order to eradicate these problems, we need to incorporate state-of-the-art bidirectional communication interfaces, automated control systems and distributed computing capabilities in our current grid, which will improve energy efficiency, reliability, security and agility in our electric grid [
10]. Furthermore, a highly integrated next generation system is needed in which electricity service providers, distributors and prosumers are well aware of real-time energy requirements and capabilities; the system which offers high performance computing, security, scalability, reliability and security with state-of-the-art communication network infrastructure is our “smart grids” (SGs) [
10,
11]. For better realization of SGs, we need to distribute and gather information remotely and in a timely manner from different phases of our SGs (i.e., generation, transmission, distribution and consumption) [
10,
11,
12]. The data acquisition from different devices deployed in the neighborhood area network (NAN) can be efficiently achieved by incorporating WSN in SGs. The upgradation of contemporary electric grids to SGs could be supported by self-governing and self-organizing features of WSN [
13]. A traditional electric grid needs installation of costly and inefficient wired monitoring systems, expensive communication cables and a high-maintenance budget [
10]. On the other hand, SGs with the help of wireless monitoring sensors and proper fault diagnostics, can remarkably reduce power losses and long-term maintenance budget and does not require expensive communication cables, thus enhancing the system’s reliability and efficiency [
13].
Efficient energy utilization and network lifetime are considered as the main design parameters in the previous research conducted for WSN [
8]. Additionally, the feasibility of mobility usage in WSN as demonstrated in [
14] can improve the network lifetime by replacing the traditional static wireless sensor nodes with mobile wireless sensor nodes. Similarly, if the center node (or sink) is mobile, it needs more computation power in comparison to other sensor nodes [
14]. The mobility and more computation power will drain out the battery of that sink node after a few rounds of sensing and aggregation, and its energy should be replenished in a timely manner. The mobility of a sink node can be controlled or randomly planned depending upon the particular scenario of the WSN and in this way, many traditional problems like hot-spot problem [
14] can be avoided. With reference to [
15], researchers have proposed a working–sleeping cycle strategy in which free nodes go to sleep to save their battery power and have a proper node scheduling scheme for efficient data transmission. These node scheduling schemes were categorized as synchronous and asynchronous working–sleeping cycle, which means that the network lifetime can be prolonged by changing the node scheduling schemes in accordance with the scenarios. Although it can affect the link stability between sensor nodes, it also creates an opportunistic node connection to exist between nodes due to asynchronous working–sleeping scheduling.
According to [
16,
17,
18,
19,
20], Opportunistic Routing (OR) is a paradigm for wireless networks which benefit from broadcast characteristics of a wireless medium by selecting multiple nodes as candidate forwarders, to improve network performance. In [
18,
19,
20] a set of nodes are selected as potential forwarders and the nodes in the selected set forward the packet according to some criteria after they receive the packet. This group of nodes in OR is called a candidate set (CS). The performance of OR depends on several key factors such as OR metric, candidate selection algorithm and candidate coordination method. Boukerche et al. in [
20] discussed the basic function of OR by highlighting its ability to overhear the transmitted packet and to coordinate among relaying nodes. In OR, by using a dynamic relay node to forward the packet, the transmission reliability and network throughput can be increased. Thus, the term “Opportunistic Routing” can be defined as the routing scheme in which the next best forwarder is dynamically selected with respect to OR metric, candidate selection algorithm and candidate coordinate method as in [
18,
19,
20].
The reasons why opportunistic node connections exist in WSNs can be summarized as follows:
WSNs are often deployed in harsh environments (smart grids NAN in our case), where wireless signals are susceptible to interference, thus causing link instability [
21,
22], further leading to opportunistic node connections;
The sink node mobility usually leads to intermittent links in the network, resulting in opportunistic node connections [
21];
Due to the limited energy of the nodes, the sensor nodes adopt an asynchronous working–sleeping cycle strategy to save energy and accordingly, the adjacent nodes may not be able to communicate with each other continuously as in [
22], thus bringing about opportunistic node connections.
By utilizing asynchronous working–sleeping cycle strategy, multiple nodes in WSNs can apply the concept of OR by overhearing their working neighbor’s transmission. A set of potential forwarders can be created using opportunistic connection random graph (OCRG) and formation of a spanning tree can be used to demonstrate that the candidate nodes in OR will forward the packet according to some criteria (i.e., optimal link and path connectivity calculations in our case).
However, the sensed data being generated as a result of deploying a WSN in a NAN of SGs might have different attributes like delay tolerance and delay sensitivity [
13]. For example, the monitoring data (e.g., power load) generated by a sensor network which is part of a SG can always be delay sensitive and should be transmitted to the data processing (or sink) node within certain time limits thereby increasing the bandwidth requirements, whereas the control data (e.g., changing power load) generated by the sensor network in SGs can often be considered as delay tolerant data and is not required to be received by the data processing (or sink) node immediately [
13]. Keeping in view the system requirements of SGs, parameters like energy consumption, mobility, network lifetime, delay and bandwidth can be treated as performance metrics for effective use of the WSN in SGs.
