1. Introduction
The Wireless Sensor and Actuator Networks (WSAN) are a well-known wireless communication technology with benefits that are becoming significantly important for solving upcoming societies challenges [
1]. The WSAN reliability is strongly affected by unpredictable changes in the environment. A node transmitting always using its maximum power will show a reliability highly immunized to changes in the environment, but the node energy consumption will unnecessarily soar. Thus, a trade-off between energy consumption and communication reliability is required, as proposed in diverse strategies. For instance, in [
2], Kotian
et al. analyze four algorithms for a proactive transmission power control system, where the transmission power is tuned according to link quality predictions. Nodes must interchange information to measure link quality for making predictions. In [
3], Mahmood
et al. provide a survey on reliability protocol schemes based on retransmission and redundancy. For overcoming data loss, the use of data retransmission techniques and data redundancy is proposed, so that the destination can rebuild lost data from extra transmitted information. In [
4], Djemili
et al. propose two algorithms that adjust the node transmission power considering the distance to its two-hop neighbors and to the base station. In [
5], Al-Bzoor
et al. propose an adaptive power control routing protocol for underwater sensor networks. That protocol runs in two phases: first, the base station arranges the network so that nodes are clustered according to their distance to the base station, and second, nodes in a cluster must determine which one has the higher energy to become the cluster gateway to the base station. In [
6], Ning
et al. survey different routing protocols for underwater acoustic sensor networks, focusing on their energy consumption. Summarizing, routing protocols based on node location could reduce energy consumption, compared to those that do not locate neighbors, but increase node memory footprint and processor overhead. Conversely, location-free routing protocols provide worse network latency and increase overall network energy consumption, because of the cooperation among nodes to get network routes to the destination, but are gentle with node computational resources. In [
7], Huang
et al. discuss how to improve network resilience by modifying the network topology and/or the routing protocol. In [
8], Kusy
et al. show how radio diversity improves network reliability though there is a slight increase in the energy consumption. Nodes’ radio transceivers use dual widely-spaced radio frequencies through spatially-separated antennas. That approach only requires new hardware for the node (new radio transceivers and antennas) and does not imply any overload on the node processor or memory, as software or protocols already deployed are not changed. Nevertheless, there is an energy overload of 33%.
In a previous work [
9], we propose a self-adaptive strategy, based on fuzzy control, which adapts each node transmission power to achieve an optimal number of neighbors (an optimal node degree). This optimal number of neighbors guarantees the node a high likelihood to reach any other node in the WSAN and only depends on the parameters of the specific WSAN: the deployment area and the number of nodes per m
2. The node transmission power is dynamically adapted, and thus, the energy consumption is optimized.
Such a self-adaptive strategy was carried out as described in another previous work [
10], where the proposed fuzzy control system running in each node in a WSAN includes two feedback control loops as depicted in
Figure 1. A primary feedback control manages the node transmission power considering both its real and targeted number of neighbors, as mentioned in the previous paragraph. A secondary feedback control loop was added to extend the node battery lifetime by managing the node targeted optimal number of neighbors considering the battery level. Whenever the node battery level drops below a critical value, the targeted number of neighbors is decreased, whereby the node transmission power is reduced and, thus, the node energy consumption.
In some of the above-mentioned related works, improvements in the WSAN energy consumption are carried out by means of new routing protocols, entailing an overload for the network. In others, the node must run algorithms for either making predictions or estimating node locations or distance to other nodes, which might not be accurate in real deployments and involve stressing node computational resources. However, the solution proposed in
Figure 1, deeply described in the following sections, has no significant impact on the performance of existing WSANs, because it requires few extra computational resources in a node, as it implies running very simple algorithms, and does not require data interchange among nodes over the network, whereas the built-in routing protocol in the node provides accurate information about the number of neighbors, no matter the distance.
