Pravuil: Global Consensus for a United World
Abstract
:1. Introduction
Contributions
- We propose a consensus protocol that remains robust, secure, and scalable among rational participants in an Internet setting;
- We prove liveness, safety, and censorship-resistance of our new consensus protocol;
- We discuss the underlying rationale of our design and prove all the advantages that it provides over previous blockchain designs.
2. Related Literature
3. Model and Methods
- Termination: If a correct party strongly consistently broadcasts m with tag , then all correct parties eventually strongly consistently deliver m with tag .
- Agreement: If two correct parties and strongly consistently deliver m and , respectively, with tag , then .
- Integrity: Every correct party strongly consistently delivers at most one payload m with tag . Moreover, if the sender is correct, then m was previously strongly consistently broadcast by with tag .
- Transferability: After a correct party has strongly consistently delivered m with tag , it can generate a string such that any correct party that has not strongly consistently delivered message with tag is able to strongly consistently deliver some message immediately upon processing .
- Strong unforgeability: For any , it is computationally infeasible to generate a value M that is accepted as valid by the validation algorithm for completing unless correct parties have initialised instance and actively participated in the protocol.
- Improved communication complexity: This reduces the optimistic case to , unlike the Hyperledger Sawtooth PBFT of .
- There is no fork in a blockchain. By running a distributed consensus algorithm, state machine replication is achieved.
- Transactions are confirmed almost instantly. Whenever a transaction is written into a block, the transaction is regarded as valid.
- Transactions are tamper-proof (forward security). Whenever a transaction is written to a blockchain, the transaction and block cannot be tampered with and the block will remain on the chain at all times.
- Anyone can join a node without requiring permission from any party;
- Any node can join or leave at any time;
- The number of participating nodes varies at any time and is unpredictable.
3.1. Prior Consensus Protocols
3.2. Research Design
- A broad literature review about the economic consequences of the technical features used by blockchains and cryptocurrencies leads us to formulate an optimal architecture; detailed teachings distilled from said literature review are detailed in Section 5;
- The optimal architecture is described and implemented in Section 4;
- A controlled experiment simulating a real-world deployment under different configurations is described in Section 6.
4. Resulting Design
4.1. Goals
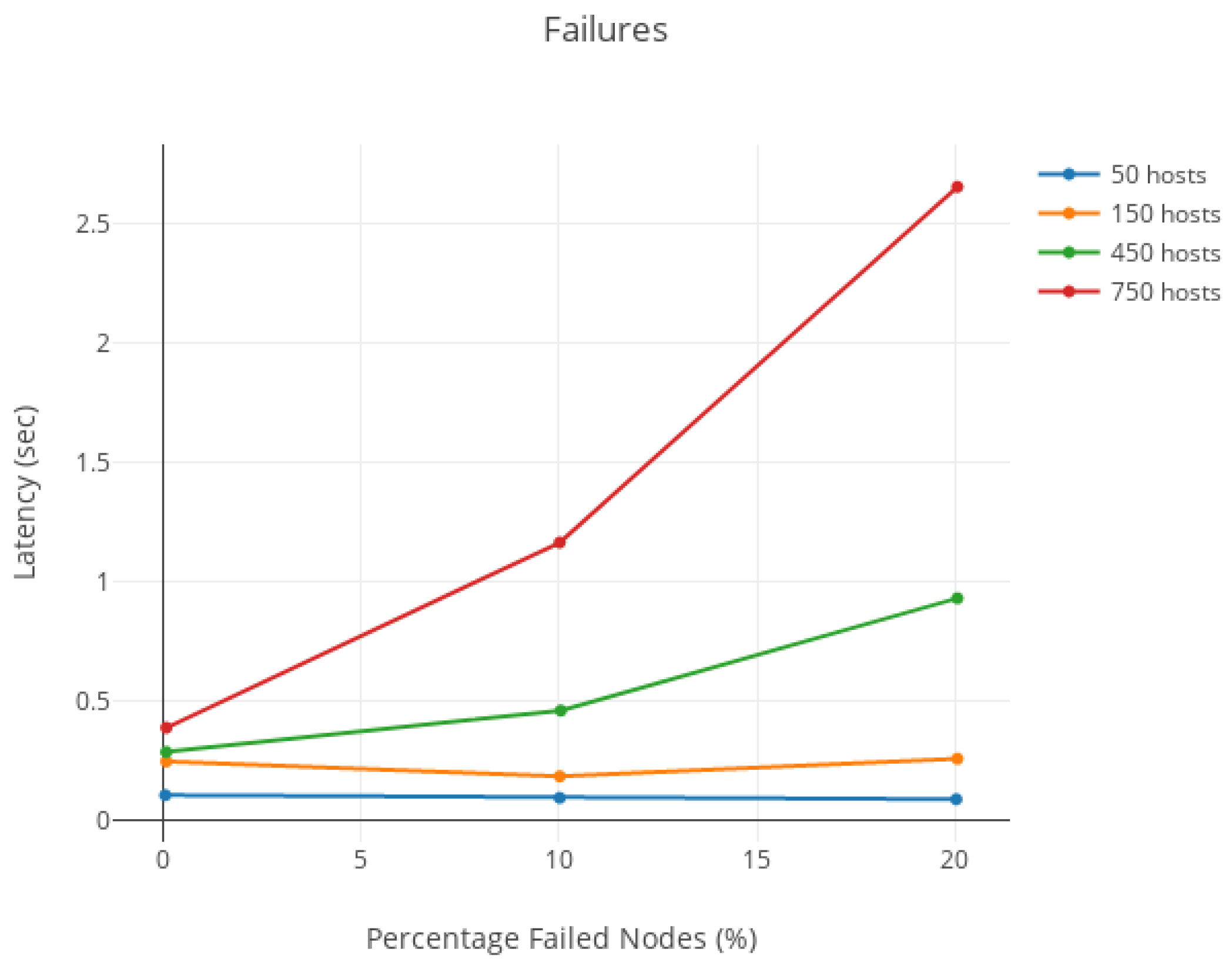
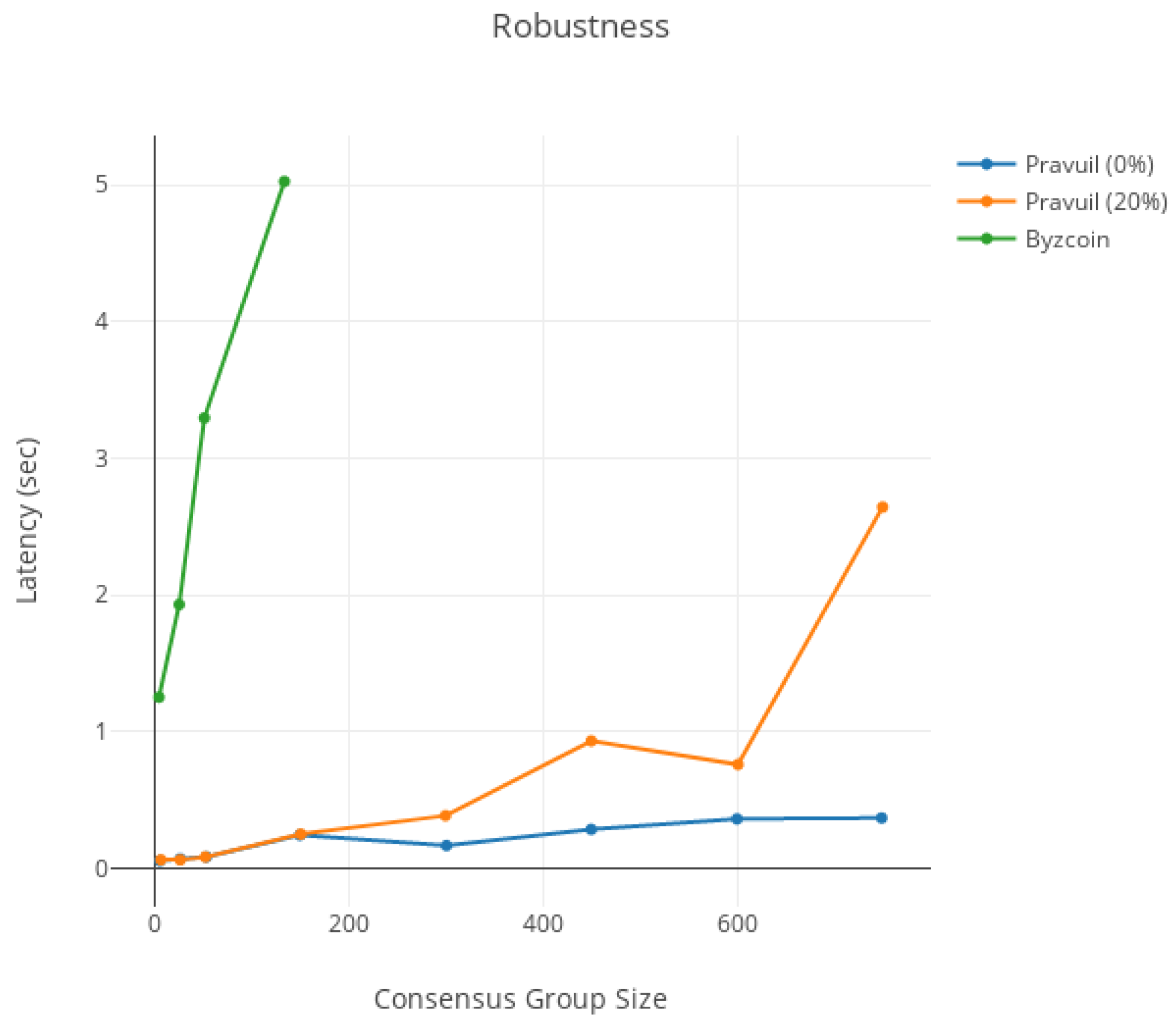
- Robustness: the consensus round can only be disrupted by controlling the leader node.
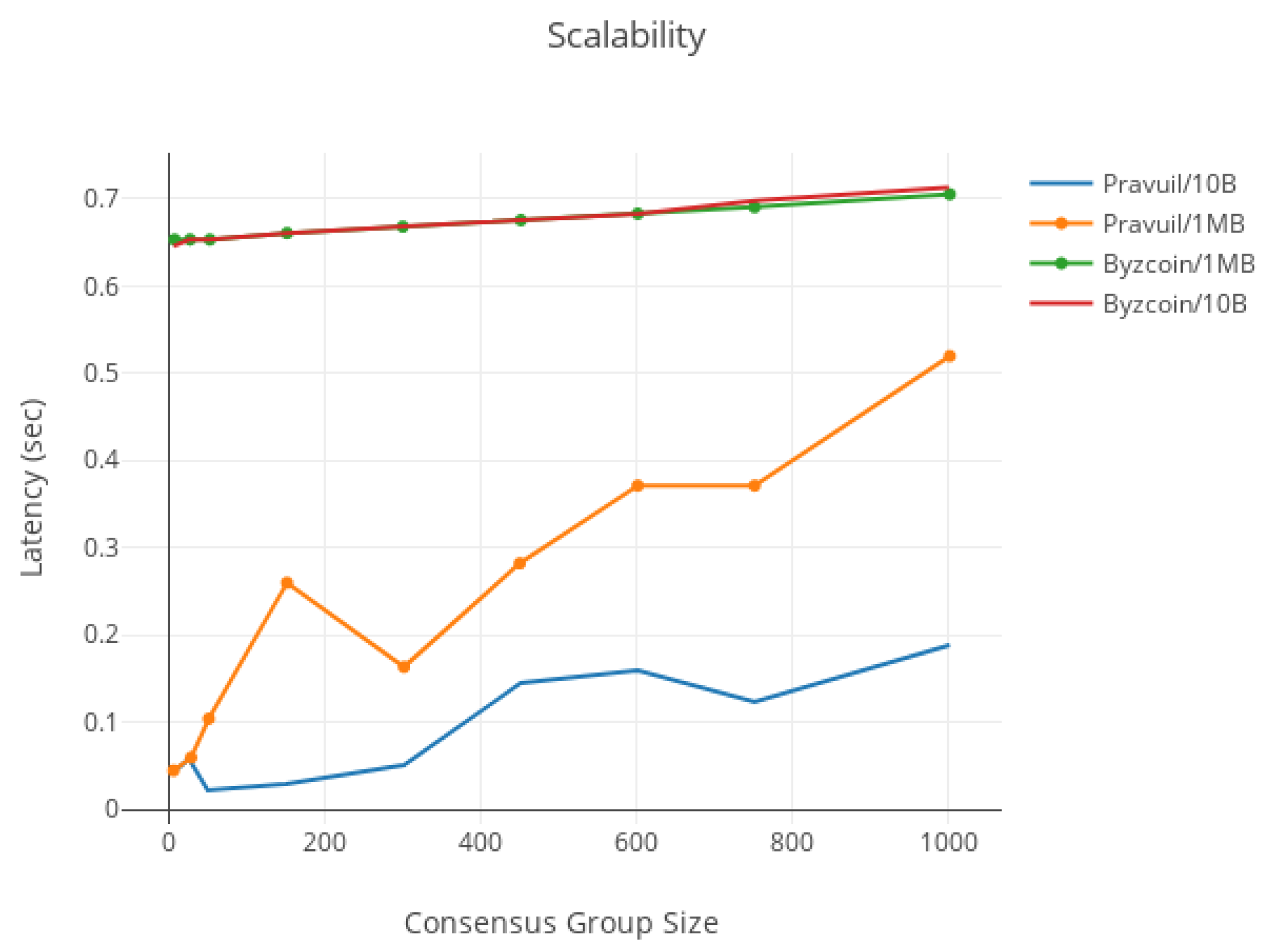
- Scalability: the protocol performs well among hundreds of nodes ().
- Fairness: the malicious leader can only be elected with a probability equal to the percentage of malicious nodes in the system (i.e., the adversary cannot always control the leader).