Many routing techniques specifically designed for WSNs have been proposed in [
23,
24,
25]. Likewise, the multipath routing protocols according to [
26] have been proposed for WSNs. These multipath routing protocols use multiple paths for data delivery, and thus improve the network reliability and robustness. In this paper, we propose an energy efficient and multipath opportunistic node connection routing protocol for WSNs in NANs to achieve load balancing through splitting up traffic in terms of real-time and non-real-time across multi-disjoint paths and energy consumption balance through asynchronous working–sleeping cycle of sensor nodes.
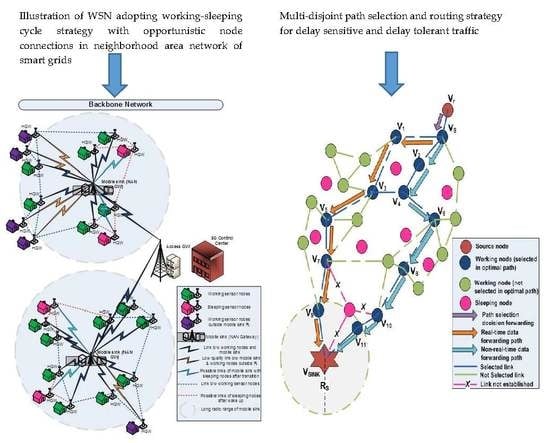
Figure 1 demonstrates the wireless sensor networks deployed in the NAN of SGs in which our NAN gateway is actually the mobile sink. The opportunistic node connections between mobile sink sensor nodes and between adjacent sensor nodes can be clearly seen in
Figure 1.
As a reflection of opportunistic node connectivity caused by asynchronous working–sleeping cycle strategy, OCRG is constructed in which a probe message forwarding mechanism is used for each node to forward the information to the mobile sink node [
27]. Additionally, EMOR utilizes the residual energy, availability of the node’s buffer size, working–sleeping cycle of sensor nodes and link quality factor to calculate the optimal link and path connectivity for both real-time and non-real-time traffic and assigns multi-disjoint paths to them accordingly.
The rest of the paper is organized as follows:
Section 2 describes the related research work conducted for WSN routing protocols in SGs and various other applications. System modeling is presented in
Section 3. EMOR protocol design for WSNs in NAN is presented in
Section 4. Performance evaluation and simulation results can be depicted from
Section 5. Finally,
Section 6 and
Section 7 briefly discuss the paper and provide some future research directions.
2. Related Research Work
Keeping in view the need for a more efficient and robust electric grid, a conceptual framework was proposed by the National Institute of Standards and Technology (NIST) in SGs Interoperability Standards Roadmap [
28,
29]. According to this conceptual framework, there is a need to have an inter domain and intra domain communication between key building blocks like operations, markets, service providers, generation, transmission, distribution and consumer [
28,
29]. The NIST framework states that SGs should support the information flow and electrical flow between all key building blocks. Information flow includes data acquisition, data processing and data dissemination between the desired energy subsystems of SGs, while the electrical flow deals with the generation, transmission and distribution of energy [
29]. The main objective of information flow is to monitor and control the energy whereas the electrical flow is responsible for power delivery, demand and asset optimization, etc. [
29].
In [
30,
31,
32], several key technologies have been identified by the National Energy Technology Laboratory (NETL) for SGs:
- (1)
Full-duplex and high-speed communication infrastructure for the information exchange between different SG entities.
- (2)
State-of-the-art sensing network infrastructure which will be responsible for the measurement and relaying of physical data. This sensor network can be used to prevent power theft, improve demand response, etc.
- (3)
Fabrication of components related to power electronics, superconductivity and energy storage should be needed based on the contemporary research being conducted for SGs.
- (4)
Seamless and real-time decision making at the prosumer end should be possible by improving the prosumer interface with operations, markets and service providers.
The general overview of SGs concept is presented in [
11,
12]. The communication architecture and application needs of SGs are explained in detail in [
30]. Moreover, the mechanisms for data collection and SGs sensing network is surveyed in [
13] and strategies for improving information flows in SGs is mentioned in [
33]. Technologies like high speed communication network architecture for SGs have been studied in [
30]. Due to the decentralized and lightweight architecture of WSNs, it can be efficiently used in SGs and micro-grids [
13]. Erol-Kantarci et al. in [
33] presented that WSNs can be used in various SG applications like generation, transmission, distribution and consumption as the WSN can deliver the information needed by the intelligent algorithms running in the control center of SGs. An overview of opportunities and challenges of WSNs in SGs is presented in [
34]. Likewise, different researchers have focused on proposing different routing protocols for WSNs based on parameters like network lifetime, delay, bandwidth, packet to delivery ratio and node mobility [
23,
24,
25,
26]. As mentioned in a detailed survey for energy efficient and energy balanced routing protocols for a WSN [
35], most of these protocols emphasize on improving energy consumption during network transmission activities but very few researches can be found about improvement in energy consumption with node mobility.