The rationale for the system in
Figure 1 is available in [
11,
12,
13]. Briefly, the probability of a WSAN being k-connected is the same as the probability of all WSAN nodes having a minimum number of neighbors equals to
k and depends on the number of deployed nodes
n, the node density
ρ, defined as
n/A, where
A is the deployment area, and the nodes’ radio range
r, as shown in Equation (
1).
Thus, for a concrete set of deployment parameters, an optimal number of neighbors for all network nodes can be estimated for guaranteeing that all of them have a good connectivity probability. At this juncture, the node target must be to manage its power transmission accordingly to keep the minimum number of neighbors estimated for its network always, as depicted in
Figure 1, which also considers decreasing a node’s desired number of neighbors to extend its battery lifetime, though the probability of good network connectivity also decreases.
In addition, in [
14], Huang
et al. compare the fuzzy logic controller against other techniques for WSAN topology control, and the results from simulation highlight the fuzzy logic controller benefits. Additionally, in [
15], Huang
et al. compare fuzzy logic controllers obtained through a training dataset and fuzzy logic controllers based on heuristic if-then rules and membership functions. The former are preferred for WSAN deployments that can be accurately described by a mathematical model, and the latter is preferred when no mathematical model is available or accurate enough. For the approach analyzed in this paper, the latter kind of controller has been carried out.
This paper shows the results concerning the WSAN nodes’ connectivity and energy consumption from a real deployment, accomplishing the system in
Figure 1. This paper’s novelty lies in the system simplicity. The approach is very easy to carry out and does not impose significant burdens to being deployed in existing WSANs. However, it includes some uncertainty, as a high probability of getting a k-connected network does not guarantee it is. Besides, the results in this paper come from a real deployment, not from simulations, like in most of the related previous works.
In the following sections, the implemented system’s inner details and its software design are discussed in
Section 2 and
Section 3, respectively.
Section 4 describes the deployed experiments, and
Section 5 analyzes and compares the results from those experiments. Finally,
Section 6 presents the conclusions and depicts future works.
3. System Design
The
Figure 3 depicts the UML (Unified Modeling Language) component diagram for the system in
Figure 1. This figure proposes a general software design for accomplishing self-adaptive systems based on MAPE-K [
16]. It is also based on the one fully described in [
17] customized for the SunSPOT platform, the deployment platform.
The component ORAMediatorForSunSPOT enables the interaction among the rest of the components. It behaves as a broker decoupling observers, triggers, reasoners and actuators. Therefore, all of the components required for the reasoning engine must be previously registered on it. It also provides the observations and actions to either the reasoner or the monitor whenever they are required.
The components
PowerScalingMonitor,
BatteryLevelObservation and
NodeDegreeObservation in
Figure 3 shape the monitoring module in
Figure 1. The components
BatteryLevelObservation and
NodeDegreeObservation measure respectively the battery level and the number of neighbors of a node. The component
PowerScalingMonitor monitors at a specific rate the number of neighbors and the battery level of a node. With the updated values of the sensed parameters, this component then evaluates the rules discussed previously and, if required, triggers the reasoner represented by the
PowerScalingController component. The activity diagram for this component is illustrated in
Figure 4.
The
PowerScalingController component matches the reasoner module from
Figure 1, including both task
TR1 and
TR2. Therefore, it implements the execution of the fuzzy decision-making functions to evaluate the error, either the node degree error
or the battery level error
. The activity diagram for this component is exposed in
Figure 5.
3.1. Neighbor Discovery Protocol
As mentioned in the Introduction section, the node number of neighbors could be usually obtained from the built-in routing protocol. Thus, no extra components are needed for discovering the node neighbors, encouraging this approach to be readily embedded in existing WSAN solutions.
However, that is not the case for the deployment platform that is to be analyzed in this paper. The SunSPOT library provides two routing protocols:
Ad hoc On-demand Distance Vector (AODV) [
18] and Link Quality Routing Protocol (LQRP) [
19]. LQRP is indeed a modified version of AODV, where the next hop in a route is selected by the link quality indicator (LQI) instead of the number of hops. Both of these protocols keep a neighbor list. However, its information is only updated on two occasions:
This is not enough for the purpose of the self-adaptive controller described so far, as the information will not be updated unless a new route discovery is requested.