4.2. Rotating Leader
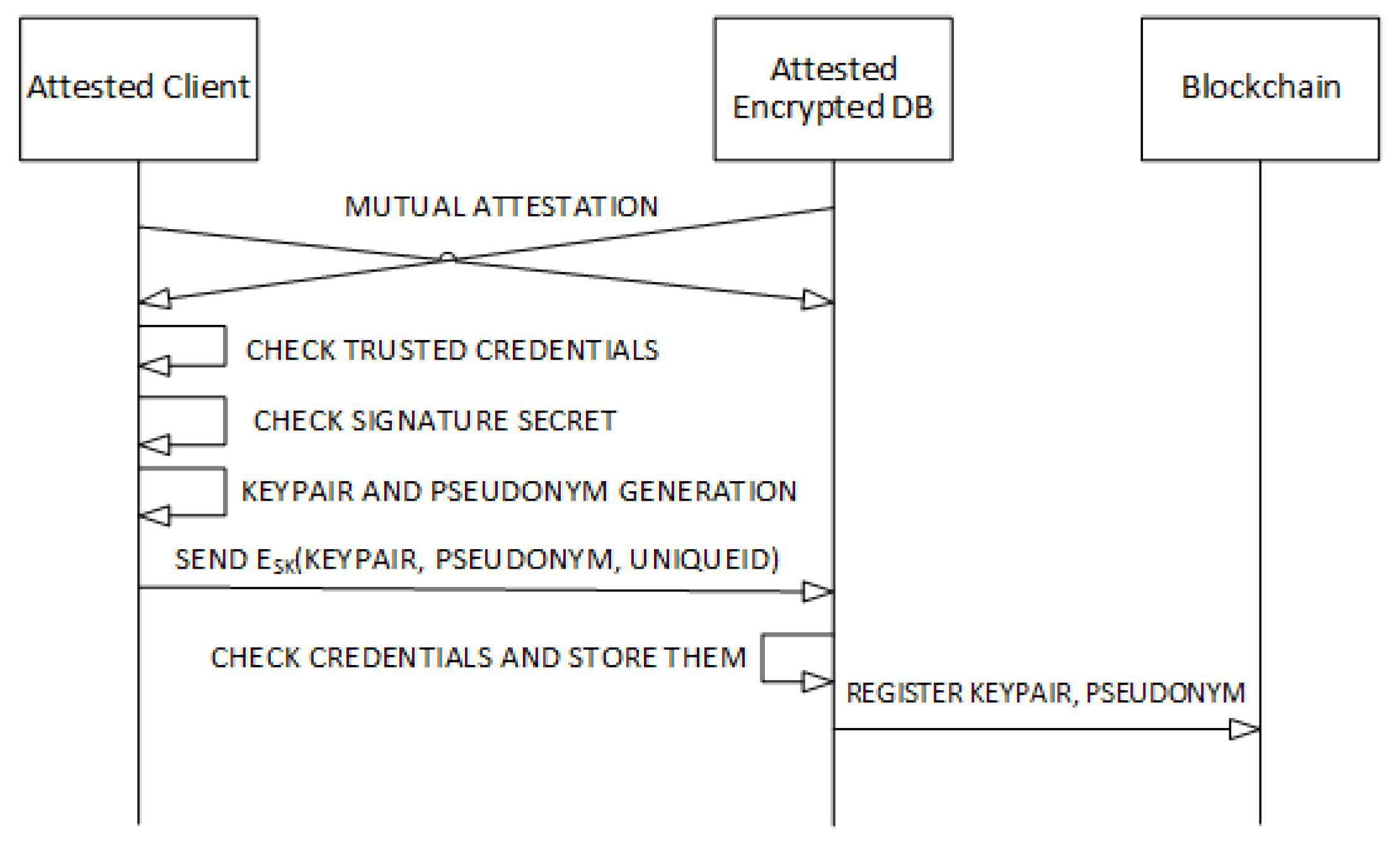
4.3. Zero-Knowledge Proof-of-Identity
| Algorithm 1 Drand’s rotating leader pseudo-code |
NewViewChangeRequest(oldRoster) { nextRoster, time, round = rotateRosterRandomly(oldRoster) return NewViewReq(nextRoster, time, round) } rotateRosterRandomly(roster) { t = time(now) round = drand.RoundAt(t) rnd = drand.Get(round) mod = mod(rnd, length(roster)) return newRoster(roster.List[mod:], roster.List[:mod]), t, round } ViewChangeVerifyRandom(block, request) { nextRoster = rotateRosterRandomVerification(block.Roster, request.time, request.round) if (nextRoster != request.Roster) error(“invalid roster”) if (!request.VerifyUniqueness()) error(“proofs are not unique”) threshold = defaultThreshold(length(block.Roster.List) numsigners = len(request.Proof) if (numsigners < threshold) error(“not enough proofs”) if (!request.VerifySignatures(block.Roster)) error(“couldn’t verify signatures”) } rotateRosterRandomVerification(roster, time, roundBlock) { roundDrand = drand.RoundAt(time) if (roundDrand != roundBlock) error(“different rounds”) rnd = drand.Get(round) mod = mod(rnd, length(roster)) return newRoster(roster.List[mod:], roster.List[:mod]) } |
4.4. Implementation
- A blockchain layer in Go and Java, invoking drand [31] as described in Section 4.2;
- Zero-knowledge proof-of-identity [4] in Python and C;
- Secure smart contracts in Obliv-Java [41].
5. Discussion
5.1. Overcoming Bitcoin’s Limited Adoption Problem
5.2. Obtaining Higher Transaction Security at a Lower Cost
- , a probability that reflects user’s trust in the system;
- , a penalty that could also include legal action.
5.3. An Empirical Approach to Blockchain Design
- Cost: permissionless blockchains are costlier (2.83) than permissioned blockchains (4.84). Please note that a higher cost score means that the blockchain is considered to have better costs (i.e., lower costs), and the ranking obtained from this cost score must be reversed to be useful in the next rankings.
- Performance: permissionless blockchains are less performant (1.88) than permissioned blockchains (4.53).
- Performance/Cost: permissionless blockchains show worse performance regarding cost (0.77) than permissioned blockchains (4.10).
- (Performance*Security)/Cost: permissionless blockchains show worse performance and security regarding cost (2.99) than permissioned blockchains (13.76).
- Security/Cost: permissionless blockchains show worse security regarding cost (1.61) than permissioned blockchains (3).