In a typical WSN topology, all nodes including the sink nodes are static. This leads to a situation in which the adjacent or neighboring nodes of the sink node deplete their limited battery powers as they have to participate in managing more traffic loads for forwarding the sensing data to the sink node as compared to the nodes which are far from the sink node. This typical scenario is known as hot-spot problem and adversely affects the network lifetime in any WSN application [
14,
15]. For this particular reason, the node mobility concept is introduced by many researchers, which exploits the movement of the sink node in the WSN to overcome the hot-spot problem [
36,
37]. As the location of the neighboring nodes around the sink node are changed due to movement of the sink node, the probability of a hot-spot problem is reduced and network lifetime is improved due to a more even distribution of energy consumption in the surrounding nodes [
37]. Keeping in view the node mobility, researchers have worked on the path formation for mobile sinks in [
37,
38,
39] based on the predefined, controlled and random path selection procedures. In [
40], Alghamdi et al. proposed a new routing aware algorithm to detect malicious nodes in a concealed data aggregation for WSNs to highlight the significance of data aggregation in WSNs by reducing communication overhead of sensor nodes.
All these previous researches were formulated to equalize the energy consumption of nodes, but they are not able to prolong the network lifetime. Thus, an emerging concept “utilization of working–sleeping cycle of nodes” was introduced to improve the energy consumption of nodes and overall network lifetime [
22]. The working–sleeping cycle can be segmented into two categories—synchronous and asynchronous working–sleeping cycles. Authors in [
41,
42] revealed that synchronous working–sleeping cycle could help in achieving improvement in energy consumption. However, the synchronization problem needed significant contributions. Thus in [
43], Ng et al. proposed an energy efficient synchronization algorithm in which adaptive adjustment of the traffic and wakeup period could improve energy consumption through counter-based and exponential-smoothing algorithms. In addition to it, some researchers also explored asynchronous working–sleeping cycle in which all nodes have independent working–sleeping schedules depending on the network connectivity requirements in terms of traffic coverage area [
16,
17]. Mukherjee et al. also proposed an asynchronous working–sleeping technique while focusing on network coverage by maintaining a minimum number of awake nodes [
44]. As a result of working–sleeping cycle strategy, opportunistic node connections will be established between sensor nodes and the mobile sink which can further lead to link instability. Therefore, we need a random graph theory to model these kinds of opportunistic node connections in the WSN. Mostafaei et al. proposed reliable routing with distributed learning automaton (RRDLA) algorithm, which considers dynamics of links in finding a path from a source to a destination by considering Quality of Service (QoS) constraints such as end-to-end reliability and delay [
45]. Ben Fradj et al. in [
46] presented a new opportunistic routing protocol called energy-efficient opportunistic routing protocol using a new forward list (EEOR-FL) aiming to balance energy consumption and maximize the network lifetime by calculating the list of candidates. Sadatpour et al. proposed a new collision-aware opportunistic routing protocol abbreviated as SCAOR for highways by utilizing cluster-based scheduling algorithms [
47].
Kenniche et al. in [
48] indicated that WSN modeling in the case of working–sleeping cycle strategy and opportunistic node connections can be modeled using a random geometric graph in which a set of vertices represent sensor nodes and a set of edges represent links between those vertices or sensor nodes. In reference [
49], Norman et al. proposed a novel random graph modeling for heterogeneous sensor networks based on different transmission ranges and a new routing metric. Referring to [
50], in which Ren et al. focused on the challenges and weaknesses of using random graph theory for modeling WSN, they thus proposed a new weighted topology model for WSN based on the random geometric theory. In [
51], Fu et al. developed an optimal policy for connection between source and destination nodes in random WSN topology using random graph. For this policy to be implemented correctly, an energy efficient probe message forwarding mechanism was proposed. After analyzing the source information in the received probe message, the mobile sink calculates the link connectivity between any two adjacent nodes after determining their neighbor relationships. Thus, an opportunistic connection random graph can be constructed.
As SGs require real-time (delay sensitive) and non-real-time (delay tolerant) traffic being routed through the WSN while minimizing the energy consumption and increasing the network lifetime, we need to utilize the WSN routing protocol which can offer energy efficiency and multi-disjoint path routing. Keeping in view these SGs requirements, Dulman et al. in [
52] discussed the trade-offs between traffic overhead and reliability in multi-path routing for WSN. In [
35], the authors discussed the taxonomy of cluster-based routing protocols for WSN, with respect to energy efficient and energy balance routing protocols. Ben-Othman et al. discussed the energy efficient and QoS based routing protocol in [
53]. Mostafaei et al. in [
54] investigated the problem of self-protection in WSNs and devised the Self Protection Learning Automaton (SPLA) algorithm in which sensing graph of the network plays the main role in finding the minimum number of nodes to protect the nodes. The proposed solution takes advantage of irregular cellular learning automaton (ICLA) to properly schedule the sensors into either an active or idle state. In [
53], researchers proposed an energy efficient and QoS-based multi-path routing protocol with disjoint paths for real-time and non-real-time traffic management. In [
55], Liang et al. presented a novel routing optimization technique based on improvement in Low Energy Adaptive Clustering Hierarchy (LEACH) in WSNs. According to this novel routing optimization technique, energy efficiency per unit node per round can be achieved and network lifetime can be prolonged. In our proposal, we utilized certain ideas from the previous routing protocols in WSN and proposed a detailed solution for optimally tackling the problems like energy consumption and network lifetime enhancement through multi-disjoint path opportunistic node modeling using random graph theory for delay-tolerant and delay-sensitive data in SGs NAN.