Therefore, a neighbor discovery protocol has been carried out. This does not replace the built-in routing protocol in the SunSPOT platform. Indeed, both protocols run in parallel.
The neighbor discovery protocol in question is quite simple, conceived just for testing the adaptability of the controller. In any case, there is a whole area of study focused on the exploration of neighbor discovery protocols for wireless sensor networks, either passive, active or both [
20,
21,
22,
23].
The accomplished neighbor discovery protocol is an active three-way one, as shown in
Figure 6. The node that wants to update its neighbor list starts the handshake by broadcasting a NEIGHBOR REQUEST message. The nodes that receive the message issue a unicast NEIGHBOR RESPONSE message. Upon receiving this message, the originating node knows that it is able to reach the responding one and receive the messages, so it can be considered as a neighbor and, thus, added to the list. It then also issues a unicast NEIGHBOR ACK message to acknowledge the other node as a neighbor. At this point, the second node knows that it has been able to reach the originating one, as well as getting its messages. Therefore, it can also be added to its own neighbor list.
The class diagram for the neighbor discovery protocol is illustrated in
Figure 7.
5. Results
5.1. Communication Range Dynamics
A self-adaptive system will try to keep itself in a steady state by executing the necessary actions to achieve its predefined functionality regardless of external perturbations [
33]. The goal of the self-adaptive system is therefore to reduce the impact of the external perturbations, or stimuli, in the normal operation of the system. In our case, the predefined functionality of the proposed fuzzy control-based self-adaptive system is to keep the network connectivity of a wireless sensor network using a probabilistic approach based on the number of neighbors, or node degree, of each node. The only action that a node can do at any iteration of the control loop is to increase or decrease its communication range by means of acting on its own transmission power. We can say then that the system has reached a steady state when there is no change in the transmission power of the node or even when the change is so small and smooth that it keeps the network connectivity over a minimum performance limit.
Thus, to evaluate the performance of the system beyond the energy consumption and the connectivity, as analyzed in [
10], here, we are going to evaluate its dynamical behavior. The dynamical behavior allows us to know how much effort is required for a self-adaptive system to reach its steady state. We can talk then about two main measures: the total number of actions performed by the self-adaptive system during the experiments and how fast it reaches a steady state, expressed as the number of iterations of the control loop required. As described previously, the only action the system does is over the transmission power, so these measurements are calculated just taking into account the changes in the transmission power, as shown in
Figure 10. In any case the dynamics relative to the node degree and the connectivity are also shown in
Figure 11 and
Figure 12, respectively, as they provide additional information of interest.
The figure of merit calculated for the transmission power dynamics is obtained using Equation (20), where
i represents the node and
k the iteration. Therefore, this equation provides us with the total number of actions done on the transmission power for all of the nodes during the running of the experiment.
The results of applying Equation (20) to the obtained data from the experiments is shown in
Table 3.
There are several conclusions we can derive from both the figures and the values listed in
Table 3. The first and easiest thing we can conclude is that Experiment e05 has the best performance regarding the number of actions on the transmission power, as it uses just only 58 changes during the experiment and reaches a good enough connectivity after just six iterations of the control loop, achieving a 92.48% PDR in the seventh iteration. Indeed, as we will see later, the expected delivery rate of this experiment reaches a 99% after the 10th iteration.
Another thing we can observe is that although the dynamics estimation provides interesting information, it has to be considered along with other performance measurements. For instance, Experiment e07 has one of the worst dynamics figures, with 205 changes of the transmission power during the experiment, but it has valid connectivity results, reaching an expected delivery rate of 90% in its 16th iteration, with connectivity values over the 80% PDR from the 10th iteration, as seen in
Figure 12e. The same happens the other way. Experiment e10 has the third best figure for the transmission power dynamics, but due to a bad choice of the configuration parameters, it provides a really bad connectivity, never reaching even an expected delivery of 50% of the messages transmitted, as seen in
Figure 12h.