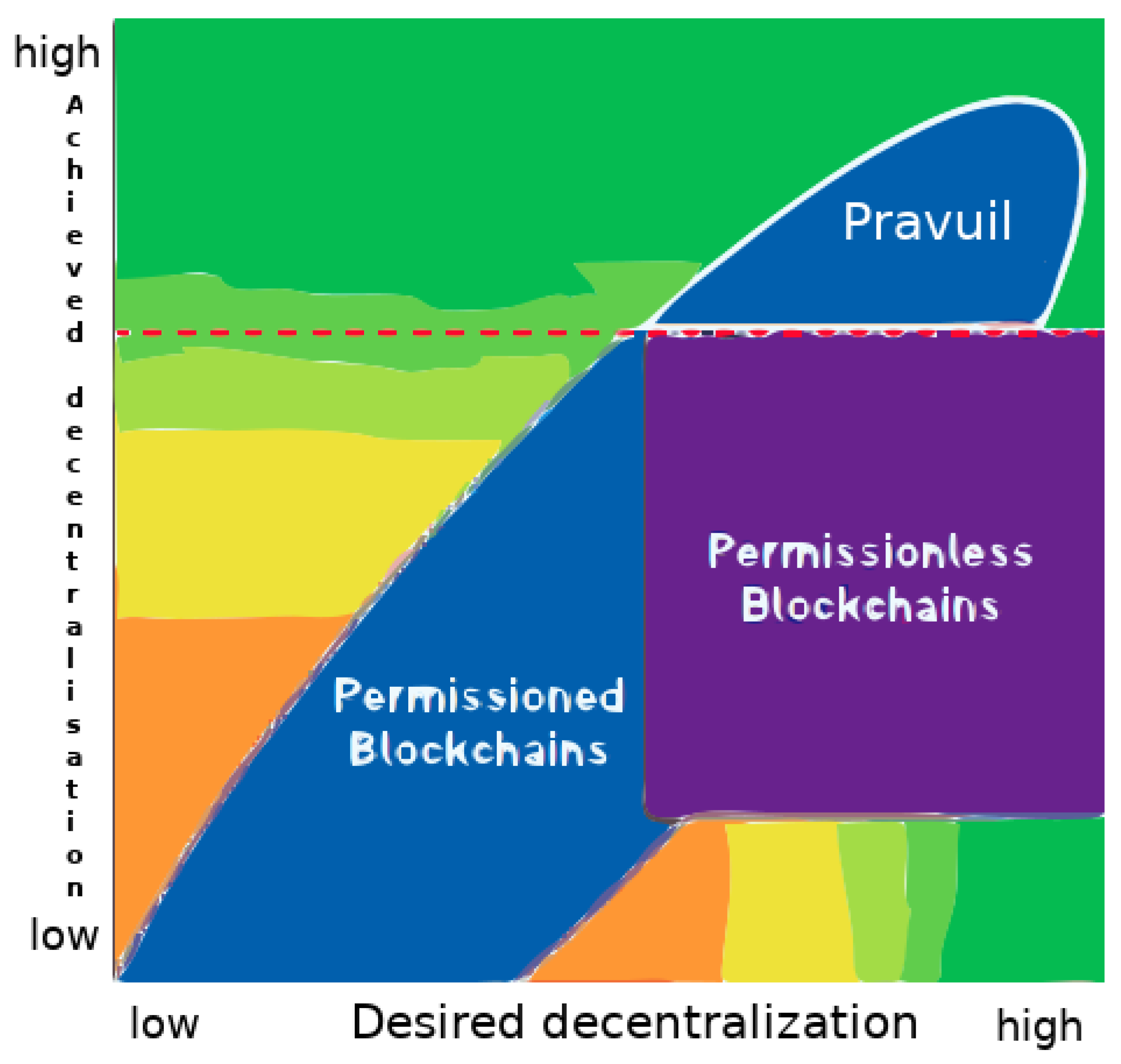
5.4. Achieving More Decentralisation Than Other Permissionless Blockchains
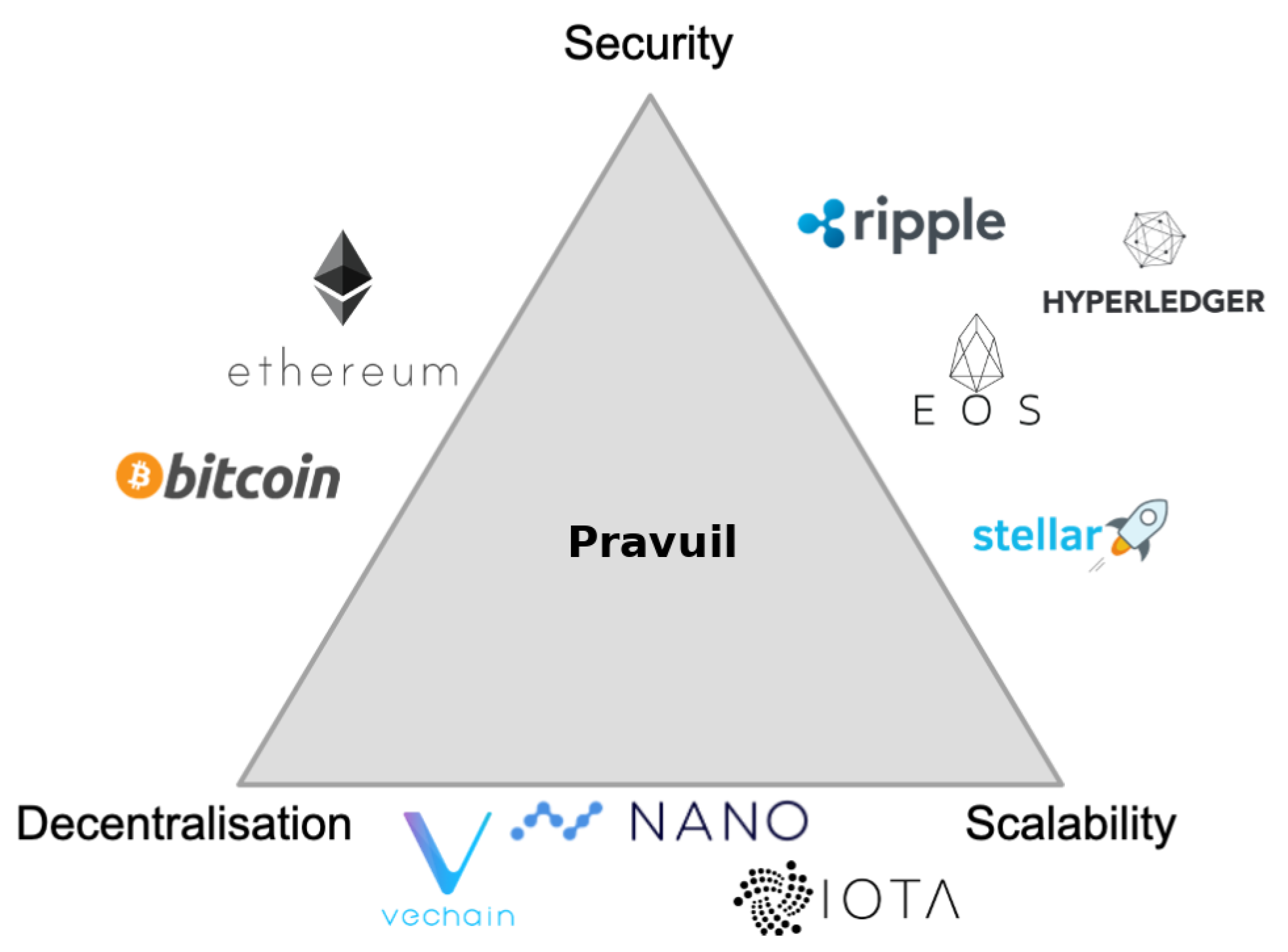
5.5. Overcoming the Scalability Trilemma
- Decentralisation: as discussed previously in Section 5.4, Pravuil can be more decentralised than other permissionless blockchains by using zero-knowledge proof-of-identity, as previously explained in Section 4.3. It also circumvents the impossibility of full decentralisation [4].
- Scalability: Pravuil inherits the scalable rotating-subleader (RS) communication pattern from MOTOR [19], specifically created to avoid the communication bottleneck experienced by classic BFT protocols when run over limited-bandwidth networks.
- Security: Pravuil is secure, as previously proven in Theorems 1 and 2.
5.6. Obviating the Price of Crypto-Anarchy of PoW/PoS Cryptocurrencies
- PoW blockchains: in 2018, Bitcoin, Ethereum, Litecoin, and Monero consumed an average of 17, 7, 7, and 14 MJ, respectively, to generate one USD [45], and in 2021, Bitcoin may have consumed as much energy as all data centres globally [46,47] at 100–130 TWh per year. Holders of cryptocurrency ultimately experience the Price of Crypto-Anarchy as inflation from mining rewards; the next Table 4 compares the yearly mining rewards of some of the top PoW cryptocurrencies and provides estimations of their yearly inflation rates; note that for Ether, the table is only for PoW and before the merge transitioned Ethereum to proof-of-stake (PoS), because although the inflation rate is much lower with PoS (even deflationary), there was not a long enough time series at the time of publication to provide a reliable estimate of the inflation rate.