4. EMOR Protocol Design for WSN in NAN
The following five phases reflect the proposed design of EMOR for WSN deployed in NAN.
4.1. Initialization Phase
It is assumed that the mobile sink node can start the data collection anywhere and anytime in the network by broadcasting a message which contains the sink ID (SID) and data collection duration. Upon receiving the message from the mobile sink, the sensor nodes within long radio range
Rl obtain the data collection duration the sink and start calculating their working schedule (based on the working–sleeping cycle) and status transition frequency (i.e., switching from working to sleeping and vice versa), within this particular data collection duration. In case the sensor node is not working (sleeping state), then it can participate in the next data collection period when the sink node broadcasts the same message again to facilitate the sleeping sensor nodes and acquisition of probe messages from the new sensor nodes. Here, we have assumed that the relative signal strength indication (RSSI) parameter can be used to estimate the distance between the mobile sink and sensor nodes. In order to minimize the energy consumption, we employed the expected optimal hops (EOH) approach. EOH can be defined as the number of hops needed to forward a probe message from any node to the mobile sink node with minimum energy consumption [
22]. According to [
22], EOH can be expressed as:
where
E is the basic energy consumed during transmission and reception per bit,
is the energy consumed by the transmission amplifier,
is the distance between node
Vi and
VSINK and
is the expected optimal hops of node
Vi needed to select proper forwarders to the mobile sink with minimum energy consumed.
4.2. Probe Message Forwarding Mechanism in Data Collection Scope
All sensor nodes within long radio range
Rl which received the broadcast message from the mobile sink, need to send a data set comprising of information such as source ID, status transition frequency, working–sleeping schedule and all neighbor IDs to the mobile sink node during the data collection period. The format of probe message being forwarded to the mobile sink can be seen from
Table 1.
The length of the probe message is 120 bits in which the source ID occupies 10 bits, working–sleeping schedule occupies 15 bits, status transition frequency and neighbor IDs have 10 bits each, sink ID has 10 bits, forwarders ID has 60 bits and EOH contains 5 bits. The “Source ID” represents the ID of the node sending the message to the mobile sink. The “Working–Sleeping Schedule” represents the information about whole working time and whole sleeping time of the respective node. “Status Transition Frequency” provides information about the transitions from working mode to sleeping mode and vice versa of the sensor node. “Neighbor IDs” includes the ID list of neighboring nodes to the source node. If there is no neighbor or all neighboring nodes are in sleeping mode, the “Neighbor IDs” field remains empty. Moreover, the “Sink ID” is related to mobile sink’s SID and is used to indicate that the probe message being forwarded from the sensor node is specifically targeted for the desired sink node in case of multiple mobile sinks present in the network. “Forwarders ID” stores the IDs of nodes which have already forwarded this probe message to the mobile sink. This field is updated when a new node forwards this probe message to the mobile sink and adds its ID in the forwarders ID list. Likewise, “EOH” field stores the value of expected optimal hops needed for the source ID message to reach the sink node. As this probe message can be generated by any sensor node within the radio range
Rl of the mobile sink, so it’s quite probable that different working–sleeping schedules and status transition frequencies of sensor nodes can lead to inefficient probe message forwarding. Therefore, only the nodes that have received the probe message can participate in this forwarding mechanism. For example, for an intermediate node
VS receiving the probe message from one of its neighbors
Vr as shown in
Figure 3, the first step would be to check its own ID in the “Forwarders ID” field. If the probe message was not forwarded by this node
VS, it will add its ID to “Forwarders ID” field, determine the total number of forwarders (TNF) for this probe message and then calculate (EOH-TNF). Now it will check the “Neighbor IDs” field and see which neighbor’s EOH is closest to (EOH-TNF) as an optimal forwarder.
Since the asynchronous working–sleeping cycle strategy is used in sensor nodes, if any sensor node
VS receives the probe message from its surrounding node
Vr, it will forward the probe message to one of its neighbors only if that neighbor node is in working mode. Likewise, it will not forward the probe message if there is no neighboring node or the neighbor is in sleeping mode. The probe message receiving and forwarding mechanism based on asynchronous working–sleeping cycle of nodes is depicted in
Figure 3. Algorithm 1 provides the details about probe message forwarding mechanism.
| Algorithm 1: Initialization and Probe Message Forwarding Mechanism in EMOR |
Input:- 1.