Thus, we cannot use just the dynamics estimation to evaluate the performance of the system. However, it still provides good complementary information to other performance measurements, like the energy consumption and the connectivity performance explored in [
10]. It also produces other valuable information, like the evidence that the node degree is different for each node even when the network has reached a steady state. This can be observed when comparing
Figure 10c and
Figure 11c. This allows us to reformulate the question proposed in [
34] about the adjustment of the desired node degree for each node according to its location in the network. Moreover, the node degree also changes when there is no change in the transmission power. For instance, in the aforementioned figures, we can observe that there is no change in the transmission power from Round 11 to Round 16 for Experiment e05. However, when observing the same interval for the node degree dynamics, we can see that the node degree changes among rounds. Additionally, this occurs without losing connectivity, as shown in
Figure 12c. Of course, this resilience to the changes in the node degree is due to the use of the tolerance parameter
, but it also illustrates that events external to the nodes affect the node degree. Therefore, the question that remains is if there is another way to solve the unexpected changes in the node degree beyond the use of a tolerance factor.
5.2. Analysis of the Effect of the Parameters on the System’s Performance
Once all of the figures of merit have been obtained, we can analyze the effect of each parameter in the outcome of the fuzzy control-based self-adaptive system. This final analysis is performed applying Equations (21) and (22) to the values obtained in the experiments in correlation to the grouping of the parameters’ set.
For instance, the estimation of the effect of each configuration parameter on the energy consumption, using the figures previously published in [
10], is shown in
Table 4. In our case, each configuration parameter can have two potential values. The
can be either two or three; the
can be zero or one; and the
can be one or three. Therefore, in this case, the first row, corresponding to the parameter level
, shows the sum of the figure
values when the first value of the configuration parameters
,
and
is used, divided by the number of times it is used (in this case, four). The second row shows the same for the second possible value for each configuration parameter. The final row shows the result of applying Equation (22) to the previous rows. The greatest value in this row identifies which parameter has the greatest effect on this figure of merit. In this case, the tolerance represented by
is the parameter that, according to this estimation, has the greatest effect on the energy consumption for the whole network, representing 47.02% of the total estimation of the effect. The
factor represents 36.08%, and the lowest impact on the energy consumption is represented by the
, with 16.90% of the total estimation.
The same procedure is used to estimate the effect of each parameter on the connectivity, using again the figures from [
10], as shown in
Table 5. This time, the configuration parameter more relevant to the connectivity is the scaling factor
, with 61.06% of the total estimation. The next parameter in relevance is the
, with a 37.69% representation. Additionally, the smallest impact on the final result is due to the tolerance parameter
, with 1.24%.
Finally, we make the proper estimation for the dynamics presented in this paper, focusing just on the transmission power dynamics, as that is the only dynamic on which the self-adaptive system acts. The results are shown in
Table 6, and the tolerance represented by
is the parameter that has the greatest impact on the transmission power dynamics, representing 78.57% of the total estimation. Next follows the
parameter with 18.65%, and the smallest impact is caused by the
factor, with 2.78% representation.
As a summary, we can conclude that the parameter is the most relevant for the proposed fuzzy control-based self-adaptive system, being the one with higher impact on the energy consumption and the communication range dynamics, although it has the lowest effect on the connectivity. Indeed, its overall contribution to the system’s performance represents 42.28%, while the parameter contributes with 33.31%, and finally, the parameter contributes with 24.41%.
5.3. Cost Estimation
The cost estimation allows us to evaluate which configuration of the system is better for a given necessity in the explored scenario. Equation (23) represents the cost function used in this analysis, where
and
are the weights assigned to the energy consumption and the connectivity, respectively, and
and
are the normalized values for the figures of merit for the energy consumption and the connectivity obtained in [
10]. This cost estimation does not include the communication range dynamics, as its figures do not show a correlation to the system’s performance, as we have discussed in the previous section.