- PoS blockchains: in theory, the costs are identical to the costs of PoW schemes, except that instead of electrical resources and mining chips, they take the form of illiquid financial resources [11], and in practice, proof-of-stake is not strictly better than proof-of-work, as the distribution of the market shares between both technologies has been shown to be indistinguishable (Appendix 3, [48]).
5.7. Beyond the Economic Limits of Bitcoin
5.8. More Valuable and Stable Cryptocurrencies
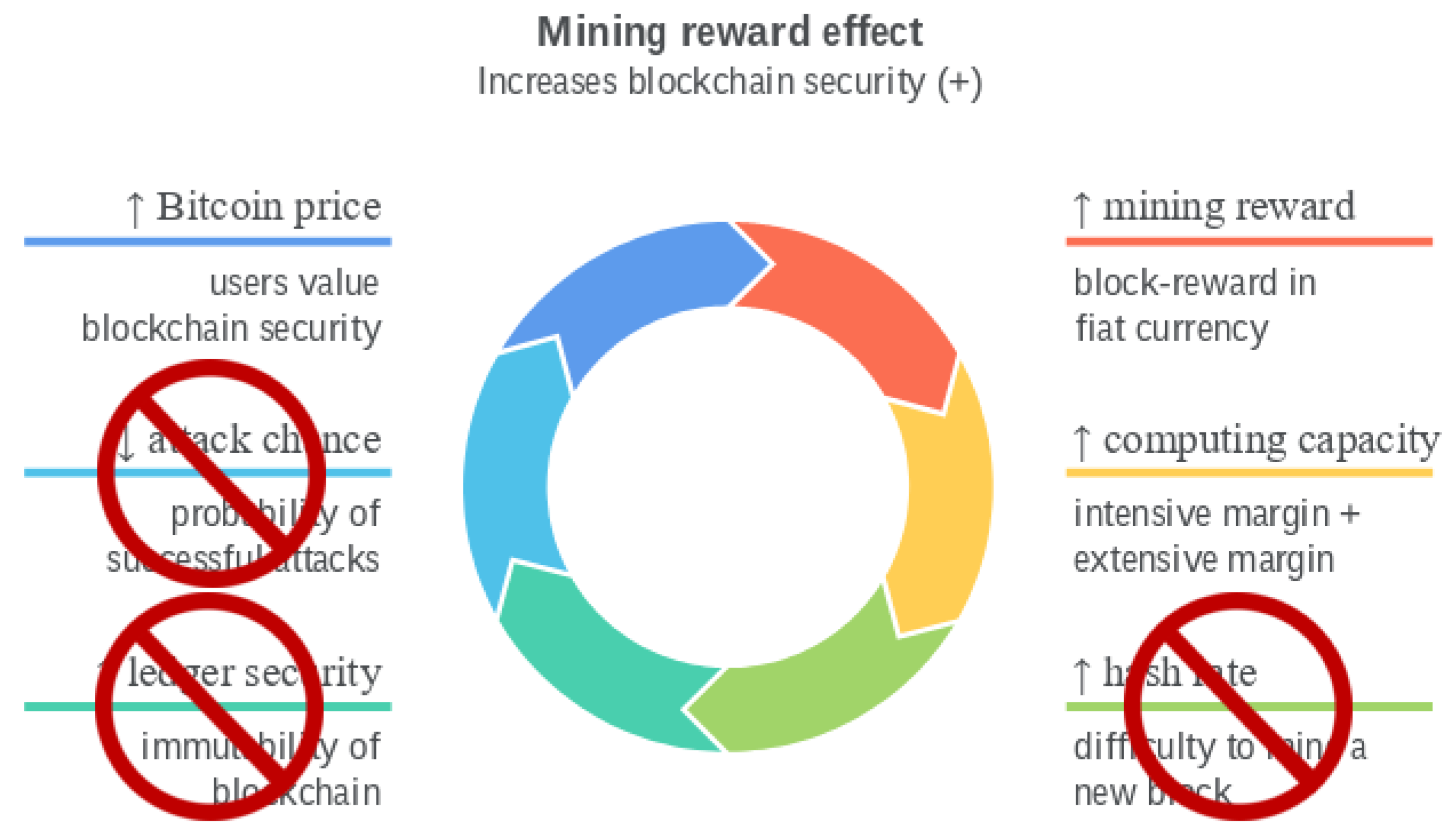
- Bitcoin’s security is sensitive (elastic) to mining rewards and costs, although temporary mining costs and price shocks do not affect the long-run blockchain security [13]; a 1% permanent increase in the mining reward increases the underlying blockchain security by 1.38% to 1.85% in the long-run; positive shocks to electricity prices in China have a negative impact on the hashrate in the short-run; a 1% increase in the efficiency of mining equipment increases the computing capacity between 0.23% and 0.83% in the long-run; in the short-run, mining competition intensity has a statistically positive impact, leading to expansion of mining capacity, but in the long-run, the relationship is reversed.
- High fixed mining rewards are the source of the instability in reaching an equilibrium between miners and users [16]; instead, mining rewards should be adjusted dynamically.