Mobile sink broadcasting SID and data collection duration to all nodes within Rl - 2.
Sensor nodes within Rl receive the data collection message
Output:- 3.
Select neighbor which is optimal forwarder
Begin:- 4.
Calculate the working–sleeping cycle and status transition frequencies - 5.
Estimate the distance between sensor node and mobile sink using RSSI - 6.
Calculate EOH based on distance estimation - 7.
Determine the optimal forwarders based on the following criteria: - 8.
When an intermediate working node Vs receives the mobile sink message - 9.
if (Vs has not forwarded the probe message to any of its neighbors), then - 10.
Add Vs source ID in the forwarders ID list and calculate total number of forwarders (TNF) - 11.
Compute - 12.
if (Vs has working neighbors), then - 13.
Check EOH of all of its working neighboring nodes - 14.
if , then - 15.
Select the neighbor as an optimal forwarder - 16.
end if - 17.
endif - 18.
else if (Vs has already forwarded probe message to neighbor node Vt but receives it again), then - 19.
Explore the working neighbors other than Vt that have not forwarded the message yet - 20.
Remove the recently added source IDs of Vs, Vt from forwarders ID list - 21.
Add Vs source ID in the forwarders ID list and calculate total number of forwarders (TNF) - 22.
Compute - 23.
if (Vs has working neighbors other than Vt), then - 24.
Check EOH of working neighboring nodes other than Vt - 25.
if , then - 26.
Select the neighbor as an optimal forwarder - 27.
end if - 28.
end if - 29.
endif - 30.
if (all Vs neighbors are sleeping), then - 31.
Stop forwarding the probe message - 32.
Wait for the next data collection by sink node. - 33.
end if
|
4.3. Construction of Opportunistic Connection Random Graph
The construction of OCRG is dependent on the asynchronous working–sleeping cycle of sensor nodes and additional source information received within probe message forwarding during the initialization phase. In order to construct an OCRG, we assumed that the mobile sink is always in working mode and any sensor node within the short radio range
RS of the mobile sink can communicate with the mobile sink at any time. Furthermore, we proposed a data set
D(S,Ns,W/S,FST,RE,BS,S/N) consisting of source (
S) and its neighboring nodes (
NS) information, working–sleeping cycle schedule (
W/S), status transition frequencies (
FST) for every sensor node, residual energy of every sensor node after every round of communication (
RE, buffer size (
BS) and signal-to-noise ratio
(S/N)) of every sensor node with its adjacent nodes. Using this data set
D(S,Ns,W/S,FST,RE,BS,S/N), we analyzed the opportunistic connection between any adjacent sensor nodes which are in working mode. Additionally, for EMOR, the link connectivity between adjacent nodes is dependent on asynchronous working–sleeping cycle
W/S, status transition frequencies
FST of the adjacent nodes, residual energies of the adjacent nodes
RE, remaining buffer size of the adjacent nodes to cache the sensory data and link quality factor between adjacent nodes in terms of signal-to-noise ratio
S/N. More status transitions of a node will lead to an improvement in its link connectivity with the adjacent node as the probability of establishing a link connection will increase. Keeping in view the data set
D(S,Ns,W/S,FST,RE,BS,S/N), the time-frequency parameter
TFViVj of link connectivity
LViVj can be calculated as:
where
WVi and WVj are the whole working time of the adjacent nodes
Vi and
Vj,
TCP is the data collection period during probe message forwarding mechanism,
FSTVi and
FSTVj are the status transition frequencies of adjacent nodes
Vi and
Vj,
TFViVj is the time-frequency parameter of link connectivity
LViVj, and
FSTmax is the max status transition frequency value obtained during
TCP which is used here for normalization of the sensor node’s
FST. The mobile sink is always in working mode, so
WSINK = 1 and Equation (5) will be become,
Hence, the time-frequency parameter
only depends upon the whole working time and status transition frequency of the sensor nodes. With time-frequency parameter
, we have to calculate the residual energy, remaining buffer size and link quality factor between adjacent nodes. In order to determine the next best hop, we assume that there are N nodes deployed in the NAN, so our link connectivity function
LViVj in terms of
TF, RE, BS, S/N will be:
where
are the contemporary residual energies of node
Vj and
Vi,
are the available buffer size of nodes
Vj and
Vi,
are the link quality factors in terms of signal-to-noise ratio between
Vi and
Vj and
VSINK and
Vi, respectively.
TFViVj is the time-frequency parameter of link connectivity
LViVj,
are the appropriate weights assigned to time-frequency parameter, residual energy, buffer size and link quality factor, respectively. Also, we have considered the residual energy and buffer size of node
Vj only in Equation (7) because node
Vj consumes energy and buffer capacity for both data reception and transmission in accordance with a simplified energy model [
18]. Moreover, illustration of opportunistic connection random graph to understand the link and path connectivity based on asynchronous working–sleeping cycle of adjacent nodes can be seen in
Figure 4.