The normalized values of
and
are obtained using Equation (24), where
x refers to the specific figure, either
e for energy or
c for connectivity, and
y is the experiment for which the estimation is being calculated, while
is the maximum value for the figure of merit for all of the experiments.
Once we have the values for
and
for each experiment, we can just assume that the relation between the weights for the connectivity and the energy consumption follows Equation (25).
Then, we can assign a value from zero to one to the weight for the energy consumption to see how each experiment has behaved. The lowest value of the cost estimation indicates the best performance for the associated weights. Additionally, if we map all of the obtained results for the range assigned to both weights, we will obtain the result shown in
Figure 13. This map represents how well a parameter set fits according to the assigned weights.
The conclusion to the cost estimation is that when the energy consumption is the least relevant condition, up to 45.5% (or the connectivity is the most relevant condition from 54.5%), we should use a fixed transmission power set to the maximum. Additionally, when the energy is the most relevant condition, from 87.8% (or the connectivity is the least relevant condition up to 12.2%), we should still be using a fixed transmission power, but in this case set to a medium value. Additionally, the most important thing, when the energy consumption has a relevance between 45.5% and 87.8%, we should use the fuzzy control-based self-adaptive system with the configuration from Experiment e05. Of course, these results are valid for the experiments we have made. Additionally, they illustrate that there is a range of relevance for either the energy consumption and the connectivity where the use of a self-adaptive system provides better results than using fixed transmission power.
5.4. Additional Conclusions
As
Figure 14 shows, the minimum network energy consumption corresponds to Experiment e01, while the maximum corresponds to Experiment e02. In both cases, the transmission power was set to a fixed value. The first was set to a medium one, and the second to the maximum available one. In
Figure 15, we can compare also the results for the connectivity as an expression of the tendency curves for the packet delivery ratio (PDR) for the whole network as presented in [
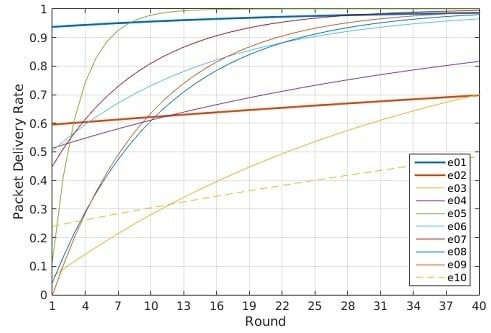
10]. In this case, the situation is reversed: the maximum transmission power, as expected, provides a 99% PDR, while the medium transmission power merely reaches 70% PDR.
Therefore, the use of the self-adaptive transmission power depends on the importance assigned to the energy consumption and the connectivity, as discussed previously regarding the cost estimation. From the experiments performed to evaluate the performance of the proposed self-adaptive system, we know that there is a set of parameters that provides a good performance with low dynamics. In the explored scenario, this corresponds to Experiment e05, where the energy consumption shows an improvement with respect the figures obtained using a fixed transmission power set to the maximum and reaches a 99% PDR in just 11 iterations of the self-adaptive loop.
6. Discussion and Future Works
We have observed in the dynamic results of the system presented in the past section that even in the event of having a steady state regarding the communication range (expressed as no changes in the transmission power), the number of neighbors of each node is not the always the same. For instance, we can observe in
Table 3 and in
Figure 10c that Experiment e05 has the least number of changes in the transmission power of the deployed nodes. Additionally, if we look at
Figure 11c, we will see that the number of neighbors registered in each node is not the same for all of them and also changes frequently. We can guess that this is due to the possible uncontrollable changes in the environment. Therefore, we can make the following proposition:
Proposition 1. In an arbitrarily-deployed wireless sensor network, the node degree that guarantees the network connectivity is unbalanced.
We also have obtained results that show how there are configurations and conditions where the use of the proposed self-adaptive system improves both the connectivity and the energy consumption from the point of view of the whole network.