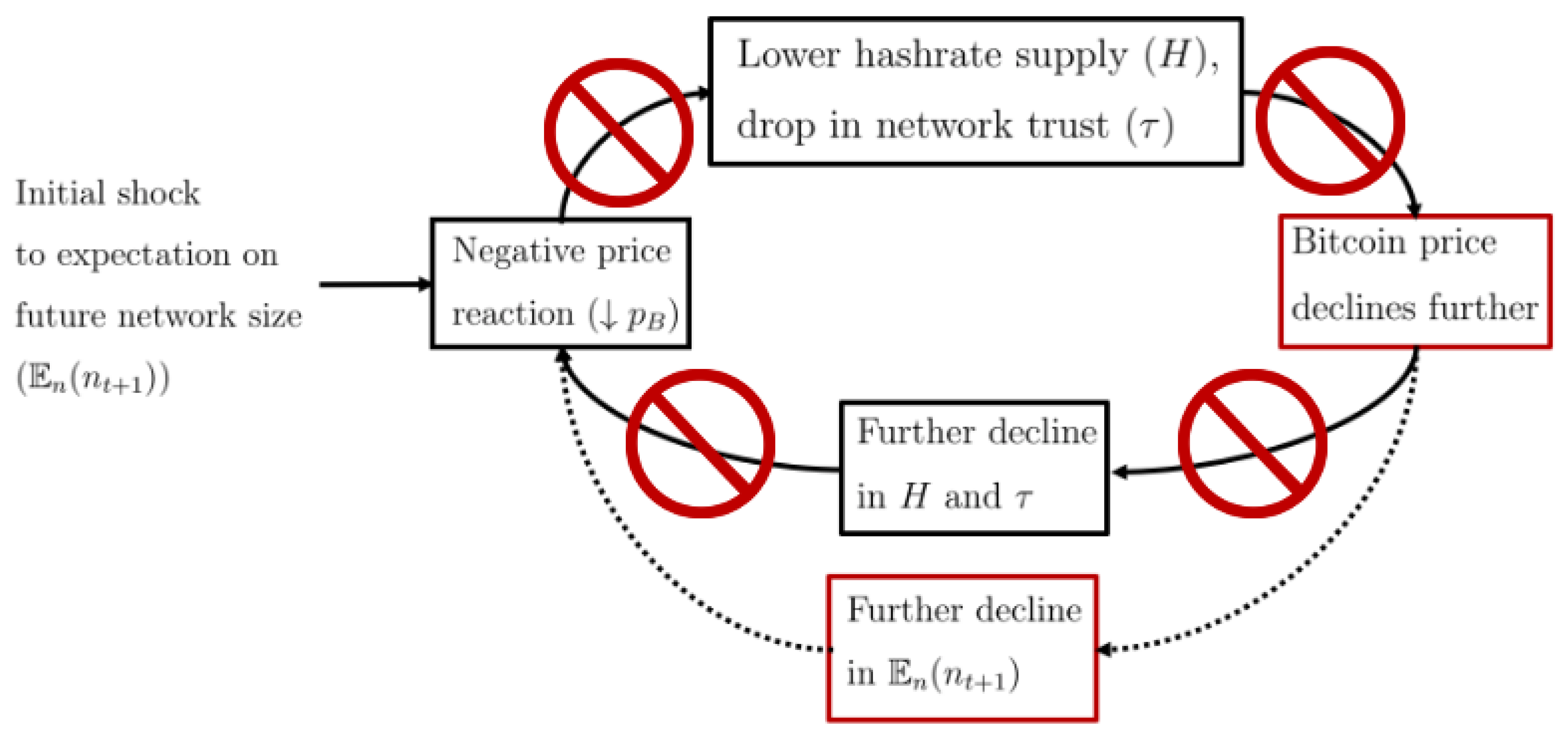
- The production of cryptocurrency by miners is jointly determined by the price used by consumers [15]; the equilibrium price depends on both consumer preferences (i.e., price increases with the average value of censorship aversion and the current and future size of the network) and industrial organisation of the mining market (i.e., price increases with the number of miners and decreases with the marginal cost of mining). Price-security spirals amplify demand and supply shocks: for example, a sudden demand shock provoked by a government banning the cryptocurrency in a country would lead to price drops, leading to miners decreasing hashrate, further decreasing prices, and the feedback loop continues until a new equilibrium is reached in multiple rounds. In other words, Bitcoin’s security model embeds price volatility amplification: indeed, empirical studies [51] find evidence of persistence and long memory volatility in Bitcoin’s market.
- In a PoW blockchain, it is impossible to simultaneously achieve all three following goals [14]: maximise cryptocurrency price, blockchain security, and social welfare.
- Blockchain and transaction security are independent of blockchain mining capacity, mining costs and rewards, and price: once a transaction is instantly committed, it is committed forever;
- There are not price–security spirals for demand and supply shocks: changes in prices do not lead to changes in security;
- As blockchain security is independent of price, it is possible to maximise cryptocurrency price and social welfare.
6. Evaluation
7. Conclusions
- Unpredictably rotating leaders using drand to defend against adversaries and censorship attacks;
Supplementary Materials
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| BFT | Byzantine fault tolerance |
| BLS | Boneh–Lynn–Sacham |
| DKG | distributed key generation |
| FATF | Financial Action Task Force |
| GST | global stabilisation time |
| PKI | public key infrastructure |
| PoI | proof-of-identity |
| PoS | proof-of-stake |
| PoW | proof-of-work |
| SGX | Software Guard eXtensions |
| zk-PoI | zero-knowledge proof-of-identity |
Notations
| Variable | Definition |
| m | message |
| party i | |
| network time bound | |
| n | number of nodes |
| f | faulty nodes |
| d | attacker-controlled nodes |
| network adoption rate | |
| N | number of users |
| V | transaction rate |
| e | exogenous parameter |
| R | block reward |
| x | crypto-to-fiat exchange rate |
| w | block maturation rate |
| f | probability of detecting block replacement |
| permissionless transaction safety upper bound | |
| permissioned transaction safety upper bound | |
| punishment for node i | |
| probability of punishing attacker’s node | |
| expected attacker’s payoff | |
| duration of the attack | |
| = | assignment |
| ∈ | element of |
| ⊆ | subset of |
References
- Garay, J.; Kiayias, A. SoK: A Consensus Taxonomy in the Blockchain Era. In Topics in Cryptology–CT-RSA 2020; Jarecki, S., Ed.; Springer International Publishing: Cham, Switzerland, 2020; pp. 284–318. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, J.; Salles, M.A.V.; Zhang, Z.; Li, T.; Hu, B.; Henglein, F.; Lu, R. Building Blocks of Sharding Blockchain Systems: Concepts, Approaches, and Open Problems. arXiv 2021, arXiv:2102.13364. [Google Scholar] [CrossRef]
- Raikwar, M.; Gligoroski, D.; Kralevska, K. SoK of Used Cryptography in Blockchain. IEEE Access 2019, 7, 148550–148575. [Google Scholar] [CrossRef]
- Cerezo Sánchez, D. Zero-Knowledge Proof-of-Identity: Sybil-Resistant, Anonymous Authentication on Permissionless Blockchains and Incentive Compatible, Strictly Dominant Cryptocurrencies. Cryptology ePrint Archive, Report 2019/546. 2019. Available online: https://eprint.iacr.org/2019/546 (accessed on 2 September 2022).
- Bonneau, J.; Miller, A.; Clark, J.; Narayanan, A.; Kroll, J.A.; Felten, E.W. SoK: Research Perspectives and Challenges for Bitcoin and Cryptocurrencies. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 104–121. [Google Scholar] [CrossRef]
- Garriga, M.; Dalla Palma, S.; Arias, M.; De Renzis, A.; Pareschi, R.; Andrew Tamburri, D. Blockchain and cryptocurrencies: A classification and comparison of architecture drivers. Concurr. Comput. Pract. Exp. 2021, 33, e5992. [Google Scholar] [CrossRef]
- Bakos, Y.; Halaburda, H.; Mueller-Bloch, C. When Permissioned Blockchains Deliver More Decentralization Than Permissionless. Commun. ACM 2021, 64, 20–22. [Google Scholar] [CrossRef]
- Bakos, Y.; Halaburda, H. Tradeoffs in Permissioned vs Permissionless Blockchains: Trust and Performance. 2021. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3789425 (accessed on 2 September 2022).
- Hinzen, F.J.; John, K.; Saleh, F. Bitcoin’s limited adoption problem. J. Financ. Econ. 2022, 144, 347–369. [Google Scholar] [CrossRef]
- Budish, E. The Economic Limits of Bitcoin and the Blockchain. 2018. Available online: https://www.nber.org/system/files/working_papers/w24717/w24717.pdf (accessed on 2 September 2022).
- Gans, J.S.; Gandal, N. More (or Less) Economic Limits of the Blockchain. 2019. Available online: https://www.nber.org/system/files/working_papers/w26534/w26534.pdf (accessed on 2 September 2022).