4.4. Optimal Paths Calculation and Spanning Tree Design
After the construction of OCRG, we need to find the optimal path in EMOR for our sensor node’s data to reach the sink node successfully. In order to establish the optimal path, we need to design a spanning tree algorithm which will help us in determining the maximum value of path connectivity from any sensor node to mobile sink node. Using this algorithm, we will select the optimal multi-disjoint paths for real-time and non-real-time traffic towards mobile sink (NAN gateway) in
Section 4.5.
Path connectivity (PC) depends on the link connectivity of adjacent sensor nodes and is calculated as the product of individual link connectivity values between sensor nodes along the path towards the sink node. The reliability of the data delivery depends on the link connectivity between adjacent sensor nodes and optimal path selection. PC for a path (
Vi,
Vi+t, t) according to
Figure 4 can be formulated in Equation (9) as:
Similarly, the PC for neighboring nodes
Vi of mobile sink node
VSINK will be:
During the construction of the spanning tree, it is pertinent to mention that the nodes whose optimal path are formed already, since they were the neighbors of mobile sink, can help the mobile sink node in getting the optimal paths of intermediate and far-end nodes. Equations (8), (9) and (10) help us in determining the PC of node
Vj to mobile sink. The PC from mobile sink node to an unknown sensor node
Vj depends on 2 factors: (i) PC between mobile sink and its neighboring nodes and (ii) link connectivity between mobile sink’s neighboring node
Vi and unknown sensor node
Vj.
where
is the path connectivity from the mobile sink to neighboring node
Vi. Here we have assumed that
Vj = Vi+t for which
t is the number of hops on the path from
Vi to
Vj and it satisfies the criteria
. In every round of communication (iteration), the mobile sink acquires the updated path connectivity values of intermediate and far-end sensor nodes deployed in the NAN, compares it with the previous PC values, and selects the max PC value. The same process is repeated until mobile sink node receives the updated path and max PC information of all the nodes present in the network.
This spanning tree formation is useful in reducing the overall delay in the network as if the mobile sink needed to explore all the possible paths before selecting the optimal path and determining which one has maximum PC value would have resulted in more delay and a less efficient spanning tree design.
The formation of a spanning tree and optimal path calculation after construction of OCRG can be seen in
Figure 5 and
Table 2. It can be depicted from
Figure 5b that after construction of OCRG, the mobile sink starts the initialization phase by connecting to its immediate neighbors.
Figure 5c shows the path connectivity between the mobile sink and neighbors of the neighbors of mobile sink (i.e., node V
4 and V
5). The process of spanning tree formation continues from
Figure 5d–i based on the optimal path connectivity rule in Algorithm 2. According to the optimal path connectivity rule, we have to choose the maximum values between the current path connectivity value and updated path connectivity value. The optimal path connectivity values for
Figure 5 are given in
Table 2. The initialization step of
Table 2 is synchronized with
Figure 5b where only immediate neighbors are connected to the mobile sink. From steps 1–7, the optimal path connectivity rule is followed to reduce the overall delay in the network.
| Algorithm 2: Optimal Paths Calculation and Spanning Tree Design for Non-Distinguishable Service |
Input:- 1.
Formation of data set D(S,Ns,W/S,FST,RE,BS,S/N) - 2.
Construction of opportunistic connection random graph (OCRG)
Output:- 3.
Optimal path connectivity and spanning tree formation
Begin:- 4.
Determine link connectivity LViVj in terms of TF, RE,BS, S/N of adjacent nodes - 5.
- 6.
Set the path connectivity of VSINK, i.e., - 7.
Determine the path connectivity for neighboring nodes Vi of mobile sink node VSINK - 8.
- 9.
for each awake node Vj in network, do //subroutine_wakeup - 10.
if (Vj is directly connected to neighboring node Vi of mobile sink node VSINK), then - 11.
- 12.
- 13.
elseif (Vj is not directly connected to neighboring nodes Vi of mobile sink node VSINK), then - 14.
- 15.
- 16.
else - 17.
- 18.
end if - 19.
end for - 20.
for each sleeping node Vj in network, do - 21.
if (Vj wakes up); it should send the probe message to mobile sink with updated information - 22.
VSINK should reconstruct OCRG in the next iteration - 23.
subroutine_wakeup: go to 9 //execute steps 9–20 - 24.
end if - 25.
end for - 26.
while (PC from VSINK to entire network is not yet established) - 27.
Select the optimal path using following expression - 28.
- 29.
Update the path from VSINK to Vj - 30.
- 31.
end while
|
After the formation of spanning tree, the mobile sink should broadcast it to the sensor nodes within long radio range Rl in every round of communication. The sensor nodes send the sensing data to mobile sink using this spanning tree information. If a sensor node does not find itself on the spanning tree, it can wait for the next broadcast message from the mobile sink during data collection period and resend its probe message to mobile sink. Upon receiving this probe message, the mobile sink will reconstruct OCRG, re-formulate the spanning tree by re-calculating the optimal path from itself to that node.