During the analysis of the system, we have observed other interesting areas where the proposed system can be improved and that we consider worth further exploration.
6.1. Future Works
The performance analysis for the proposed fuzzy control-based self-adaptive system has been done only in an outdoor scenario with just one arbitrary deployment. Other scenarios, either indoor or outdoor, should be explored in further works, including also different deployment schemes. The system’s performance results obtained should then be compared to the results shown in this paper.
Furthermore, in the proposed system, we have relied on the use of fuzzy functions for the decision-making blocks of the controller. These two functions operate in a similar way, as described in the system description: they both use one input and generate one output. It may be of interest to explore the use of more inputs, in particular in the case of the primary loop function of decision making. In this case, we were using the error on the node degree as an input once it has been normalized as . If for instance we add the previous communication range variation rate () as an input, could it be used to help in the reduction of the oscillations? If so, could this eliminate the need for the use of a tolerance value like ?
As we are talking about the functions of decision-making, although we have explored the use of fuzzy logic-based functions, the self-adaptive system is open to the use of any other kind of function or mechanism for this task. For instance, it can be worth exploring the use of genetic and evolutionary algorithms for decision-making [
35], multi-criteria decision-making methods [
36] or any other one. The performance and system impact for these other functions should also be analyzed.
The analysis presented in this paper has also provided a configuration for the parameters of the self-adaptive system that give really good performance results. However, we cannot affirm that this configuration is the best one or even if there is a best one. The use of machine learning techniques to identify the best or the fittest parameter set is also another path for further research. It can also be done taking into account that the configuration can be different for each node in the network, depending on its own context and environmental conditions.
Finally, we have noticed that there are oscillations in the node degree even when there is no change in the transmission power of any node in the network. When this oscillation is within the tolerance parameter, the network can remain in the steady state. However, there is a chance that this oscillation can introduce errors in the system, causing it to enter into an active adaptation cycle. We have considered that these oscillations in the node degree can be due to changes in the environmental conditions. Additionally, these changes cause more oscillations with respect of those nodes that are located in the limit of the communication range of their neighbors. The following subsection proposes an idea of a possible workaround to cope with this problem.
6.1.1. Detailed Description of the Proposal for Further Exploration of the Use of Weighted Links
The proposed fuzzy control-based self-adaptive system has been defined to use the node degree as a reference to make an estimated adjustment of the transmission power in order to achieve a minimum connectivity represented by the expression k-connected. The results analyzed in this paper and already discussed show that the node degree is a value that changes even when there is no change in the network parameters. This happens because some nodes can and usually will be located in a frontier area with respect to a reference node. Thus, a minor change in the environment conditions can cause their connectivity to the reference node to be interment.
Just take a look at
Figure 16a. In this figure, we have depicted a potential scenario. The reference node is labeled as “1”, and a disc communication range approach is used for explaining the theory. There are two discs in the figure. The inner disc represents the area where the connectivity is not affected by the environment. Of course, the quality of the communication can and will vary, but the nodes inside this disc will always appear as neighbors to Node “1”. The outer disc represents the limit of the communication range for Node “1”, and the ring between the inner and the outer discs is the area of the nodes that can be neighbors or not at different times.
If we just use the same probabilistic approach as defined for the system under test, Node “1” can have any number from two to six neighbors at any time. If the and the values are selected, two neighbors are not enough to guarantee the network connectivity; we can assure that there will be iterations of the control loop where the transmission power will be readjusted. Additionally, in a case like the one proposed, a readjustment of the transmission power may not be necessary, or even worse, can introduce new variations on the environment breaking the steady state of the networks.
Therefore, it could be interesting to explore the use of other probabilistic approaches, like considering the quality of the communication of every potential neighbor besides the node degree. For instance, in
Figure 16, we have assigned a value between 0.0 and 1.0 to each potential neighbor. In this example, the value represents the probability that the node will be seen as a neighbor from Node “1”. We can then sum the weights, so we can say that the connectivity quality of the neighborhood for Node “1” is 3.4.