- Fantazzini, D.; Kolodin, N. Does the Hashrate Affect the Bitcoin Price? J. Risk Financ. Manag. 2020, 13, 263. [Google Scholar] [CrossRef]
- Ciaian, P.; Kancs, d.; Rajcaniova, M. Interdependencies between Mining Costs, Mining Rewards and Blockchain Security. Ann. Econ. Financ. 2021, 22, 1–36. [Google Scholar]
- Pagnotta, E.S. Decentralizing Money: Bitcoin Prices and Blockchain Security. Rev. Financ. Stud. 2021, 35, 866–907. [Google Scholar] [CrossRef]
- Pagnotta, E.; Buraschi, A. An Equilibrium Valuation of Bitcoin and Decentralized Network Assets. 2018. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3142022 (accessed on 2 September 2022).
- Iyidogan, E. An Equilibrium Model of Blockchain-Based Cryptocurrencies. 2018. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3152803 (accessed on 2 September 2022).
- Kokoris-Kogias, E.; Jovanovic, P.; Gailly, N.; Khoffi, I.; Gasser, L.; Ford, B. Enhancing Bitcoin Security and Performance with Strong Consistency via Collective Signing. In Proceedings of the 25th USENIX Conference on Security Symposium, Anaheim, CA, USA, 10–12 August 2016; USENIX Association: Austin, TX, USA, 2016; pp. 279–296. [Google Scholar] [CrossRef]
- Kokoris-Kogias, E.; Jovanovic, P.; Gasser, L.; Gailly, N.; Syta, E.; Ford, B. OmniLedger: A Secure, Scale-Out, Decentralized Ledger via Sharding. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 583–598. [Google Scholar] [CrossRef] [Green Version]
- Kokoris-Kogias, E. Robust and Scalable Consensus for Sharded Distributed Ledgers. Cryptology ePrint Archive, Report 2019/676. 2019. Available online: https://eprint.iacr.org/2019/676 (accessed on 2 September 2022).
- Damgård, I.; Ganesh, C.; Khoshakhlagh, H.; Orlandi, C.; Siniscalchi, L. Balancing Privacy and Accountability in Blockchain Identity Management. In Topics in Cryptology—CT-RSA 2021; Paterson, K.G., Ed.; Springer International Publishing: Cham, Switzerlan, 2021; pp. 552–576. [Google Scholar] [CrossRef]
- Ramasamy, H.V.; Cachin, C. Parsimonious Asynchronous Byzantine-Fault-Tolerant Atomic Broadcast. In Principles of Distributed Systems; Anderson, J.H., Prencipe, G., Wattenhofer, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 88–102. [Google Scholar] [CrossRef]
- Dolev, D.; Dwork, C.; Stockmeyer, L. On the Minimal Synchronism Needed for Distributed Consensus. J. ACM 1987, 34, 77–97. [Google Scholar] [CrossRef]
- Dwork, C.; Lynch, N.; Stockmeyer, L. Consensus in the Presence of Partial Synchrony. J. ACM 1988, 35, 288–323. [Google Scholar] [CrossRef]
- Fischer, M.J.; Lynch, N.A.; Merritt, M. Easy Impossibility Proofs for Distributed Consensus Problems. In Proceedings of the Fourth Annual ACM Symposium on Principles of Distributed Computing, Minaki, ON, Canada, 5–7 August 1985; Association for Computing Machinery: New York, NY, USA, 1985; pp. 59–70. [Google Scholar] [CrossRef]
- Pass, R.; Shi, E. Hybrid Consensus: Efficient Consensus in the Permissionless Model. In Proceedings of the 31st International Symposium on Distributed Computing (DISC 2017), Vienna, Austria, 16–20 October 2017; Richa, A.W., Ed.; Schloss Dagstuhl–Leibniz-Zentrum fuer Informatik: Dagstuhl, Germany, 2017; Volume 91, Leibniz International Proceedings in Informatics (LIPIcs). pp. 39:1–39:16. [Google Scholar] [CrossRef]
- Boneh, D.; Lynn, B.; Shacham, H. Short Signatures from the Weil Pairing. In Advances in Cryptology—ASIACRYPT 2001; Boyd, C., Ed.; Springer: Berlin/Heidelberg, Germany, 2001; pp. 514–532. [Google Scholar] [CrossRef] [Green Version]
- Boneh, D.; Drijvers, M.; Neven, G. Compact Multi-signatures for Smaller Blockchains. In Advances in Cryptology—ASIACRYPT 2018; Peyrin, T., Galbraith, S., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 435–464. [Google Scholar] [CrossRef]
- ICAO. ICAO Public Key Directory (PKD). 2022. Available online: https://www.icao.int/Security/FAL/PKD/Pages/default.aspx (accessed on 2 September 2022).
- Stifter, N.; Judmayer, A.; Schindler, P.; Kern, A.; Fdhila, W. What Is Meant by Permissionless Blockchains? Cryptology ePrint Archive, Report 2021/023. 2021. Available online: https://eprint.iacr.org/2021/023 (accessed on 2 September 2022).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2009. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 2 September 2022).
- DRAND. DRAND. 2021. Available online: https://drand.love (accessed on 2 September 2022).
- DRAND. DRAND Specification. 2021. Available online: https://drand.love/docs/specification (accessed on 2 September 2022).
- Feldman, P. A Practical Scheme for Non-Interactive Verifiable Secret Sharing. In Proceedings of the 28th Annual Symposium on Foundations of Computer Science, Los Angeles, CA, USA, 12–14 October 1987; IEEE Computer Society: New York, NY, USA, 1987; pp. 427–438. [Google Scholar] [CrossRef]
- Gennaro, R.; Jarecki, S.; Krawczyk, H.; Rabin, T. Secure Distributed Key Generation for Discrete-Log Based Cryptosystems. In Advances in Cryptology—EUROCRYPT ’99, International Conference on the Theory and Application of Cryptographic Techniques; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1999; Volume 1592, pp. 295–310. [Google Scholar] [CrossRef] [Green Version]
- Galindo, D.; Liu, J.; Ordean, M.; Wong, J.M. Fully Distributed Verifiable Random Functions and their Application to Decentralised Random Beacons. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy (EuroSP), Vienna, Austria, 6–10 September 2021; pp. 88–102. [Google Scholar] [CrossRef]
- DRAND. DRAND Security Model. 2021. Available online: https://drand.love/docs/security-model (accessed on 2 September 2022).
- King, S.; Nadal, S. PPCoin: Peer-to-Peer Crypto-Currency with Proof-of-Stake. 2012. Available online: https://www.peercoin.net/whitepapers/peercoin-paper.pdf (accessed on 2 September 2022).
- Rajab, T.; Manshaei, M.H.; Dakhilalian, M.; Jadliwala, M.; Rahman, M.A. On the Feasibility of Sybil Attacks in Shard-Based Permissionless Blockchains. arXiv 2020, arXiv:2002.06531. [Google Scholar]
- Hafid, A.; Hafid, A.; Samih, M. A Tractable Probabilistic Approach to Analyze Sybil Attacks in Sharding-Based Blockchain Protocols. IEEE Trans. Emerg. Top. Comput. 2022. [Google Scholar] [CrossRef]
- Cerezo Sánchez, D. Updates to Worldwide Coverage. 2022. Available online: https://www.calctopia.com/category/coverage/ (accessed on 2 September 2022).
- Cerezo Sánchez, D. Raziel: Private and Verifiable Smart Contracts on Blockchains. Cryptology ePrint Archive, Report 2017/878. 2017. Available online: https://eprint.iacr.org/2017/878 (accessed on 2 September 2022).