4.5. Optimal Multi-Disjoint Path Selection for Real-Time and Non-Real-Time Traffic
We know that the link connectivity function depends on several factors such as time-frequency parameter, residual energy of each neighboring sensor node, remaining buffer size and link quality factor in terms of signal-to-noise ratio. Based on the link connectivity function, we select our next best hop to create an optimal link between sensor node and one of its neighboring nodes, which further results in the optimal path connectivity towards mobile sink node. But this approach just includes the same optimal path for all kinds of data delivery, which will not suit delay-sensitive and delay-tolerant traffic requirements in SGs. Keeping in view the SGs control and monitoring data requirements in NAN, we need to split up our real-time and non-real-time data in such a way that instant priority and an optimal multi-path connectivity should be provided to real-time traffic, whereas for non-real-time traffic, secondary priority should be assigned, and an alternate multi-disjoint path connectivity should be provided.
Therefore, we need to find the next most preferred neighboring node (second best hop) for an alternative multi-disjoint path connectivity of non-real-time traffic. In this way, we can have two-path connectivity:
- (a)
Primary multi-path connectivity for real-time traffic based on first best hop decision criteria in link connectivity function
- (b)
Alternate multi-path connectivity for non-real-time based on second best hop decision criteria in link connectivity function
where is the link connectivity for real-time traffic, is the link connectivity for non-real-time traffic, is the path connectivity for real-time traffic from node Vi to any other node Vi+t and is the path connectivity for non-real-time traffic from node Vi to any other node Vi+t in Equations (15) and (16).
Foregoing in view, the constructed paths are node-disjoint paths which have no rendezvous point except source and destination. Node-disjoint paths are also preferred because they utilize most available network resources while avoiding the bottle necks by keeping energy balance. If an intermediate node fails in a node-disjoint path, only the path containing that failed node will be affected, thus maintaining the diversity of the routes intact with minimum impact. To avoid misuse of energy resources, we limit each sensor node to involve either in first-best hop decision or second-best hop decision, so that no sensor node is involved in constructing paths for both real-time and non-real-time traffic. Algorithm 3 provides details about the multi-disjoint path selection for real-time and non-real-time traffic.
After the construction of multi-disjoint paths, we need to divide our total paths for real-time and non-real-time traffic (i.e., out of N available paths, let us assume that there are
μ paths that correspond to a probability of successfully delivering data to a destination) [
46]. For real-time traffic, we need
τ paths and for non-real-time traffic, we need
ϵ paths, where the total traffic
μ = τ +
. Assuming that the traffic size of real-time and non-real-time data is known, we can easily calculate
τ and
. If
RT represents the real-time traffic size and
NT represents non-real-time traffic size, we can have:
Moreover, the path connectivity from mobile sink
to
for real-time and non-real-time traffic can be expressed in Equations (19) and (20). The path information from mobile sink
to
for real-time and non-real-time traffic can be seen in Equations (21) and (22).
where
t is the hops on the path between node
to
and
t + 1 hops on the path between
to
.
| Algorithm 3: Optimal Multi-Disjoint Paths Selection for Real-Time and Non-Real-Time Traffic (Distinguishable Service) |
Input:- 1.
Formation of data set D(S,Ns,W/S,FST,RE,BS,S/N)
Output:- 2.
Optimal multi-disjoint paths for delay-sensitive and delay-tolerant traffic
Begin:- 3.
for each awake node Vi and Vj in network, do - 4.
Determine LViVj in terms of TF, RE, BS, S/N for first and second best hop decision criteria - 5.
if (delay sensitive traffic is needed), then //real-time data - 6.
- 7.
elseif (delay tolerant traffic is needed), then //non-real-time data - 8.
- 9.
else Link connectivity cannot be established due to status transition (i.e., node sleeping) - 10.
end if - 11.
Determine the path connectivity for both delay-sensitive and delay-tolerant traffic - 12.
if (delay-sensitive traffic is needed), then //real-time data - 13.
- 14.
elseif (delay tolerant traffic is needed), then //non-real-time data - 15.
- 16.
else link and path connectivity failed (i.e., path is no longer available) - 17.
end if - 18.
Formulate real-time and non-real-time paths from total paths μ - 19.
if (delay sensitive traffic is needed), then //real-time data - 20.
total real-time paths will be - 21.
else total non-real-time paths will be - 22.
end if - 23.
Select the optimal path using following expressions - 24.
- 25.
- 26.
end for
|
After the selection of optimal paths for real-time and non-real-time traffic, we need to define our routing strategy for data transmission and reception. The traditional opportunistic node connection routing only includes asynchronous working–sleeping cycle of sensor nodes which could lead to failed link connection sometimes, due to the sleeping mode of any forwarder node. Also, it does not support different type of data requirements in SGs, so in order to resolve this ambiguity, we need energy-efficient multi-disjoint path supporting opportunistic connection routing protocol. Algorithm 4 provide details about our routing strategy for delay sensitive and delay tolerant traffic in EMOR.
| Algorithm 4: Routing Strategy for Delay Sensitive and Delay Tolerant Traffic in EMOR |
Input:- 1.
OCRG, spanning tree formation, optimal path connectivity for distinguishable service
Output:- 2.
Energy efficient routing protocol based on optimal path connectivity for distinguishable service
Begin:- 3.
Assuming that NAN sensing data from node Vm is forwarded to VSINK using optimal path - 4.
When an intermediate node Vr receives the sensing data in NAN: - 5.
if (the successor node Vs of node Vr is in working mode), then - 6.
Forward the sensing data to Vs - 7.
if (Vs knows optimal path towards VSINK in its routing table), then - 8.
Vs receives the sensing data from Vr and forwards the data on optimal path; - 9.
elseif (Vs does not know optimal path towards VSINK in its routing table), then - 10.
if (Vs has neighbors on the spanning tree), then - 11.
for (each working neighbor Vi of Vs node), do - 12.
if (delay sensitive traffic is needed), then - 13.
Calculate for real-time data - 14.
Determine for real-time data based on - 15.
elseif (delay tolerant traffic is needed), then - 16.
Calculate for non-real-time data - 17.
Determine for non-real-time data based on - 18.
end if - 19.
end for - 20.
Select the optimal path using Algorithm 2 and 3 - 21.
elseif (Vs has no neighbors on the spanning tree), then - 22.
Stop forwarding the data - 23.
end if - 24.
end if - 25.
elseif (the successor node Vs of node Vr is sleeping), then - 26.
Search for other neighbors or wait until Vr wakes up - 27.
end if
|
Based on the routing strategy algorithm for delay-sensitive and delay-tolerant traffic in EMOR, the detail process of a source node forwarding its sensed data to the mobile sink can be depicted from
Figure 6. When a random node
Vs receives the data from one of its neighboring nodes, it follows the optimal multi-disjoint path selection for delay sensitive and delay tolerant traffic. Node
V1 receives the delay sensitive traffic as it has the maximum link connectivity with
Vs and node
V2 receives the delay tolerant traffic as it has the second maximum link connectivity value with V
s. During the transmission of delay-sensitive and delay-tolerant traffic in the network, we have to ensure that the nodes can be part of the optimal path towards mobile sink if they offer higher link connectivity. Although the nodes appearing as green in
Figure 6 are working, they do not offer max or second max link connectivity, so they are not part of the delay-sensitive or delay-tolerant traffic paths. Moreover, the nodes appearing as pink in
Figure 6 are sleeping nodes, so they could not be involved in the processes of OCRG, spanning tree, and optimal paths towards mobile sink.
After the path connectivity for delay-sensitive and delay-tolerant traffic is established, we have to update the path connectivity value by comparing the path connectivity value in previous rounds with the path connectivity value in the current round of communication and select the maximum of the two values. In this way, we will be able to acquire the optimal path from any working sensor node to the mobile sink.
7. Conclusions
In this paper, we proposed an energy-efficient multipath opportunistic routing protocol for wireless sensor networks, which can be used in neighborhood area network of smart grids. In this proposed scheme, the mobile sink launches the data collection task anywhere and anytime in the network by broadcasting its SID in the tag message. Upon receiving the tag message, the sensor nodes start formulating their working–sleeping schedule and then forward a probe message to the mobile sink as a response to the tag message. The probe message contains the source information, working–sleeping schedule, and status transition frequency of that sensor node. When the mobile sink receives this probe message, it constructs an opportunistic connection random graph and calculates the optimal path from itself to each sensor node. The optimal path formation is based on the dataset of link connectivity and path connectivity, which includes time-frequency parameter, residual energy, buffer capacity, and link quality factor. After calculation of the optimal path, the first spanning tree is generated in which mobile sink is considered as the root node. Keeping in view the nature of NAN traffic in smart grids, we performed multi-path selection for real-time and non-real-time traffic based on the first and second best possible decisions for link connectivity and path connectivity. The second spanning tree after the selection of real-time and non-real-time path was generated and optimal paths for real-time and non-real-time traffic were calculated. Consequently, we designed the routing protocol based on the optimal paths for real-time and non-real-time traffic of sensor nodes in the spanning tree while focusing on different working–sleeping cycle strategies of sensor nodes.
The possible future work could be incorporation of networks like cloud computing and fog computing with EMOR in which the high computation needs of the mobile sink in the sensor network can be fulfilled using fog computing nodes bridged with cloud. Additionally, the novel concept could be applied to cognitive radio sensor networks to deal with problems like predictive channel assignments and opportunistic spectrum access. Moreover, supervised machine learning techniques can also be used with our proposed scheme to investigate the performance improvements in OCRG and spanning tree formation, predictive changes in the real-time and non-real-time traffic trends (including volumes, faults, power surges, etc.).