- Shanaev, S.; Shuraeva, A.; Vasenin, M.; Kuznetsov, M. Cryptocurrency Value and 51% Attacks: Evidence from Event Studies. J. Altern. Invest. Winter 2020. [Google Scholar] [CrossRef]
- Gencer, A.E.; Basu, S.; Eyal, I.; van Renesse, R.; Sirer, E.G. Decentralization in Bitcoin and Ethereum Networks. In Financial Cryptography and Data Security; Meiklejohn, S., Sako, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2018; pp. 439–457. [Google Scholar] [CrossRef] [Green Version]
- Douceur, J. The Sybil Attack. In Proceedings of the 1st International Workshop on Peer-to-Peer Systems (IPTPS), Cambridge, MA, USA, 7–8 March 2002. [Google Scholar] [CrossRef]
- Krause, M.J.; Tolaymat, T. Quantification of energy and carbon costs for mining cryptocurrencies. Nat. Sustain. 2018, 1, 711–718. [Google Scholar] [CrossRef]
- Digiconomist. Bitcoin May Consume as Much Energy as All Data Centers Globally. 2021. Available online: https://digiconomist.net/bitcoin-may-consume-as-much-energy-as-all-data-centers-globally (accessed on 2 September 2022).
- de Vries, A. Bitcoin Boom: What Rising Prices Mean for the Network’s Energy Consumption. Joule 2021, 5, 509–513. [Google Scholar] [CrossRef]
- ElBahrawy, A.; Alessandretti, L.; Kandler, A.; Pastor-Satorras, R.; Baronchelli, A. Evolutionary dynamics of the cryptocurrency market. R. Soc. Open Sci. 2017, 4, 170623. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Georgoula, I.; Pournarakis, D.; Bilanakos, C.; Sotiropoulos, D.; Giaglis, G.M. Using Time-Series and Sentiment Analysis to Detect the Determinants of Bitcoin Prices. MCIS 2015 PROCEEDINGS. 2015. Available online: https://aisel.aisnet.org/mcis2015/20 (accessed on 2 September 2022).
- Hayes, A.S. Cryptocurrency value formation: An empirical study leading to a cost of production model for valuing bitcoin. Telemat. Inf. 2016, 34, 1308–1321. [Google Scholar] [CrossRef]
- Bouri, E.; Gil-Alana, L.A.; Gupta, R.; Roubaud, D. Modelling long memory volatility in the Bitcoin market: Evidence of persistence and structural breaks. Int. J. Financ. Econ. 2019, 24, 412–426. [Google Scholar] [CrossRef] [Green Version]
- Kovtun, V.; Izonin, I.; Greguš, M. Model of Information System Communication in Aggressive Cyberspace: Reliability, Functional Safety, Economics. IEEE Access 2022, 10, 31494–31502. [Google Scholar] [CrossRef]

| Features | Bitcoin | ByzCoin/MOTOR | Pravuil |
|---|---|---|---|
| Secure | ✓ | ✓ | ✓ |
| Decentralised | ✓ | ✓ | ✓ |
| Scalability | ⊠ | ✓ | ✓ |
| Real-world identity | ⊠ | ⊠ | ✓ |
| Free Sybil resistance | ⊠ | ⊠ | ✓ |
| Lawfulness | ⊠ | ⊠ | ✓ |
| Unlimited adoption | ⊠ | ⊠ | ✓ |
| No economic limitation | ⊠ | ⊠ | ✓ |
| Features | BTC | ETH | BCH | LTC | ADA | USDT | Mean |
|---|---|---|---|---|---|---|---|
| Popularity | 1 | 2 | 3 | 7 | 8 | 9 | |
| Cost | 1.33 | 2 | 1.66 | 2.66 | 4.33 | 5 | 2.83 (*) |
| Consistency | 1.33 | 2.33 | 1.33 | 2 | 3.66 | 1 | |
| Functionality | 2 | 5 | 2 | 2 | 4.33 | 2 | |
| Performance | 1.33 | 1.66 | 2 | 2.33 | 3 | 1 | 1.88 (*) |
| Security | 4 | 4 | 4 | 4 | 4 | 3.33 | 3.88 |
| Decentralisation | 5 | 3.33 | 4.33 | 3.66 | 3.33 | 1.33 | |
| Total | 14.99 | 18.32 | 15.32 | 16.7 | 22.65 | 13.66 | |
| Performance/Cost | 0.28 | 0.41 | 0.46 | 0.7 | 1.79 | 1 | 0.77 (*) |
| (Perf*Sec)/Cost | 1.13 | 1.66 | 1.84 | 2.79 | 7.18 | 3.33 | 2.99 (*) |
| Security/Cost | 0.85 | 1 | 0.92 | 1.2 | 2.39 | 3.33 | 1.61 (*) |
| Features | XRP | EOS | XLM | TRX | MIOTA | Mean |
|---|---|---|---|---|---|---|
| Popularity | 3 | 5 | 6 | 11 | 10 | |
| Cost | 4.66 | 5 | 4.66 | 5 | 5 | 4.84 (*) |
| Consistency | 4.33 | 5 | 4 | 4 | 4.66 | |
| Functionality | 1.33 | 5 | 1.33 | 5 | 3.66 | 4.53 (*) |
| Performance | 4.33 | 4.66 | 4 | 4.66 | 5 | 3.33 |
| Security | 2.33 | 3.33 | 4 | 3.33 | 3.66 | |
| Decentralisation | 1 | 2.66 | 2.33 | 3.33 | 2.33 | |
| Total | 17.98 | 25.65 | 20.32 | 25.32 | 24.31 | |
| Performance/Cost | 3.23 | 4.66 | 2.98 | 4.66 | 5 | 4.10 (*) |
| (Perf*Sec)/Cost | 7.52 | 15.51 | 11.94 | 15.51 | 18.3 | 13.76 (*) |
| Security/Cost | 1.73 | 3.33 | 2.98 | 3.33 | 3.66 | 3 (*) |
| Name | Reward per Block | Block Time | Blocks per Day | Price | Yearly Mining Reward | Yearly Inflation |
|---|---|---|---|---|---|---|
| BTC | 6.25 | 10 m | 144 | $50,000 | $18,061 B | 4.12% |
| ETH | 2 | 13.2 s | 6545 | $3780 | $16,425 B | 1.76% |
| DOGE | 10,000 | 1 m | 1440 | $0.49 | $2575 B | 4.06% |
| LTC | 12.5 | 2.5 m | 576 | $320 | $840 MM | 3.94% |
| BCH | 6.25 | 10 m | 144 | $1275 | $418 MM | 1.75% |
| ZEC | 3.125 | 75 s | 1152 | $301 | $395 MM | 11.84% |
| XMR | 1.02 | 2 m | 720 | $407 | $109 MM | 1.5% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cerezo Sánchez, D. Pravuil: Global Consensus for a United World. FinTech 2022, 1, 325-344. https://doi.org/10.3390/fintech1040025
Cerezo Sánchez D. Pravuil: Global Consensus for a United World. FinTech. 2022; 1(4):325-344. https://doi.org/10.3390/fintech1040025
Chicago/Turabian StyleCerezo Sánchez, David. 2022. "Pravuil: Global Consensus for a United World" FinTech 1, no. 4: 325-344. https://doi.org/10.3390/fintech1040025




